
- May in figures
- Spam in the spotlight
- The geographical distribution of spam sources
- Malicious attachments in email
- Phishing
- Conclusion
May in figures
- The percentage of spam in email traffic in May was down 2.5 percentage points and averaged 69.7%
- The percentage of phishing emails rose slightly compared with April, and averaged 0.0024%
- Malicious attachments were found in 2.8% of all emails, a rise of 0.4% compared to the previous month
Spam in the spotlight
May turned out to be fairly varied when it came to spammer creativity. In fraudulent and advertising messages the spammers made active use of well-known people and companies. The quantity of holiday-related spam fell, but we still came across mailings exploiting Mother’s Day and Memorial Day.
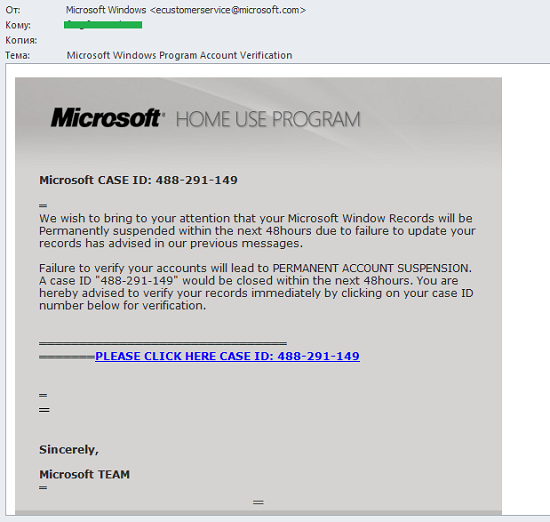
Spammers target Microsoft
In May spammers organized a phishing mailing disguised as messages from Microsoft customer service and support. The messages, which at first glance appear to come from the perfectly legitimate microsoft.com domain, stated that the user’s “Microsoft Window” records would be suspended due to the absence of updates that were supposedly recommended in earlier messages. Recipients are told to immediately follow the link in the email to avoid any disruption. Those users falling for the scam ended up on a phishing site specially crafted to steal personal information.
But a sharp-eyed reader will notice that the name of the operating system is called Microsoft Window and is missing an ‘s’ at the end. In addition, the message uses ‘=’ symbols to break up the text, there’s no link to the official site of the company or customer service and support contacts – things that just wouldn’t happen if it was a legitimate email.
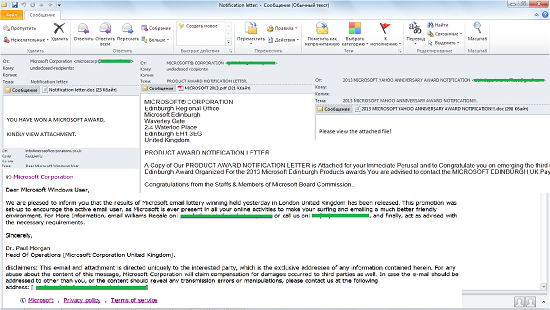
We also came across fraudulent notifications of wins in a non-existent lottery that was supposedly organized by Microsoft. The recipient was, of course, a winner.
In some mailings the scammers sent notifications about a lottery win and asked the recipients to contact them for more information, while other messages promised huge sums of money and asked for a small payment to cover the costs of processing the winnings.
May’s ‘holiday’ spam
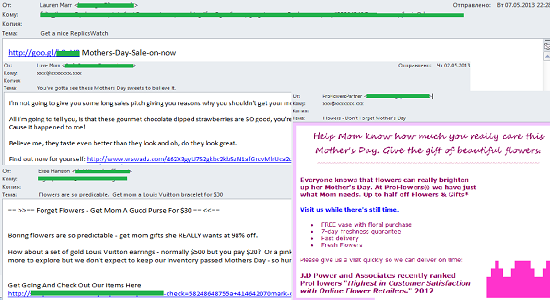
In May spammers continued to exploit the theme of Mother’s Day – traditionally celebrated on the second Sunday of May in the US – with adverts for flowers, chocolates and fake designer goods. It is noteworthy that Mother’s Day is the second most popular holiday after Valentine’s Day in terms of spam mailings, and the quantity of spam from “flower” partner programs increases dramatically in the preceding days and weeks. The majority of these mailings use a specific template with only the picture of flowers and the name of the holiday that the message relates to changing.
On the last Monday of May the US marks Memorial Day – a national holiday commemorating men and women who have died serving in the country’s military. This year the day was linked to spam messages with adverts for online car sales. It should be noted that even these innocent looking spam messages can be used to harvest personal data, including bank payment details. In addition, we detected a mailing with an offer to buy “likes” on Facebook that was also linked to Memorial Day.
The geographical distribution of spam sources
May saw no changes among the Top 3 sources of worldwide spam. China remained in 1st place with 21.4% of all distributed spam, a decrease of 2.5 percentage points.

Sources of spam around the world by country
The amount of spam sent from the US accounts for 16.3%, keeping this country 2nd in the rating. In May, South Korea’s contribution continued to grow and reached 12%. Overall, these three countries produced nearly half of the world’s spam.
Taiwan (5.9%) and Vietnam (5%) remained in the Top 5. Ukraine came 6th with 4.8% of the total spam distribution. Kazakhstan (4.3%) climbed one position up from April’s 8th place having added nearly one percentage point to the global spam flow. Russia (2.2%) decreased its contribution by 1.1 percentage points and moved down to 10th place.
Canada was May’s newsmaker having rocketed from 20th place in the rating to 11th with 1.8% of distributed spam, an increase of 1 percentage point.

Sources of spam in Europe by country
South Korea remained the main source of spam sent to European users in May (45.7%): its share grew by 2.3 percentage points. The US remained in 2nd position (5.8%) although its share fell by 0.9 percentage points. As in the previous month Vietnam came 3rd with 5.8% of spam sent to European users, an increase of 0.6 percentage points.
Meanwhile, China saw its share fall by 1.1 percentage points, dropping from 5th to 8th position in the rating. Germany’s contribution saw no change and accounted for 1.2%, but due to the fluctuations in spam flows of the other countries it fell from 13th to 16th place in the Top 20.
Asia (56.1%) remained the leading source of spam by region: in May its share increased by 0.4 percentage points compared with the previous month. As in April, the Top 3 also included North America (18.1%) and Eastern Europe (14.6%).
Malicious attachments in email
In May, malicious attachments were detected in 2.8% of emails, an increase of 0.4 percentage points from April.
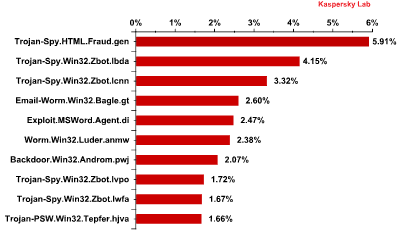
Top 10 malicious programs spread via email in May 2013
In May, Trojan-Spy.html.Fraud.gen remained the most widespread malicious program. This malicious program is used on HTML pages which imitate the registration forms of well-known banks or e-pay systems and steals user credentials for online banking systems.
Representatives of the ZeuS/Zbot family occupied 2nd, 3rd, 8th and 9th positions in May’s rating. This notorious Trojan program used to be very popular in 2009-2010 but it has not been among the most widespread malicious programs in recent years. This program targets users’ confidential information including their credit card credentials. The share of this Trojan in May’s rating accounted for 26.2%.
Interestingly, Exploit.MSWord.Agent.di appeared in 5th place in May’s Top 10. Exploits are seldom distributed via email attachments as their authors prefer links in spam messages which redirect the victims to malicious sites where exploits are downloaded on their computers without being noticed by users. Exploit.MSWord.Agent.di uses another tactic: it spreads a Microsoft Word document with malicious code utilizing the CVE-2012-0158 vulnerability to infect the computer.

Distribution of email antivirus detections by country
The US remains the country which is most heavily targeted by malicious emails. Its share increased by 1.8 percentage points compared with April and came to 14.2%. Germany remained in 2nd (9.5%) although its contribution reduced by 1.2 percentage points. The UK (6.1%) came 3rd.
April’s Top 10 members China and Russia were replaced by Hong Kong (2.9%) and Canada (2.5%).
In May, Russia’s share came to 2.2% of all antivirus detections.
Special features of malicious spam
In May, fake messages sent on behalf of the well-known online stores remained very popular. In the run-up to the summer we received a mass mailing imitating official notifications from the online store Amazon. The fraudsters thanked recipients for a non-existent order and invited them to make changes to the order or track its status by visiting the company’s website or clicking the link in the email. The links in the email really led to the official online store website, not to phishing pages or malicious files. However, the same message stated that additional information about the order could be found in the attachment. This information was highlighted in blue so that the user could easily notice it. Unlike many similar letters, the spammers did not frighten the recipients with an order cancelation to make them open the attachment. Instead they provided information about the terms and conditions related to a cancelled order.
The attached archive Your Order Details with Amazon.zip contained the executable file Your Order Details with Amazon.PDF.exe detected by Kaspersky Lab as Backdoor.Win32.Androm.qp. In May, one of this family’s malicious programs was the seventh most popular piece of malware spread by email, while in April a program belonging to this family was among the Top 3. Once on the victim’s computer, Backdoor.Win32.Androm can, for example, download other malicious files, send a variety of information from the computer, or make it part of a botnet without the user’s awareness.
In May spammers continued to send malicious fake notifications on behalf of well-known logistics companies: our traps caught messages allegedly written by a representative of the UPS postal service. They informed recipients that the courier had failed to deliver their parcel due to an incorrect delivery address so they had to pick it up in the company’s office. To do it they had to print out the document attached to the email.
Instead of the promised document the attached archive UPS_Label_23052013.zip contained the executable file UPS_Label_23052013.exe, detected by Kaspersky Lab as a Trojan-PSW.Win32.Tepfer.kxdh. In April, one of the malicious programs from this family was the 4th most popular piece of malware spread by email and in May it was 10th. This Trojan steals passwords from FTP clients and email programs as well as logins and passwords entered in the browser. In order to convince the victim of the legitimacy of the message the fraudsters added the notification that the email had been sent from a public address and it did not require any reply. The message also contained a confidentiality warning.
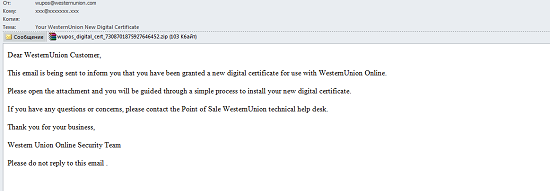
The Trojan Tepfer.kdkq was found in yet another May mass mailing. A malicious file called wupos_digital_cert_{DIGIT [19]}.exe was packaged in a zip file attached to an email which had allegedly been sent by the Western Union security service.
Recipients of the email were informed that they had been issued new digital certificates for money transfers on the Internet and in order to install it they had to open the attachment.
The message also stated that any questions could be referred to the Western Union support service. The spammers hoped that this technique would diminish user suspicions about the legitimacy of the email.
Phishing
The percentage of phishing emails increased very slightly compared with April, reaching 0.0024%.

The distribution of the Top 100 organizations targeted by phishers, by category*
This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
Social networking sites continued to be the most attractive target for phishing attacks: their share grew 0.5 percentage points and averaged 35.93%.
The Top 3 also included Search engines (14.95%) and Financial and e-pay organizations (14.93%) which were 2nd and 3rd respectively.
IT vendors remained in 4th position (9.93%). They were followed by Online stores (8.68%). Telephone and Internet service providers (8.39%) moved down one position to 6th.
Conclusion
Spammers continued to use the names of famous people and companies both for fraud and for advertising products and services. In May, the Microsoft name was actively used by scammers to trick users.
In May, most of the world’s spam originated from two countries – China and the United States. However, South Korea’s share, which was the 3rd highest, continued to grow bringing this country even closer to the 2nd position. At the same time, almost half of Europe-bound spam was sent from South Korea while the United States and Vietnam trailed far behind in 2nd and 3rd respectively.
As expected, Social networking sites remained the most attractive target for phishers: their share increased slightly, as did that of Online stores. Meanwhile, May saw a decrease in the number of attacks involving online games. However, we expect a rise in the number of phishing attacks on this category of sites in June, the first month of the summer holidays.
During the summer holidays schoolchildren and students often fall victim to fraud. Scammers are very keen on fake notifications from a wide range of online services at the moment. Therefore, we recommend that you be cautious if you receive a notification from a service. Remember that official services never ask customers to enter and confirm personal or banking information via links contained in emails. Neither do they threaten to block customer accounts. Never click on links blocked by an antivirus program or a browser. Pay attention to the links in the message. If the link indicated in the email leads to an unofficial site or if the text of the email contains the address of the official website while the link in fact leads to another site, this may mean you have a phishing email in front of you. If you have any doubts about the authenticity of the email, contact the customer support of the organization which is said to have distributed the email and find out whether this mass mailing really was sent out.
























Spam in May 2013