
A few days ago we wrote about a new variant of the Stuxnet worm’s rootkit component, signed not with Realtek’s digital signature, but with one owned by JMicron. Costin posted about it in detail.
The media jumped on the news, and there was a lot of talk about “New worm variant discovered”. However, the situation isn’t quite as simple as the headlines made out.
There wasn’t a clear answer to the main question i.e. where’s the worm which the signed driver would have come from? The fact that the driver was created on 14 July could indicate that a new variant of the worm, potentially with new functionality, was out in the wild.
However, all of our attempts to find the dropper of the second rootkit driver (there are meant to be two) came to nothing.
Over the last few days, all the discussions have boiled down to two possible explanations: either cybercriminals stole the digital certificates using a Trojan, or it was the work of an insider. Our failure to find the dropper or second driver, though, makes the whole story all the more complicated.
So we decided to look at some statistics: how many times has the Kaspersky Security Network detected Rootkit.Win32.Stuxnet.c (the driver signed with the JMicron certificate)? The numbers are discouraging – since 20 July, the module’s been detected all of twice, once in Russia and once in Ukraine. These figures look pretty silly when compared to the detection statistics for the rootkit component signed with the Realtek signature.
Verisign has now revoked the JMicron certificate, making it invalid. Our allowlisting database contained 124 programs which had been signed using the certificate – all of them, of course, were clean.
At the moment, I’m not drawing any conclusions about the origins of this mythical driver. I don’t doubt that it is a modified variant of mrxcls.sys. We’re still looking for whatever is launching it, or computers which it’s infected.
If we look at the stats relating to the initial Stuxnet variant, they show epidemics in India, Iran, and Indonesia. The number of infected computers increases by about a thousand every day, and this is only what our monitoring systems show us. In other words, it’s merely the tip of the iceberg.
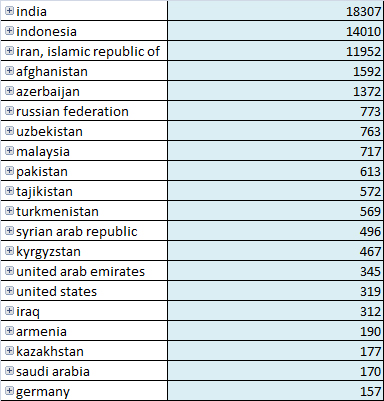
Apart from the three countries hit by Stuxnet, Azerbaijan and Afghanistan have also been heavily affected, with more than a thousand infected machines each.
The geographical spread of the Trojan, together with the “missing” variant, has given us all a lot to think about.






















Myrtus and Guava, Episode 4