
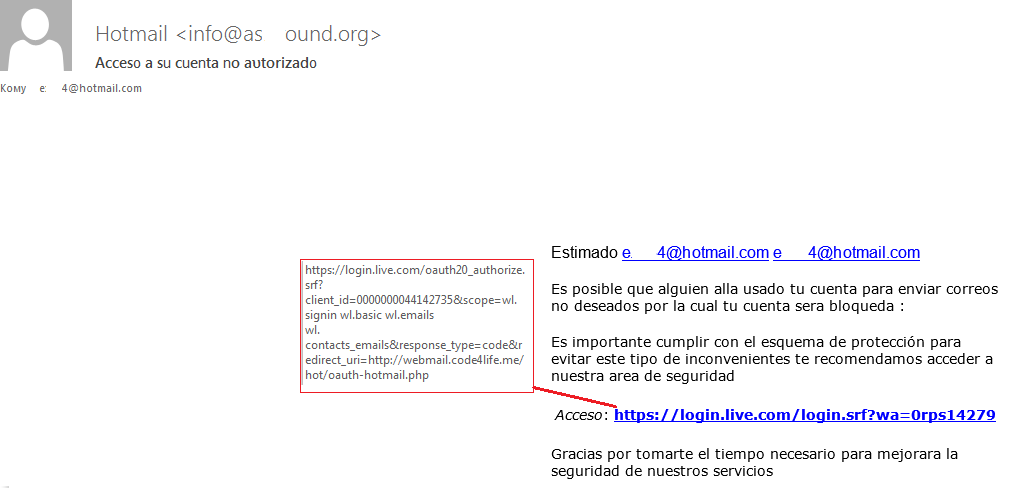
We have recently come across a method of getting personal information that was interesting from the technical point of view. Our customer received an email saying that someone had used his Live ID to distribute unsolicited email, so his account would be blocked. The email suggested that, to prevent the account from being blocked, the customer should follow the link and fulfill the service’s new security requirements.
This sounds very much like a typical phishing email. The victim is expected to click on the link that will take him to a fake site imitating the official Windows Live page, enter data which will be sent to the scammers, etc. However, to our surprise, the link from the scam email actually led to the Windows Live website and the cybercriminals did not make any attempt to get the victim’s login and password. Their scam was much more sophisticated than that.
The scam
Then why is it dangerous to follow the link if it does lead to the official Microsoft service?
The scam email
This is because the Live ID account can also be used for authorization with other services – Xbox LIVE, Zune, Hotmail, Outlook, MSN, Messenger, OneDrive, etc. The attack does not result in the fraudster getting direct access to these services on behalf of his victim, but it does enable the attacker to steal personal information contained in the user profiles for these services and subsequently use it for fraudulent purposes.
Having followed the link in the email, we are taken to the official live.com service, where we are asked to authenticate using our login and password.
After successful authentication, the user’s login and password are not intercepted by the fraudsters as one might suppose (and as it usually happens); the user does get authenticated on live.com. But after this they receive a curious prompt from the service:
Some application requests permission to automatically log into our account, view our profile information and contact list and access the list of e-mail addresses. By clicking “Yes” we assign it these rights – in effect providing its creators with our personal information, our contacts’ email addresses, our friends’ nicknames and real names, etc.
Do not give the right to access your personal data to applications that you do not know or trust
Tweet
Since in this case we know nothing about the application or its authors, we can only assume that the data collected will be used for fraudulent purposes. Once again – the login and password do remain confidential.
How it works
Technically, this is not very complicated. There is a special open protocol for authorization, OAuth, which allows resource owners to give third parties limited access to their protected resources without sharing their credentials. The protocol is commonly used by the developers of web applications for social networks if these applications require some data for their operation, such as the ability to access the contact list. It is convenient for users because once they are authenticated with the service they do not have to enter their credentials every time an application requests authorization.
This is the first time we have come across a phishing email used by fraudsters to put these techniques into practice
Tweet
The security flaws of the OAuth protocol have been known for quite a while: in early 2014, a student from Singapore described possible techniques for stealing user data after authentication. However, this is the first time we have come across a phishing email used by fraudsters to put these techniques into practice.
In our case, after clicking on the link hxxps://login.live.com/oauth20_authorize.srf?client_id=00xxx4142735&scope=wl.signin%20wl.basic%20wl.emails%20wl.contacts_emails&response_type=code&redirect_uri=hxxp://webmail.code4life.me/hot/oauth-hotmail.php, which was received in a scam email, a user is taken to the authentication page where (s)he is asked to assign certain rights to an application. The list of rights requested is encoded in the link’s parameters. If the user agrees, (s)he is redirected to a landing page (hxxp://webmail.code4life.me/hot/oauth-hotmail.php) whose URL includes an “access token” (hxxp://webmail.code4life.me/hot/oauth-hotmail.php?code=36cef237-b8f6-9cae-c8e4-ad92677ba) after the “code” parameter, which is then intercepted by the application right from the address bar. The “access token” is then used by the application to access protected resources. It is worth noting that the capabilities offered by OAuth are not limited to authentication and authorization. A token received during authorization can be used for integrating a web service’s or social network’s functionality into your own resource, including the ability to read and write posts, access the news feed, the Wall, etc.
Link parameters
If you take a closer look at the link, you can see the following parameters: wl.signin, wl.basic, wl.emails, and wl.contacts_emails. These parameters are used to encode the permission levels requested by the application:
- wl.signin – single sign-in enabling users who are logged into Windows Live to automatically log into any web site that supports this type of authorization;
- wl.basic gives permission to read basic information in the user profile, such as the user’s nickname, first and last name, sex, age, country of residence, as well as giving access to the user’s contact list;
- wl.emails – gives reading access to the user’s personal, preferred and business email addresses;
- wl.contacts_emails gives access to the email addresses of all people on the user’s contact list.
There are many other parameters, which give permissions to access the user’s and their contacts’ photos, date of birth, the list of meetings and important events. In fact, a scammer can use this information to create a person’s profile, including information on what the user’s activities are when going out, the user’s friends and people (s)he meets, etc. This profile can then be used for criminal purposes.
The victim’s information is gathered in order to send spam or to launch spear phishing attacks
Tweet
Further research enabled us to find a few similar phishing emails containing links to the official Microsoft service. In all cases, attackers asked the user to provide the same information (profile data, email addresses, contacts). Only the addresses of the landing pages hosting the scammers’ application were different.
hxxps://login.live.com/oauth20_authorize.srf?client_id=000000004C1xxx06&scope=wl.signin%20wl.basic%20wl.emails%20wl.contacts_emails&response_type=code&redirect_uri=http://soluciones-ntflix.com/web/oauth-hotmail.php
hxxps://login.live.com/oauth20_authorize.srf?client_id=000000004C1xxx3C&scope=wl.signin%20wl.basic%20wl.emails%20wl.contacts_emails&response_type=code&redirect_uri=http://registros-promos.com/web/oauth-hotmail.php
hxxps://login.live.com/oauth20_authorize.srf?client_id=00000000441xxx1B&scope=wl.signin%20wl.basic%20wl.emails%20wl.contacts_emails&response_type=code&redirect_uri=http://applications-registro.com/web/oauth-hotmail.php
hxxps://login.live.com/oauth20_authorize.srf?client_id=00000000441xxx17&scope=wl.signin%20wl.basic%20wl.emails%20wl.contacts_emails&response_type=code&redirect_uri=http://estimaciones-serv.com/web/oauth-hotmail.php
It should be noted that some applications designed for social networks also use the OAuth protocol.
Example of rights assigned to an application on Facebook
An application created by scammers might request the victim’s permission to publish posts and pictures on the Wall, to read and send private messages, to add entries in guest books. These features can be used to distribute spam or links to phishing or malicious sites.
Conclusion
In the case discussed above, information is most likely gathered in order to send spam to the contacts in the victim’s address book or to launch spear phishing attacks.
To avoid falling victim to scammers, do not follow links received by email or in private messages on social networks. Most importantly, do not give the right to access your personal data to applications that you do not know or trust. Before you agree, carefully read the descriptions of the account access rights which the application will get and assess the threat level. You can also search the Internet for information and feedback on the application requesting these rights. Any social networking site or web service also allows users to view the rights of currently installed applications in account/profile settings and cancel some of the permissions if necessary.
Example of Google access rights assigned to an application
If you have found out that an application is already distributing spam or malicious links on your behalf, you can send a complaint to the administration of the social networking site or web service and the application will be blocked. If you want to log on to a service or social networking site, it is best to go directly to the official website by manually entering its address in the browser. And, of course, keep the databases of your antivirus software with integrated anti-phishing protection up to date.























Fraudsters can have rights, too