
Classifying methods used to steal data
The United States Federal Trade Commission (FTC) views the issue of the theft of confidential data in the broadest sense. Their website provides information about many traditional “non-computerized” means of stealing information, such as stealing wallets and purses, searching through shredded papers that have been thrown in the garbage, making calls allegedly from a financial institution, and using special devices to scan credit card numbers, to name a few.
However, in addition to all these techniques, there are other ways of stealing information. There are at least three different ways to steal data using a computer. The first is when the computer user voluntarily gives information to a malicious user, having trusted a false request for said information. These requests usually come in the form of mass mailings. The malicious user will have created a false website that imitates the site of an actual bank or other financial organization. This kind of computer crime is called phishing.
The second way to steal confidential information involves tracking and logging a user’s actions. This kind of electronic espionage is carried out using Trojans which Kaspersky Lab classifies as Trojan-Spy programs. One of the most popular kinds of Trojan-Spy program is the keylogger, covered in detail in a previous article.
The third technique for stealing confidential data involves the use of malicious programs (most often Trojans) to search for confidential information on a user’s computer and then transmit this data to a malicious user. In this case, a malicious user may only receive data that the user considered important enough to enter into the computer’s memory. However, this seeming drawback is compensated for by the fact that the data is transmitted without user participation. For more details about this technique, see: https://encyclopedia.kaspersky.com/knowledge/trojans/.
These malicious programs can spread in a number of ways: they can be activated when an email attachment is opened or when a user clicks on a link sent via instant messaging. They can also launch when a file is opened from a directory on a peer-to-peer network or by using scripts on a website that take advantage of idiosyncrasies in web browsers, making it possible for these programs to launch automatically when users visit these sites. Such programs can also be spread via other previously installed malicious programs that are capable of downloading and installing them to the system.
Malicious programs like PSW Trojans are designed to access a range of information about the system, the user and passwords to a number of programs and operating system services. In order to do this, they scan all storage areas which contain relevant data: Windows protected storage, registry keys and certain program files of interest to a malicious user (usually instant messaging clients, email systems and Internet browsers).
After gathering data, the Trojan will usually encrypt it and compress it into a small binary file. Later, the file may be sent via email or placed on the malicious user’s FTP server.
The way in which the abovementioned malicious programs function is covered in detail in “Computers, Networks and Theft”, which examines two different techniques used by modern security solutions to protect confidential data
How do today’s products protect confidential data?
Almost all modern security solutions (such as Security Suite) include a component which protects confidential data, typically called Privacy Control. (In some applications, this component is combined with other security components, such as an anti-phishing component.) The key purpose of this component is to protect confidential information on the user’s computer against unauthorized access and transmission.
Let’s take a look at how Symantec products implement protection for confidential data. This company was chosen because they were one of the first to implement protection for confidential data in their products, before other market players followed suit and added their own, similar components.
Back in late 1999, Symantec published information about their new product, Norton Internet Security 2000. This featured the new Norton Privacy Control, with one of its key modules being Confidential Data Blocking.
This component works in the following way:
- the user must enter all data he considers confidential,
- the product will then analyze all outgoing traffic from the user’s computer and either “cut up” all outgoing confidential data, or substitute it with meaningless symbols (such as “*”).
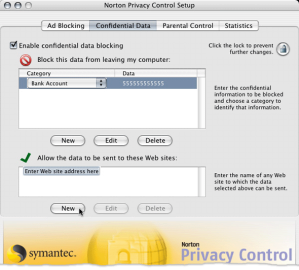
Figure 1. Norton Internet Security 2000 Confidential Data component
Norton’s Privacy Control component is included in new Norton products, such as Norton Personal Firewall and Norton Internet Security.
The company’s latest flagship product is Norton360, which was released by Symantec in 2007. The Privacy Control component is also included in Norton360, but not in the regular package. Instead, it comes as an Add-on Pack which can be downloaded from Symantec’s official website.
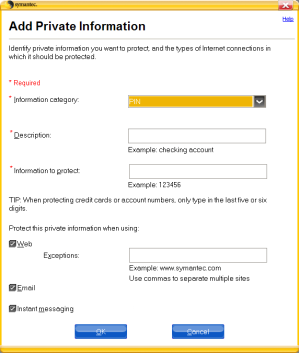
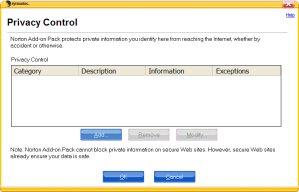
Figure 2. Norton360 Confidential Data Blocking component
The main idea behind the product remains unchanged: just as Norton Internet Security 2000, it uses a table into which the user is meant to enter his confidential data (see figure 2).
Drawbacks in traditional approaches to protecting confidential data
What made the program’s developers decide to remove the Confidential Data protection component from the list of standard Norton360 modules? There are probably several reasons, but one stands out in particular. The truth is that this approach to protecting confidential information is not effective ─ it only creates the illusion of security.
Some official descriptions of the latest version of Norton Internet Security say that it “blocks […] transmitting unauthorized information”. However, this is not actually the case.
If you look carefully at the first window in Figure 2, you can see a note in the lower half of the window: Norton Add-on Pack cannot block confidential information on secure Web sites. However, secure Web sites already ensure your data is safe.” The reason for this note is simple: data exchange with secure websites uses data encryption, which makes it impossible for any third party to analyze the data transmitted.
A confidential data protection component should protect users from Trojans like PSW Trojans. What prevents a Trojan from encrypting all data being transmitted? Nothing, actually, and over 80% of Trojans do just that. That is why the confidential data protection component – which is based on traffic analysis and searching for previously entered data sequences – is not capable of preventing data from being sent out in most cases, since it simply will not find the data once it has been encrypted by a Trojan.
Furthermore, storing all your confidential information in one place after entering the data in windows like the ones in Figure 2 cannot do anything to increase security. On the contrary, instead of having to search through all kinds of data in several places on a computer’s file system, a malicious user knows right where to go and all he has to do is gain access to the file used by the protection component. There is no doubt that developers do everything they can to secure the data entered by the user, but security cannot be guaranteed.
An example of how this component works is as follows: if a webpage asks you to enter your telephone number, Norton Internet Security 2000 will ask you if you are sure that you want to send this confidential data after you have entered it into the text field.
However, that warning is not especially helpful in real life, since the user decision to enter the requested information is based on whether or not s/he trusts the website. If the user believes the website is authentic, then the program warning will not stop the user from entering data. If the user believes the website is fraudulent, then he will not bother to enter any data in the first place.
Unfortunately, today there are more and more fraudulent websites designed by malicious users to look very similar to the official websites of financial institutions, and users willingly enter their confidential data despite security solution warnings.
An alternative approach to protecting confidential data
There is another approach to protecting confidential data based on blocking the actions of malicious programs at earlier stages, before data is transmitted, and before it is too late.
In order to steal confidential information, a malicious program must take two actions: find the information and extract it from wherever it is being stored (that could be a file, a registry key, or an operating system’s special storage area) and transmit it to the author of the malicious program via specific channels. Since many computers already have firewalls installed which control the network activity of applications on the computer, the malicious program cannot transmit any collected data under its own name. That is why many PSW Trojans use different tactics to evade firewall protection, making them able to send data without the user’s knowledge.
It should then follow that the protection component should track the activity of applications when that activity is indicative of a potential attempt to steal confidential information:
- An attempt to gain access to personal data or passwords located in Microsoft Windows’ Protected Storage.
This service is used to store confidential data, such as local passwords, passwords for POP and SMTP email servers, Internet access passwords, passwords for automatic access to closed website sections, other Internet data and passwords for automatically filling out Internet forms, and other information. These data are entered into the relevant text field of email clients and web browsers. As a rule, the user may store the entered data; in order to do so, he needs to mark it with a special flag. In this case, the data that is entered is stored in Microsoft Windows Protected Storage.
Even users who are concerned about information leaks and do not save passwords or other data in their Internet browser usually save their email passwords, since entering their password each time they receive or send something is too time consuming. Since many Internet providers use the same password for email and for Internet access, obtaining this password will give a malicious user access to both the email account and the Internet connection settings.
-
- Attempts to stealth data sending.
In order to transmit the data it has collected, a malicious program will try different tactics to get around a firewall if one is installed on the victim computer. For example, it may stealthily launch an Internet browser process and transmit data using program interfaces common to most browsers (COM, OLE, DDE and others). Since most modern firewalls have a set of pre-installed settings that permit network activity for trusted applications, the firewall will not react to the transmission of data by the Internet browser and the user will not be aware of this activity nor will he be able to prevent the data leak.
When using this approach, encryption of stolen data by a malicious program is not a problem, as the malicious program’s payload will be blocked before encrypted information can be transmitted.
This approach is implemented in Kaspersky Internet Security 7.0.
Trojan-PSW.Win32.LdPinch: how KIS 7.0 protects against the theft of confidential data
Kaspersky Internet Security 7.0 also features a confidential data protection module that serves as one of the subsystems of its Anti-Spyware component (see Figure 3). It analyzes the behavior of all processes in the user’s system and if it detects either of two of types of action described above, it will either warn the user or automatically block the action.
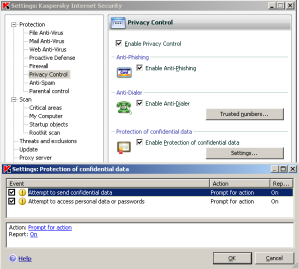
Figure 3. Configuring Kaspersky Internet Security 7.0 Anti-Spyware component
Let’s examine how this KIS module protects users against attempts to steal confidential data using Trojan-PSW.Win32.LdPinch as an example. This Trojan’s main goal is to steal passwords from a range of applications installed on a user’s computer.
As this virus description shows, Trojan-PSW.Win32.LdPinch is designed to steal information about a computer’s hard drive and the amount of free space remaining on it, the current user, the computer’s network name, the version of the operating system, the processor type, the monitor specifications, the applications installed on the computer, the current running processes and any existing dial-up connections. Of course, most of the information it steals are passwords for a wide range of programs, including the following:
- instant messaging clients:
-
-
- ICQ 99B-2002a
- ICQ 2003/Lite/5/Rambler
- Miranda IM
- TRILLIAN
- &RQ, RnQ, The Rat
- QIP
- GAIM
- MSN & Live Messenger
-
-
- email clients:
-
-
- The Bat!
- MS Office Outlook
- Mail.Ru Agent
- Becky
- Eudora
- Mozilla Thunderbird
- Gmail Notifier
-
-
- Internet browsers:
-
-
- Opera
- Protected Storage(IE,Outlook Express)
- Mozilla Browser
- Mozilla Firefox
-
-
- automatic dialers:
-
-
- RAS
- E-DIALER
- VDialer
-
-
- file managers:
-
-
- FAR
- Windows/Total Commander
-
-
- FTP clients:
-
-
- CuteFTP
- WS FTP
- FileZilla
- Flash FXP
- Smart FTP
- Coffee Cup FTP
-
and many others.
Stolen passwords are used to further spread malicious programs. Once a password for an ICQ client is obtained, for example, the Trojan will modify this password on the ICQ website and begin sending messages with a link to its own executable file from the victim’s account in an attempt to infect as many machines as possible.
All stolen data is encrypted and sent either to a specific email address or placed on the malicious user’s FTP server.
Confidential data protection systems which analyze traffic (such as Norton Privacy Control) cannot prevent encrypted data from being sent, even if the user enters all of his passwords to all of his programs in a list of monitored data. That means that if a user has installed a Symantec program with Privacy Control or another product that uses the same approach to protect confidential information, his computer may be attacked by a new version of Trojan-PSW.Win32.LdPinch that is not included in the antivirus database and is not recognized by any of the other security components. As a result, most of that user’s passwords will be stolen and then used by cyber criminals at their discretion.
However, a protection system which analyzes application activity blocks both the harvesting (see Figure 4) and stealthed transmission (see Figure 5) of confidential data by Trojan-PSW.Win32.LdPinch.
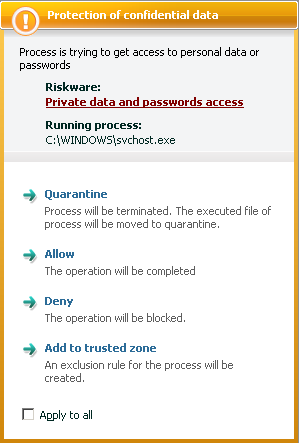
Figure 4. Kaspersky Internet Security 7.0 warns of Trojan-PSW.Win32.LdPinch
attempt to gain access to confidential data
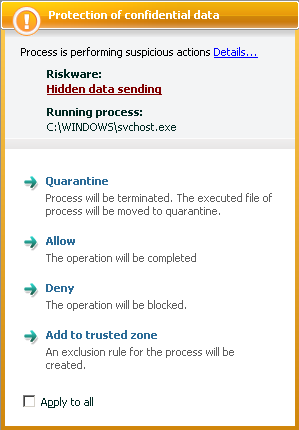
Figure 5. Kaspersky Internet Security 7.0 warns of Trojan-PSW.Win32.LdPinch
attempt to secretly transmit confidential data
Conclusion
This article covers the classification of methods used by malicious users to steal information via computer, and analyzes two fundamentally different techniques in developing modules which protect confidential data. Such modules are implemented in contemporary security solutions. The article also analyzes the effectiveness of both approaches, using a widely known Trojan as an example.
A comparison of both techniques shows that the technique based on analyzing application activity that could indicate an attempt to steal confidential data has major advantages. The approach using a list created by the user for his eyes only has been shown to be less effective, as it is more difficult to ensure that no part of that list is ever transmitted from the user’s computer.




















Modern Security Suite solutions: methods for protecting confidential data