- Part 1. How to mitigate APTs. Applied theory
- Part 2. Top-4 mitigation strategies which address 85% of threats
- Part 3. Strategies outside the Top-4. For real bulletproof defense
- Part 4. Forewarned is Forearmed: the Detection Strategy against Advanced Persistent Threats (APTs)
Part 4. Forewarned is Forearmed: the Detection Strategy against Advanced Persistent Threats (APTs)
Already existing Kaspersky Lab products could considerably mitigate1 enterprise’s possible losses because of APTs. Specialized security solutions for warning about targeted attacks are additional featured layer of organization’s defense. Such warnings are not a replacement for IT-infrastructure security solutions that stops malicious APT’s modules. Anti-APT system’s role is to control the IT-environment and to give all valuable information to security officer. It seriously increases general multi-layered enterprise’s defense.
In any targeted attack’s elaboration we can distinguish the sequence of the typical stages. Also standard techniques are applied in overwhelming majority of cases. These indications are a starting point for potential victims’ warning in proper time. In most cases APT’s uniqueness isn’t a matter of modules unusualness. It’s an efficient consolidation of typical components, that reliably solve their purposes. Knowledge about general principles of malefactor’s work helps to successfully counteract the targeted attacks.
In this document we’ll describe Kaspersky Lab’s vision of high-quality specialized Anti-APT security solution. As a targeted attack’s sample we’ll take one of the famous nowadays APT – Dark Hotel2. This carefully designed serious attack as many before (Careto, NetTraveler, Red October)3 was discovered by Kaspersky Lab’s experts.
Typical APT stages
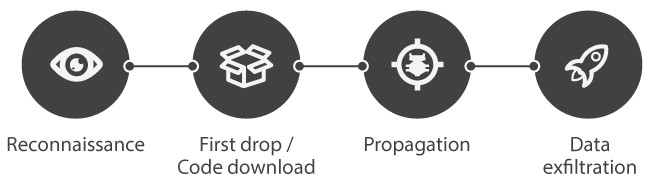
Illustration 1. APT’s elaboration stages
Any targeted attack begins with reconnaissance. During this preliminary stage APT’s authors obtain information, for example, about victim company’s key employees that have access to the valuable data; about what kind of e-mail may cause interest of these men; whenever possible malefactors get a foretaste of victim’s IT-infrastructure, etc. In most cases such preliminary work is carried out not by technical means and it’s next to impossible to notice it with any kind of software only. Rather, we can talk here about counter-espionage and overall quality of security department.
After these preliminary steps technical stages of attack begin at once. First of all, violator needs to get rights for code execution inside company’s security perimeter. Exploits are used very actively on this stage. It’s a name for a small program code, which exploits operating systems or popular software vulnerabilities on the target PCs. In the case of success violators could execute their own code, which downloads and executes main modules of attack.
Final stage is the main target of the whole attack: undetected enterprise’s data collection and sending it to the malefactors. First APT modules have to spread in the company’s security perimeter for it. Strategy of such spreading can significantly vary. Some targeted attack’s authors aim to infect as much PCs inside perimeter as possible. Both containing the desired data itself and auxiliary PCs, only as a step for further spreading and one more step to the data. Other malefactors try to restrict APT activity only with necessary devices, trying to decrease the probability of revelation that way.
At last, let us note that malicious modules developers are trying to make their software resistant to removal attempts. Modules tries to survive and don’t require a reiteration of first attack’s stages for recovery. All the stages above in text and on illustration below have its indicators and can be revealed by specialized security software.
Dark Hotel features
From common widespread tactics Dark Hotel uses standard spear-phishing. Such method along with waterholing (popular web-sites infection) is the most widespread start of a targeted attack. The reason for this choice is the methods relative simplicity and potential exposure to it of any company, in which employees use web and e-mail. Comprehensive security systems have to take such popularity into account and cut off these tactics both on the endpoint level and during the network traffic filtering.
Mentioned standard effective methods don’t interfere malefactors to add some interesting features into their specific attacks. Dark Hotel simultaneously uses one distinctive infection technique. Thanks to it this APT received its name.
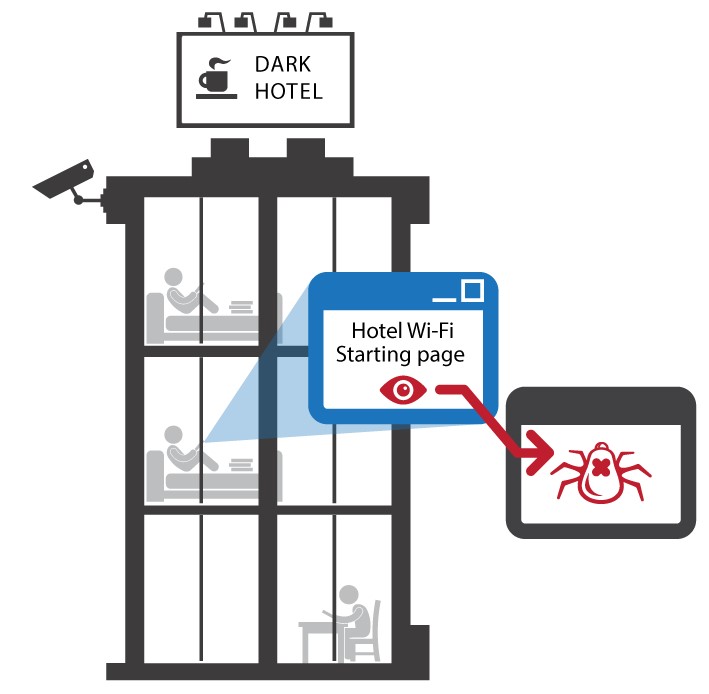
Illustration 2. Dark Hotel, attack outside the company’s security perimeter
During preliminary reconnaissance stage attackers use to know in advance about arrival of the guests with the necessary information. Technically it’s the hotels IT-infrastructure vulnerability that allow them to begin the attack at the guests PCs. Malefactors choose business class hotels for this precise targeted attack. Operation begins from starting page, which every lodger sees in his browser after going into web through hotel Wi-Fi.
In contrast to spearphishing and waterholing this hotel technique obviously requires long and far from cheap preparation on reconnaissance stage, but then the findings on the precise chosen victims PC’s can be extremely valuable. It’s significant to note that in this infection scenario victim is out of the company’s security perimeter. For a comprehensive multilayered defense from APTs it’s crucial to remember about this kind of scenario and install simultaneously local security systems on the employee’s devices. Then local security installations would inform security officer (Anti-APT agent) and would stop malicious modules execution (endpoint protection).
Solution architecture
It takes time to analyze objects in incoming traffic. In blocking mode specialized Anti-APT solution will significally delay download of e-mail attachments and files through HTTP. Hence we consider that solution should work in the warning mode. Security officer receives all needed data through his management console. Anti-APT software’s role is to register all necessary events and to help in incident analysis, but not to block the programs execution. Endpoint protection is responsible for blocking of malicious modules in proper time. In case of Kaspersky Lab for corporate customers it’s Kaspersky Endpoint Security (KES)4.
Correctly selected amount of data for security officer is crucial. It have to be enough for quality analysis, but in the same time endless alerts about potential threat and unnecessary data shouldn’t interfere information security employee.
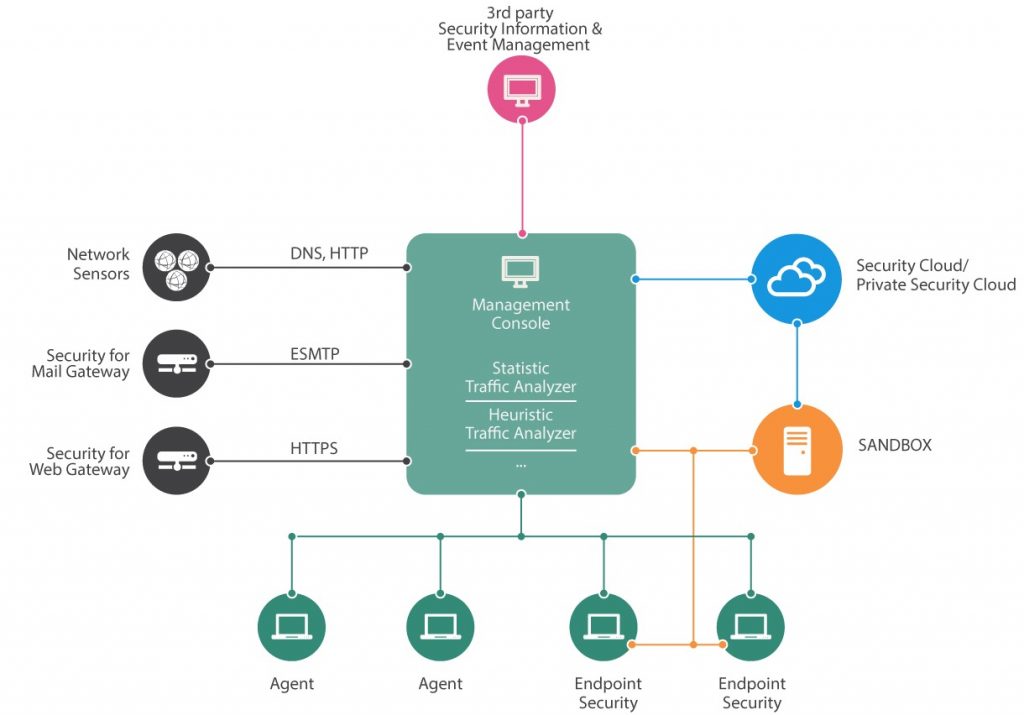
Illustration 3. Comprehensive solution architecture
The whole Anti-APT system consist of network sensors that responsible for organization traffic analysis, creation of metadata that describes this traffic’s content and separation of objects for further examination.Statistical anomaly detector is in charge for heuristics functionality. This module determines are there any deviations from the normal pattern in the enterprise’s network traffic. Sandbox module from its part analyzes the behavior of extracted objects.
Security officer sees the results of al lAnti-APT’s modules work in management console, which gather all the data from modules in a single center. In addition to such centralized solution, which needed at least some dedicated servers for its deployment, parallel installation of Anti-APT agents directly on user’s workstations is possible.
With a help from the local agents the specialized Anti-APT solution could obtain information about processes, responsible for the emergence of suspicious traffic. It allows to worn security officer far more precise. For example, he have to know about uncommon traffic on behalf of svchost.exe and other system’s processes. At last, agent allows Anti-APT solution to know about activity of the software that comes to the PCs not from network, but with USB-flash drives and other ways.
Precision of specialized Anti-APT solution considerably grows with using of cloud knowledge database. Such centralized repository is usually placed on the vendor site and provides files, domain names and IP-addresses reputations. Cloud also allows to distinguish targeted attack from mass infection using query to centralized database about uniqueness of revealed suspicious activity.
Attack through hotels takes place outside the company’s security perimeter and gives an idea of why comprehensive defense could contains centralized Anti-APT as well, as advanced local endpoint protection. These two approaches have to be realized together.
We are sure that only multilayered architecture could provide a decent level of protection. Different components of it are gathering data about events on endpoints, analyzing network traffic using among others heuristics algorithms, also using security cloud advantages to receive information about new threats faster and to improve the malware detection level. Team-work of specialized Anti-APT, which is concentrated on warning about attacks, and local security solution that is in charge for enforcement actions against malicious code.
Common approach suppose installation of the single full-featured solution that consist of sandbox and network sensor. In contrast to it solution with multiple sensors that provide data for centralized analysis is far more effective.
First and main advantage of separated sensors is more flexible deployment modelof solution on enterprise’s IT-infrastructure. In big companies traffic interception have to be organized in multiple points. This is due to many reasons: network addresses translation (NAT) usage, after which part of data in network packages is lost; organization of branches with high autonomy level; part of traffic accessibility only in certain network segments, etc. Combined solution (sandbox plus network sensor) installation in any needed point is in efficient from financial point of view. Many lighter sensors in any needed segment is far more effective.
Thus such sensors are originally designed to collect all the data in a single management console. In contract some combined devices are oriented only on its own web-interface. As a matter of fact in case of such scheme one more device is needed for centralized data collection.
One more argument in favor of multi sensors deployment instead of single device is an amount of traffic through every device. In case of SPAN (Switch Port Analyzer, popular mirroring method for traffic analysis) connection there aren’t network packages integrity confirmations. Traffic distribution on multi devices protects against increasing number of faults with flow increasing. At the same time the single management console for control and analysis remains.
Implementation phase withstanding
Let’stake a look on a multilayered Anti-APT solution work on different stages of targeted attack. In case of spear-phishing propagation Dark Hotel’s authors are sending either e-mail with the link to the exploit for Internet Explorer, or attaching exploit for Adobe software to the message. Besides there is an attack scenario, in which Microsoft Word documents with embedded Flash exploit are using (it were 0-day during APT disclosure).
Second injection method is adding Dark Hotel modules to the archives on P2P torrent networks. At last, third vector is already mentioned above – it’s hotel guest’s infection. In this case users are redirected through “iframe” tag on the hotel’s starting web-page, modified by malefactors. As a result of such substitution victim sees standard offer to download Google toolbaror update for Adobe software. If one will agree with it, PC will receive contaminated file.
Team-work of sandbox and network sensors provides counteraction. Files, extracted from the network traffic, are delivered to the sandbox. In its turn sandbox let know if that was a potentially harmful code. In case of dangerous code execution sandbox creates logs and deliver data about disclosure to the security officer’s dashboard. He receives detailed information about file activity on the PC and about actions that security software considers as suspicious. In case of hotel’s guests infection such actions would be stopped by local endpoint protection solution.
The network sensor detects targeted attacks by IP-addresses and domains, which were used during the action. Also network traffic content takes into consideration: in some cases APTs use its own specific protocols. Sandbox could use network sensor to control traffic of the suspicious programs, executed in a sandbox.
Besides, network sensor can detect targeted attacks on the basis of specific traffic abnormalities. For it security solution has to contain high-level behavioral templates, that describe typical malicious software behavior. Signs for these templates could be external connections with unknown newly created domains, periodicity of outbound traffic, locations of the servers and so on. For example, if enterprise works with some country never before and suddenly noticeable amount of data is transmitted this way in the nights – this is clearly the reason to trigger the alert.
Exploitation phase withstanding
If nevertheless the exploit code executes during the attack, than later it begins to download other APT’s modules on the infected PC. On this stage all the detection mechanisms above could trigger, as well as Anti-APT can detect precisely working modules of targeted attack.
Interesting module of Dark Hotel, for example, is digitally signed kernel level keylogger. Installed as Windows driver, software reads keystrokes directly from keyboard controller on the motherboard. For keylogger rerun standard tactic is used – registry key in branch HKCU added.
Since sandbox constantly keep an eye on objects (files, URLs) from network sensor and notify security officer about strange activity, then typical Windows registry keys addition doesn’t go unnoticed.
Conclusion
Kaspersky Lab handles sandbox development as internal technological process for many years. We already have a huge cloud base with files and URL’s reputation. Standalone variant of the sandbox for installation on the customer side is a direct continuation of a long-term development, new step in its evolution. Hardware resources of endpoints for software activity analysis are very limited in comparison with specialized dedicated hardware for standalone anti-APT sandbox. It’s crucial to analyze all the necessary events in scale of network infrastructure. It becomes possible after addition of network sensors to the sandbox. And after the addition of the single management console it’s possible to analyze targeted attacks development much more detailed.
Simultaneously Kaspersky Lab already has wide experience in APT analysis. Global Research and Analysis Team (GReAT) has an unique expertise in the field of such work.
Huge amount of already existing and simultaneously updated information in KSN5 from millions of devices allows answering the question that is important for customers: in this incident mass epidemic or it’s really targeted attack on particular enterprise’s infrastructure? These data is accessible through Kaspersky Lab’s security cloud (KSN), also it could be provided just on the client side as Kaspersky Private Security Network (KPSN). The combination of proven sandbox engine, experience in investigation of attacks and the accumulated volume of reputational data in our own cloud gives Kaspersky Lab strong positions for specialized Anti-APT solution development. Thus, it’s our deep conviction, such solution must be regarded as only one layer of comprehensive multilayered information security. Even with strong Anti-APT company can’t afford to forget about such other layers as advanced endpoint security, e-mail protections and so on.
1 It described in details in Kaspersky Lab whitepaper Strategies for Mitigating Advanced Persistent Threats (APT) >>>
2 For details please check https://securelist.com/the-darkhotel-apt/66779/ >>>
3 Information about actual threats you can find on https://securelist.com >>>
4 Here you could read more about Kaspersky Lab’s technologies https://www.kaspersky.com/small-to-medium-business-security/endpoint-advanced >>>
5 For more information about Kaspersky Lab’s technologies please check https://www.kaspersky.com/small-to-medium-business-security/endpoint-advanced >>>