- Part 1. How to mitigate APTs. Applied theory
- Part 2. Top-4 mitigation strategies which address 85% of threats
- Part 3. Strategies outside the Top-4. For real bulletproof defense
- Part 4. Forewarned is Forearmed: the Detection Strategy against Advanced Persistent Threats (APTs)
Part 2. Top-4 mitigation strategies which address 85% of threats
In Part 1 of this series, we discussed the importance of APT mitigation, outlining some of the theories and approaches to success – mostly the ASD’s Top-35 Mitigation Strategies. This second part takes a deeper dive into the ‘Top-4 Mitigation Strategies’ approach, which is successful against at least 85 per cent of all targeted attacks.
In Part 1, Kaspersky Lab distilled the Australian Signals Directorate’s (ASD) 35 point ‘Mitigation Strategy’ into four key logical areas, each of which should be considered as part of any effective threat mitigation strategy:
| Measures | Brief description |
| Administrative | Training, physical security |
| Networking | These measures are easier to implement at a network hardware level |
| System administration | The OS contains everything needed for implementation |
| Specialized security solutions | Specialized security software is applicable |
All four types of Strategy1 should be considered. Kaspersky Lab’s researchers have demonstrated that cyber criminals use a broad variety of techniques to access critical business data. Companies should respond in kind, using a variety of mitigation strategies, from employee training to highly sophisticated heuristics and cloud technologies, leaving no stone unturned. This is the only route to successful mitigation of modern APTs.
Kaspersky Lab does not simply protect selected components of IT-infrastructure from APTs. As a technology-driven organization, we have mapped listed strategies to our own vision of a highly effective multi-layered defensive strategy, which we believe aligns well with the ASD’s. Effective security has to be multi-layered, with Advanced Anti-Malware at the core of further layers of APT Mitigation mechanisms, such as Application Control, Vulnerability Management and more.
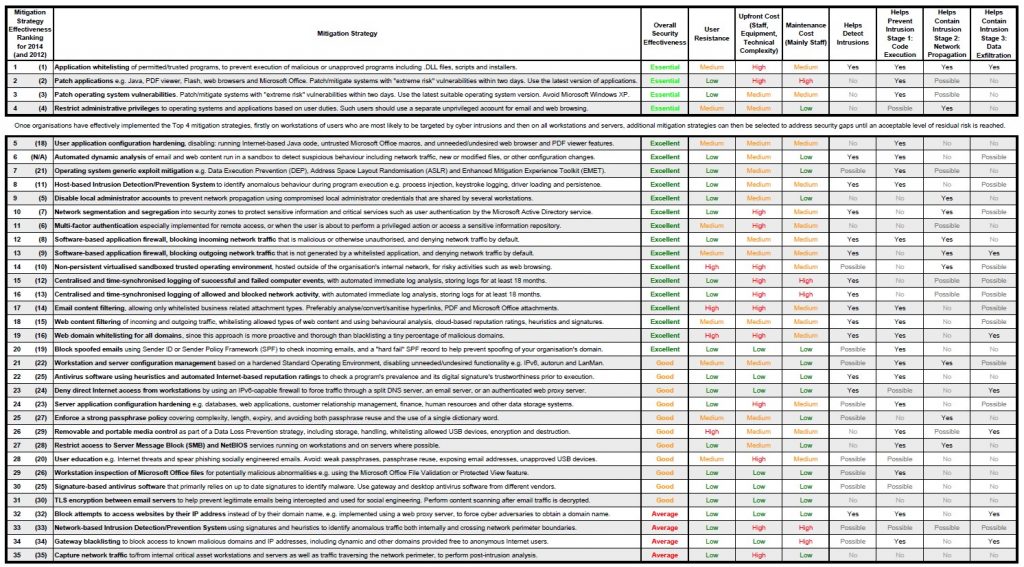
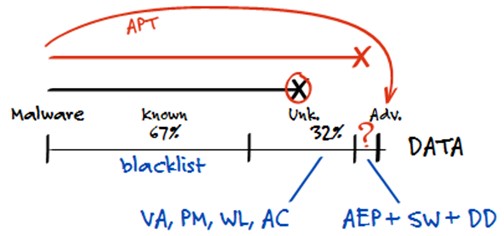
Besides strategies’ logical areas there are also classifications of threats, useful for its mitigation. Based on our statistics over a long period Kaspersky Lab could estimate that about 67% of attack attempts are going to be known viruses with identified and catalogued signatures. When the file is launched and run through a blacklist, it’s immediately denied if there’s a match. Kaspersky applies other technologies designed to detect unknown malware, these play a role to identify another 32% or so of these attacks. The last but very crucial 1% of threats consist of advanced malware, which is the lifeblood of APTs. Companies’ security solutions should mitigate all of these possible threats types.
To have a strong defence, you have to implement all the ASD’s Top-35 Mitigation Strategies on this list.
Kaspersky Lab’s solutions fulfil three of the top four strategies
Nineteen of the thirty-five strategies listed in the above table can be implemented using specialized IT security software. Kaspersky Lab’s solutions cover most of them, providing effective technologies for implementing three of the four key mitigation strategies: Application Control/Dynamic Whitelisting and Vulnerability Assessment/Patch management. Let’s take a closer look at them:
| ASD’s rank | Mitigation strategy | Kaspersky Lab technologies | Kaspersky Lab products |
| 1 | Whitelisting | Dynamic Whitelisting | Kaspersky Endpoint Security for Business. Kaspersky Security for Virtualization | Light Agent. |
| 2 | Patching application vulnerabilities | Vulnerabilities Assessment and Patch Management | Kaspersky Endpoint Security for Business tiers Advanced and Total. |
| 3 | Patching OS vulnerabilities |
It’s crucial to give the system administrators the ability to manage all the strategies-supporting features through a convenient single point of control. For Kaspersky Lab’s products we offer Kaspersky Security Center (KSC) as such centralized console.
Application Whitelisting in Kaspersky Endpoint Security for Business & Kaspersky Security for Virtualization.
Application Whitelisting is the most valuable counter-APT strategy any organization can adopt. It forms a powerful layer of protection against the executable components of APT, including as-yet-unknown ones. Interest in application control for desktops and servers has been increasing steadily over the last 5 years.
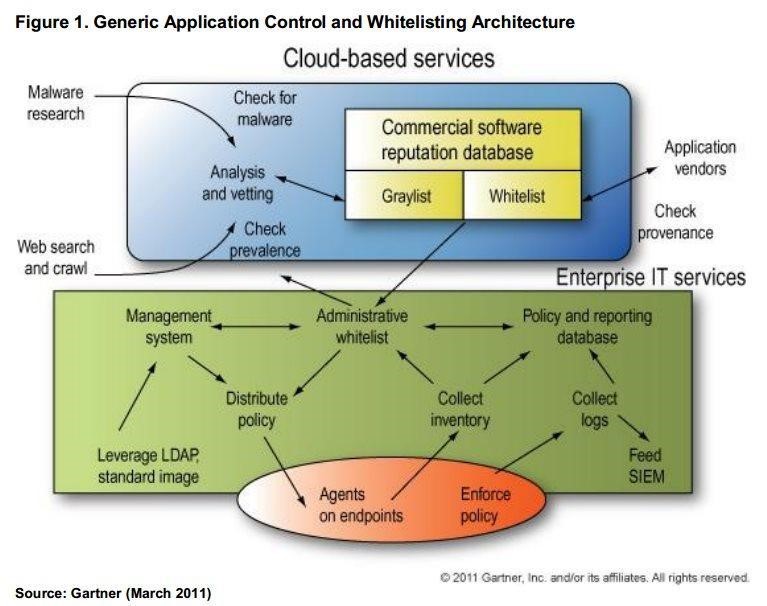
Kaspersky Lab’s solution implements Dynamic Whitelisting. According to Gartner2, the best application control implementations include vendor-supported whitelists of ‘safe’ software, automatically tracking approved changes – and continuously updated from a cloud database, making it effectively ‘dynamic.’ Application Control with Dynamic Whitelisting can help protect systems by giving administrators total control over the applications that are allowed to run on endpoints, regardless of end-user behaviour. This in addition to being able to block or allow certain, specified applications. The most secure Default Deny scenario involves blocking the execution of any application that has not been not specifically authorized by the administrator. This means that components of a targeted attack that are essentially applications won’t be allowed to run, effectively breaking the attack’s development. Kaspersky Lab’s implementation of this scenario makes sure that all the unmodified components of the OS would continue to run without interruption.
When it comes to implementing Application Control and Dynamic Whitelisting, Gartner recommends the creation of Inventory and “Gold” Images. Inventory creation enables system administrators to gain complete insight into all the software installed on every system in the company. This knowledge is vital. You can’t monitor what you don’t know you have and the best Whitelisting implementation plans start with an inventory. Once completed, all records about installed software on the corporate network will be stored in a single database, in convenient format, facilitating its analysis.
A ‘Gold’ image is a pre-constructed template of any company’s chosen, perfect installation: all of your business-critical applications and settings implemented according to best practice and fine-tuned to run at optimal performance. Gartner has also identified Application Control technology as one of the most useful traditional security capabilities for protecting industrial systems3. Kaspersky believes these measures for critical infrastructure defence should become mandatory.
Kaspersky Lab has developed its own Application Control and Whitelisting technologies, integrating them seamlessly with the other security components in Kaspersky Endpoint Security for Business. Kaspersky Security for Virtualization | Light Agent and Kaspersky Security for Mobile also include this technology. Mobile Application Control does not yet include Dynamic Whitelisting – but a Default Deny scenario can be set up for corporate mobiles.
Driven by a dedicated whitelisting division, Kaspersky Lab’s whitelisting service provides continuously updated databases of applications proven to be legitimate, trusted and safe. Kaspersky’s whitelisting database currently includes information about 1 4 billion unique executable files, compiled by a dedicated team of analysts. In 2013, after extended testing by the independent AV-Test Institute, it received an Approved Whitelisting Service certificate. It’s also worth mentioning that Kaspersky Application Control with Dynamic Whitelisting and Default Deny achieved top scores in all independent tests it participated in.4
To help the process of Application Control & Whitelisting implementation (including many automated features), Kaspersky Systems Management (available as part of Kaspersky Endpoint Security for Business or as a standalone toolset) provides both Inventory and Imaging tools, in exact accordance with Gartner’s advice.
Vulnerability Assessment and Patch Management in Kaspersky Endpoint Security for Business.
In second and third position on the list of counter-APT measures, application and OS patching are essential components of any successful threat mitigation strategy. “Extreme risk” vulnerabilities in business applications, operating systems and other software used by any organization can enable unauthorized code execution by criminals, with significant negative consequences for the business.
Kaspersky Lab’s Patch Management and Vulnerability Assessment components are implemented as part of our Systems Management technology, integrating them into the broader, day-to-day management of systems, for ease of use. Let’s take a look at what each of these components do.
Vulnerability Assessment is a critical element in protecting companies against attacks involving exploits of software vulnerabilities, including targeted attacks. An IT department using Vulnerability Assessment can promptly detect vulnerabilities in corporate software that could potentially be exploited by cybercriminals, and can quickly take action to close these security gaps using patch management.
A special software agent on the endpoint is used to detect vulnerabilities. It analyses versions of Windows OS and other installed software, comparing them with data in Kaspersky Lab’s continuously updated self-developed vulnerability database. Our database contains all needed information about popular third-party applications vulnerabilities. Vulnerability assessment was designed to be used in conjunction with Patch Management to tackle software vulnerabilities promptly and effectively.
Patch Management helps keep endpoints fully updated, significantly reducing the risk of successful exploit attacks. Kaspersky Lab’s patch management systems provide a high level of automation for system administrators, and can be used instead of or in conjunction with Microsoft’s WSUS.
Kaspersky Lab’s Vulnerability Assessment and Patch Management technologies are available in the Advanced and Total tiers of Kaspersky Endpoint Security for Business.
When it comes to ‘patches managed’ figures, Kaspersky Lab’s solution is a market leader, earning 1st place for the number of patched products and vendors. The effectiveness of Kaspersky Lab’s Patch Management solution has been proven in independent tests, including the latest test conducted by AV-test.
Let’s once again take a look at the technologies from the point of view of threats classification, that we mentioned above in the beginning of the document. Application Control with Whitelisting, Vulnerability Assessment and Patch Management are meant to mitigate unknown threats as a part of any APT. For the most advanced threats Kaspersky Lab also offers Automated Exploit Prevention, System Watcher and Default Deny.
Kaspersky Lab’s Application Controls, Dynamic Whitelisting, Vulnerability Scanning and Patch Management technologies implement 3 aspects of the Top-4 Mitigation Strategies effectively. A major aspect of targeted attacks – software vulnerability exploits – could be successfully mitigated using these measures. But bulletproof defence needs something more than Top-4. In the third part of this document, we’ll look deeper into the rest of useful counter-APT strategies.
1 Described in the Part 1 of Strategies for Mitigating APTs
2 How to Successfully Deploy Application Control, Gartner ID G00246912
3 Competitive Landscape: Critical Infrastructure Protection, Gartner ID G00250700
4 For detailed test results please go to follow pages: 1, 2 and 3.