
In our initial blogpost about “Operation Triangulation”, we published a comprehensive guide on how to manually check iOS device backups for possible indicators of compromise using MVT. This process takes time and requires manual search for several types of indicators. To automate this process, we developed a dedicated utility to scan the backups and run all the checks. For Windows and Linux, this tool can be downloaded as a binary build, and for MacOS it can be simply installed as a Python package.
How to back up your device
Windows
On Windows, the easiest way to do a backup is via iTunes:
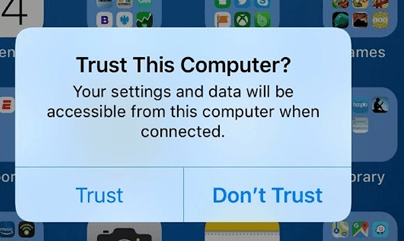
- Connect your device to a computer that has iTunes installed. Unlock your device and, if needed, confirm that you trust your computer.
- Your device should now be displayed in iTunes. Right click on it and press “Back Up”.
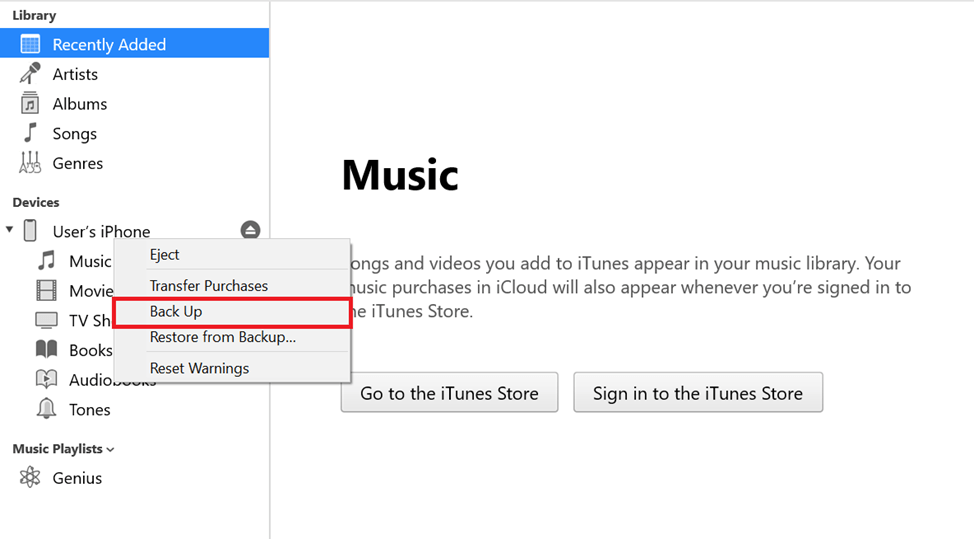
- The created backup will be saved to the %appdata%\Apple Computer\MobileSync\Backup directory.
macOS
If your macOS version is lower than Catalina (10.15), you can create a backup using iTunes, using instructions for Windows. Starting from Catalina, backups can be created through Finder:
- Connect your device to the computer and, if needed, confirm that you trust the computer.
- Your device should now be displayed in Finder. Select it and then click “Create a backup“.
- The created backup will be saved to the ~/Library/Application Support/MobileSync/Backup/ directory.
Linux
To create a backup on Linux, you will need to install the libimobiledevice library. In order to create backups of devices with the latest versions of iOS installed, you will need to compile this library from source code (you can find the build instructions in the Installation/Getting Started section).
After you install the library and connect your device to the computer, you can create a backup using the idevicebackup2 backup --full command.
During the backup process, you may need to enter your device passcode multiple times.
How to use our triangle_check utility
After you do a backup of your device using the instructions above, you will need to install and launch our triangle_check utility.
The triangle_check Python package
No matter what operating system you have, you can install the triangle_check Python package that we have published to the Python Package Index (PyPi). To do that, you need to have internet access as well as have the pip utility installed.
You can install the utility using two methods:
- From PyPI (recommended):
Run thepython -m pip install triangle_checkcommand. - Building from Github:
Run the following commands:
git clone https://github.com/KasperskyLab/triangle_check
cd triangle_check
python -m build
python -m pip install dist/triangle_check-1.0-py3-none-any.whl
After installing, you can launch the utility with the following command:
python -m triangle_check path to the created backup.
Binary builds
If you have Windows or Linux, you can also use the binary builds of the triangle_check utility that we have published on GitHub. Follow the instructions below to use it:
Windows
- Download the triangle_check_win.zip archive from the GitHub releases page and unpack it.
- Launch the command prompt (cmd.exe) or PowerShell.
- Change your directory to the one with the unpacked archive (e.g.
cd %userprofile%\Downloads\triangle_check_win). - Launch triangle_check.exe, specifying the path to the backup as an argument (e.g.
triangle_check.exe "%appdata%\Apple Computer\MobileSync\Backup\00008101-000824411441001E-20230530-143718").
Linux
- Download the triangle_check_win.zip archive from the GitHub releases page and unpack it.
- Launch the terminal.
- Change your directory to the one with the unpacked archive (e.g.
cd ~/Downloads/triangle_check_linux). - Allow the utility to be executed with the
chmod +x triangle_checkcommand. - Launch the utility, specifying the path to the backup as an argument (e.g.
./triangle_check ~/Desktop/my_backup/00008101-000824411441001E-20230530-143718).
Interpreting the results
The utility outputs “DETECTED” when it locates specific indicators of compromise, and that would mean that the device was infected.
Also, it may print out “SUSPICION” that would mean that a combination of less specific indicators points to a likely infection. Finally, if the message displayed is “No traces of compromise were identified“, then the utility did not find any signs of ‘Operation Triangulation’ compromise.
In search of the Triangulation: triangle_check utility






















u
Question about the backup password protection: does the triangulation check work with iphone-backup password protection or do I have to make a backup without password protection?
Securelist
Hi U!
The tool works both with unprotected and password-protected backups.
Forrai Tibor
It asks you for the iPhone backup’s password on the command line.
Klaus
Thanks very much!
Ivan
Y para los que no sabemos hacer nada de esto, como hacemos?
Anton
Hello, the tool identified that my iPhone was infected (“DETECTED” result), but the system was successfully updated to the latest IOS (16.5). Does this mean that now my device is clean?
Securelist
Hi Anton!
We have not observed any indicators of compromise on latest iOS versions. For additional protection against Operation Triangulation, we recommend to disable iMessage, enable Lockdown Mode and reboot device more often/periodically
James Pearson
Hi Anton – I’m a journalist with the Reuters news agency. We’ve been keen to speak to people whose devices were infected with triangulation. If you’re comfortable doing so, there are secure ways to contact me here: https://pearswick[.]press
Christina
Hi Anton,
My device has been affected with this virus as well. There is zero support from Apple on this. It’s very disheartening. The entire Apple support team still downplay the whole scenario and refuse to help me.
Kate
I’ve had the same experience. They just deny that it’s even possible. I have zero click malware on all my devices – running current OS and don’t even know how I can have it detected. (I have someone cyberstalking me who’s a hacker). I don’t know what to do or where to go for help..
Paul
Still happening iOS 17.3 beta
has also been for years comes up with an exclamation mark on messages but can’t find what for, check file system I have a modified Var/Hardware and various others
YONI
It doesn’t work if the backup is encrypted in Windows, it requires a password – you can’t press anything in CMD that asks for a password
Alex
C:\triangle_check_win>triangle_check.exe “C:\Users\manol\Apple\MobileSync\Backup\00008030-000C11A02163802E”
Traceback (most recent call last):
File “triangle_check.py”, line 8, in
File “triangle_check\__main__.py”, line 29, in main
File “triangle_check\__init__.py”, line 133, in scan_dir
FileNotFoundError: [Errno 2] No such file or directory: ‘C:\\Users\\manol\\Apple\\MobileSync\\Backup\\00008030-000C11A02163802E\\Manifest.plist’
[10304] Failed to execute script ‘triangle_check’ due to unhandled exception!
i dont know how to do that can you help me please?
Backup route:
C:\Users\manol\Apple\MobileSync\Backup\00008030-000C11A02163802E
IS in windows.
thank you
Securelist
It seems that the path to the backup is wrong. The backup folder must contain a Manifest.plist file.
San
Hi, I am receiving the same error as this commentor but on my Mac for Manifest.plist file. However it is present in my backup folder. So I am not sure why I am also recieving this same error despite having the file present within the folder
gugo
You have to put the PATH between brackets : python -m triangle_check “PATH”
I’ve had the same error and I think it’s easy to misunderstand the command the way it’s written in the article. You can right click on your backup folder to copy as a file path and it will paste it directly between brackets
Julie
Can you help me I have a iPhone iOS16.5 12
San
I strongly I am a target of this attack due to strange activities that have happened on my device from past 2 months. I am not well versed with python, so can you please make a video tutorial on how to download and use this script?
T
Nice tool!
Is there a version for full extracted filesystems available?
Mike
Unfortunately, the instructions are not very readable. The program doesn’t open for me. Wasn’t it possible to make a graphical version of the program? How about recording a video on how to run the program?
Securelist
Hi Mike!
Unfortunately, there’re no such plans right now. If you post here what precisely you have done to open the program, our experts may suggest what can be done to fix the issue.
If one day a more user-friendly version of the utility or instructions to it is out, we’ll inform you about it.
Walnut
I have been hit by this malware on at least two iOS devices, beginning no later than June 2021, according to MVT scans of EIFT full tar dumps. One of the infected devices ultimately became completely disabled from wireless connectivity and sat unused in a Faraday bag for two years until I could perform a physical acquisition. I am 99% sure it was someone associated with or employed by the US government. Thanks for publicizing this and developing the utility; telling people “my phone is hacked and I can’t use it,” without reasonable proof, is a terrible icebreaker and a credibility nightmare.
Juan
Is the script capable of analyzing full file system extractions from ios or does it only works with itunes backups?
Georgy Kucherin
Hi Juan,
The triangle_check script is designed to work only with iTunes backups.