
Kaspersky offers various services to organizations that have been targeted by cyberattackers, such as incident response, digital forensics, and malware analysis. In our annual incident response report, we share information about the attacks that we investigated during the reporting period. Data provided in this report comes from our daily interactions with organizations seeking assistance with full-blown incident response or complementary expert services for their internal incident response teams.
Download the full version of the report (PDF)
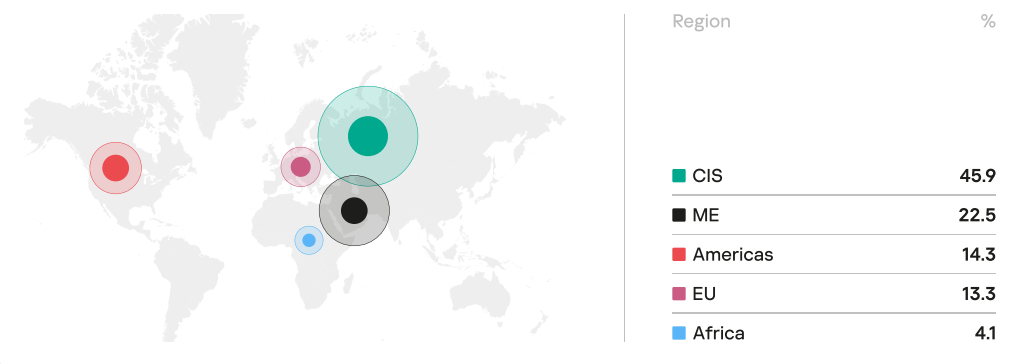
Kaspersky Incident Response in various regions and industries
In 2022, 45.9% of organizations that encountered cyberincidents were in Russia and the CIS region, followed by the Middle East (22.5%), the Americas (14.3%), and Europe (13.3%).
From an industry perspective, we offered help to government (19.39%), financial (18.37%), and industrial (17.35%) organizations most frequently.
Key trends in 2022: initial attack vectors and impact
In 2022, attackers most often penetrated organizations’ infrastructure by exploiting various vulnerabilities in public-facing applications (42.9%). However, compared to 2021, the share of this initial attack vector decreased by 10.7 pp, while the share of attacks involving compromised accounts (23.8%) grew. Malicious e-mail sharing among the initial attack vectors continued to go down and comprised 11.9% in 2022.
In 39.8% cases the reported incidents were related to ransomware attacks. Encrypted data remains the number-one problem that our customers are faced with. However, compared to 2021, the number of ransomware-related incidents dropped, and not every attack involving file encryption was aimed at extracting a ransom. In some of these incidents, ransomware was used to hide the initial traces of the attack and complicate the investigation.
Expert recommendations
To protect your organization against cyberattacks, Kaspersky experts recommend the following:
- Implement a robust password policy and enforce multifactor authentication
- Remove management ports from public access
- Establish a zero-tolerance policy for patch management or compensation measures for public-facing applications
- Make sure that your employees maintain a high level of security awareness
- Use a security toolstack with EDR-like telemetry
- Implement rules for detection of pervasive tools used by adversaries
- Continuously train your incident response and security operations teams to maintain their expertise and stay up to speed with the changing threat landscape
- Back up your data on a regular basis
- Work with an Incident Response Retainer partner to address incidents with fast SLAs
To learn more about incident response in 2022, including a MITRE ATT&CK tactics and techniques heatmap, and distribution of various incidents by region and industry, download the full version of the report (PDF).
For a deeper analysis of the vulnerabilities most commonly exploited by cyberattackers, download this appendix (PDF).
The nature of cyberincidents in 2022





















Walter Ag
Could send me , stadistics of DDoS in Argentine (since 2022). I am profesor and leader of varius investigation about: Detect DDoS using IA in network SDN too need trafic with DDoS for training my IA.
It coud be?
Thanks