
Last year, when I moved into my current home, there used to be an unprotected WiFi network available called ‘Constantine’. This is normal behavior almost everywhere around the world, but I thought it was funny when the network was renamed to ‘Buy your own net’ only a few days later. I suspect Mr Constantine grew tired of his neighbors piggybacking on his Internet link and wanted to send a message. I also suspect he didn’t know how to enable encryption in the first place, because another week later, he finally turned on WEP. He kept the name, though.
I think the Google sniffing story from earlier today is related to exactly that:
http://googleblog.blogspot.com/2010/05/wifi-data-collection-update.html
During a recent investigation by the Data Protection Authority from Hamburg, it came to light that Google has been accidentally sniffing the traffic on WiFi networks with its Google cars, during the routine mapping of the roads. If your house had an open WiFi network and a Google car passed near it in the past months, then it’s likely that bits of your network traffic have ended in Google’s hands.
So, how do you properly secure your WiFi network so that your neighbors and Google do not tap into it?
Here’s a few pointers:
1. Disable the broadcasting of the network SSID
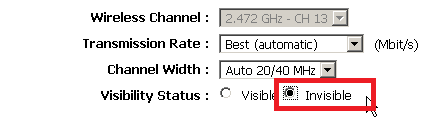
Broadcasting the network SSID can make it easier for attackers to guess your password, or for you to become the target of automated sniffing or profiling attacks.
2. Turn on the WPA2 encryption with AES
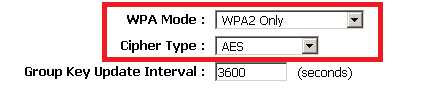
WPA and WEP are the older, less secure encryption standards. To get the best level of protection, in some cases, the best network speed (that is true with D-Link routers for instance), use WPA2 with AES.
3. Choose a complex password, with both Uppercase and lowercase letters, numbers and a few special chars such as “#, ! and _”
A complex password will make bruteforce attacks unlikely to succeed.
4. Change the network password every now and then
This way, even if the password has been compromised, you can limit the amount time when the attacker can use your network. Make sure the password is not predictable, for instance, never use the current month, or, the current year.
5. Reduce the network power to a minimum that still makes it available where you need it in your house
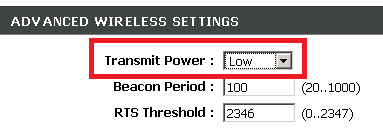
By setting the network to the lowest power setting you make sure that your neighbors from 1Km away do not have any chance of trying to access your resources.
6. Consider purchasing a modern WiFi router, which fully supports WPA2, has a firewall and can have variable broadcast power.
Many old routers have broken WPA implementations or suffer from speed problems when using it. Additionally, they lack many security features. Consider buying a modern, flexible and secure WiFi router. Make sure you update its firmware often.
By following the above advice, your data should be reasonably safe while you still get a decent level of usability!
Enjoy the signal!





















Google Sniffing Beta ™