
Overview
- Spam accounted for an average of 84.4% of the total volume of email traffic
- Links to phishing sites were found in 0.02% of all emails
- PayPal is the organization most frequently targeted by phishing attacks. Social networking site Facebook is still in the Top 5
- The number of graphical attachments in spam emails came to 10.3% of the total mail volume
- Spammers used emails designed to look like legitimate notifications from social networking sites and email service providers to advertise Viagra and spread malware
- The USA, India and Vietnam were the most prevalent sources of spam during the quarter, whilst the percentage of spam sent from Latin America increased considerably
Spam in mail traffic

The percentage of spam in mail traffic
The percentage of spam in mail traffic during the second quarter of 2010 came to 84.4%, a reduction of 0.8 percentage points on the previous quarter. The highest levels of spam were recorded on 18 April and 9 May at 89.8%, while the low for the quarter was 79.2% on 20 April.
The first half of May saw the largest sustained volumes of spam in mail traffic, primarily because the amount of legitimate email is typically less during the holiday season.
Sources of spam
The distribution of spam sources by region

The distribution of spam sources by region
Asia continues to be the world’s foremost region for the distribution of spam. In April, 40.5% of all spam originated from Asian countries, before decreasing somewhat later on. Overall, during the period April to June 2010, Asian countries were responsible for distributing 32.8% of the total spam volume, which is slightly more than the 31.7% sent from this region during the first quarter of the year. Furthermore, the amount of spam originating in Asia decreased from month to month. Meanwhile, the amount of unwanted correspondence from Latin American countries was clearly on the rise. Readers may recall that in 2009, the amount of spam sent from South America amounted to 15%, and fell to 10.5% in the first quarter of 2010. The total for the second quarter exceeded that of not only the first quarter of 2010, but the whole of 2009 also, with 16.3% of all spam originating from Latin America.

The fluctuations in spam originating in Asia and Latin America
During the first quarter of 2010, Kaspersky Lab noted that if a comparison were drawn between the spam output of Asia and Europe (including Western Europe, Eastern Europe and Russia), then the European region’s output would be higher. However, this quarter the amount of spam sent from Eastern Europe fell by 5.5 percentage points. As a result, Asia continues to dominate as the leading source of spam, even when compared to the spam output of Europe as a whole (Asia 32.8%, Europe 31.5%).
The distribution of spam sources by country
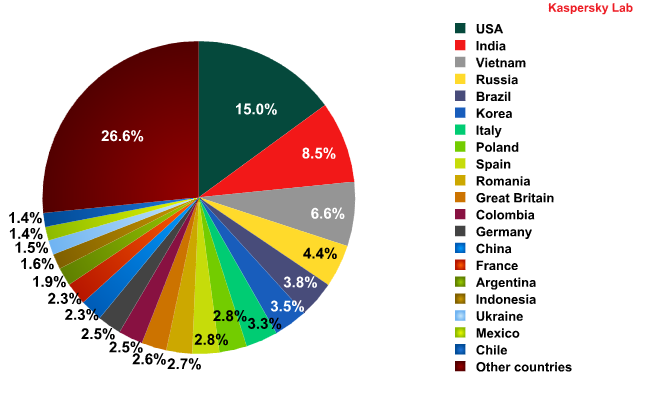
Countries that are sources of spam
The USA went firmly into the lead this quarter with 15% of all spam, while India remains a steady second place with 8.5%. Vietnam climbed two places to come in third in the chart. However, there was plenty of jockeying for position throughout the quarter. In April, the USA, India, and Vietnam were neck and neck with 12.3%, 11.7%, and 11.6% respectively, while in May, the USA unequivocally stepped into the lead with 20.8% of all spam.
Quite unexpectedly, Italy (3.3%) and Spain (2.8%) joined the Top 10 sources of spam. Last quarter, these countries were ranked a lowly 14th and 15th place respectively on the chart. China was found to be the origin of just 2.3% of all spam and did not make a comeback to the Top 10 sources of spam, leading Kaspersky Lab to believe that the strict new Internet laws imposed in China do have their good points.
The size of spam emails

The average size of spam emails
The bulk of spam continues to be comprised of emails of 5 KB or less. However, compared to the first quarter of the year, the amount of these lightweight emails did decrease somewhat. Nevertheless, they still account for over half of all spam emails. Furthermore, the amount of spam in the 5-10 KB range did increase slightly. More likely than not, this was due to the very many emails carrying spam advertisements for Viagra and fake luxury goods, featuring small graphics or long fragments of random text.
Types of attachments in spam emails

The different types of attachments in spam emails
In the second quarter of 2010, 75.7% of all spam emails contained plain, unformatted text. Over one-half of all spam emails contained a section in HTML. For the first time, the amount of graphical attachments in GIF format exceeded the number of JPEG attachments and amounted to 10.1%. As usual however, many spam emails contained both GIF and JPEG attachments.
In general, the amount of spam containing graphical attachments came to 10.3%, which is 1.4 percentage points less than in the previous quarter. The largest amounts of graphical spam (12.53%) were recorded in April.

The percentage of spam emails containing graphical attachments
Phishing
The amount of phishing emails in email traffic during the second quarter of 2010 was quite small. After a sharp decrease from 0.87% to 0.03% during March, the amount of phishing emails continued to fall, reaching just 0.02% of all mail traffic at the close of the second quarter of 2010.
The e-money company PayPal remains way ahead of the rest of the Top 10 most targeted organizations, being the focus of 60.4% of all phishing attacks during the quarter. In June, this number came close to 70%.

The Top 10 organizations targeted by phishers
Other frequently targeted organizations include eBay with 9.36% of all attacks, HSBC with 6.51%, Facebook with 6.03% and Google’s search engine with 2.84%. Kaspersky Lab has noted that phishers are increasingly focusing their efforts on social and entertainment websites. In addition to Facebook, attacks have targeted MySpace, Orkut and Habbo, along with the online games WoW and Zynga. The STEAM gaming service has come in for some unwelcome attention too.
The phishers’ Achilles heel lies in the links that they place in the spam emails. While it may be possible to persuade a user that an email really did, for example, come from their bank, if the user notices that the link takes them to a completely different website altogether, they will probably see through the ruse and disregard the email. This is why phishers are trying to disguise their links by making them as similar to the originals as possible:
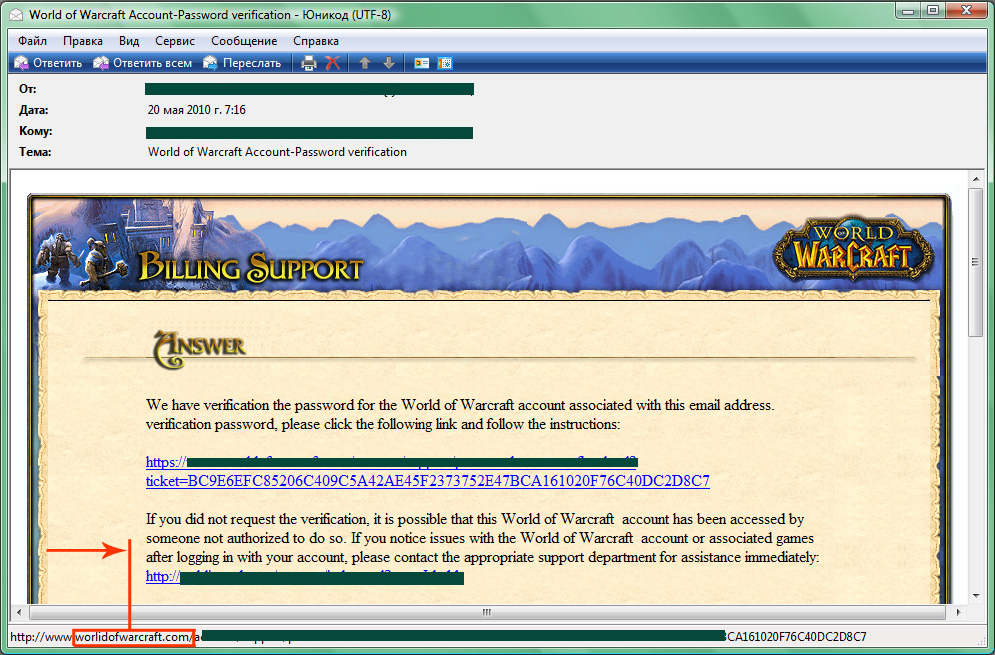
An example of an email with a phishing link that resembles a legitimate address
During the last quarter, phishers have attempted to fool users by using domain names that attempt to instill a sense of security in their victims:

A phishing link that leads to the domain guardianangels.co.za
Malicious attachments in spam
During the second quarter of 2010, malicious files were found in 1.87% of all emails, which is 1.19 percentage points more than in the first quarter.
The chart below lists the malicious files that were most commonly found in emails during the second quarter of this year.
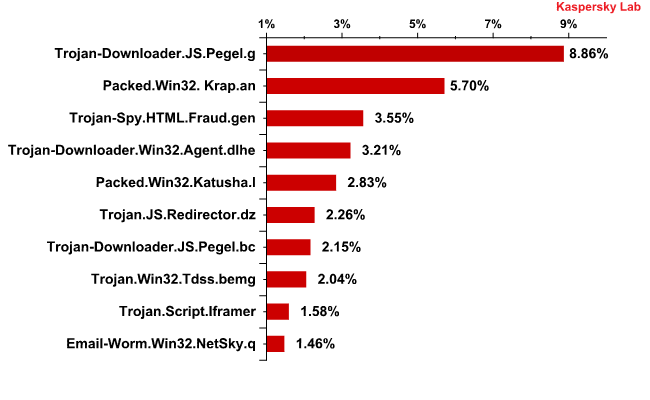
The Top 10 most common malicious files in email
Ranked in first place is Trojan-Downloader.JS.Pegal.g. Another variant of this threat, Trojan-Downloader.JS.Pegel.bc, comes in at seventh place. These types of Trojans are HTML pages that contain scenarios written in JavaScript. Trojan downloaders are designed to redirect users to a cybercriminal’s webpage containing both advertising content and malicious code that will be downloaded onto the user’s computer. Trojans from the ‘Redirector’ family all behave in the same manner. One of these, Trojan.JS.Redirector.dz, was ranked the sixth most prevalent threat in the second quarter. Another Trojan, called Trojan.Script.Iframer, works in the same way and is ninth place.
It is worth noting that all of the threats mentioned above gained their high rankings due to a massive attack in June, which will be addressed in more detail below. Prior to the June attack, none of these email threats had appeared in the Top 10.
The second most prevalent threat was the packer, Trojan.Win32.Pakes.Krap.an. A similar Trojan, Packed.Win32.Krap.x, led the last quarter’s ranking. In addition to Packed.Win32. Krap.an, another packer also made the Top 10: Packed.Win32.Katusha.l. This appeared in fifth place, with similar programs often being used to pack counterfeit antivirus programs.
Third place on the list went to the email threat, Trojan-Spy.HTML.Fraud.gen. This Trojan took second place in the previous quarter and works by exploiting a vulnerability found in Microsoft Internet Explorer versions 5.x and 6.x. This threat was primarily designed to collect confidential information that a user might enter on websites.
Malicious files were spread via emails containing a wide variety of offers. These offers included purported notifications from email and social networking providers encouraging users to install an update or change their password, fake e-greetings, and supposed invoices from email service providers. Other tactics included the sending of fake emails with subject lines bearing ostensibly scandalous news items and promises of, among other things, photographs of beautiful, scantily clad women in the attachments. Occasionally too, the virus writers ran short of bright ideas and resorted to laconic emails such as the following:

One lazy spammer’s half-hearted attempt at an email
containing a malicious attachment
June: massive attack
As noted above, the Trojan-Downloader.JS.Pegel.g threat was the most prevalent in June, accounting for 23.3% of all the malicious files found in email. All of the blame can be attributed to that one, mutating mass mailing.
An email was distributed that was made to look like a notification from social networks, email providers and popular websites such as Facebook, Twitter, Digg, Amazon, Windows Live, YouTube, Skype, and Wikipedia. These emails were very reminiscent of phishing attempts. However, if a user clicked on the link, they would be taken to a hacked site, from where a malicious script would be downloaded. This script then redirected the user to a site advertising medication or fake luxury goods. Unlike phishing emails, where only one link usually points to a malicious user’s site, in this case all of the links in the email led to one and the same page.

Examples of an email containing Pegel. The links in this email
led to a website advertising Viagra.
One distinguishing feature of this mass spam mailing was the presence of an HTML attachment in the emails, or links that would take a user to a webpage containing Pegel, Iframe, or Redirector. Once obfuscated, JavaScript would redirect the user to the cybercriminal’s website. In most cases, this complex system was used to draw victims to a website advertising Viagra or fake luxury goods. However, in some cases, the destination websites contained malware, including Backdoor.Win32.Bredolab. A similar scheme was used by scammers last year. For more details about last year’s tactics, see the following article: securelist.com.
Technical tricks
Variety was the spice of life for medication-themed spam during the last quarter. In addition to the ‘redirect’ method described above, in some cases, graphical spam would be downloaded directly into the body of the email. These images were typically fake notifications from well known resources:
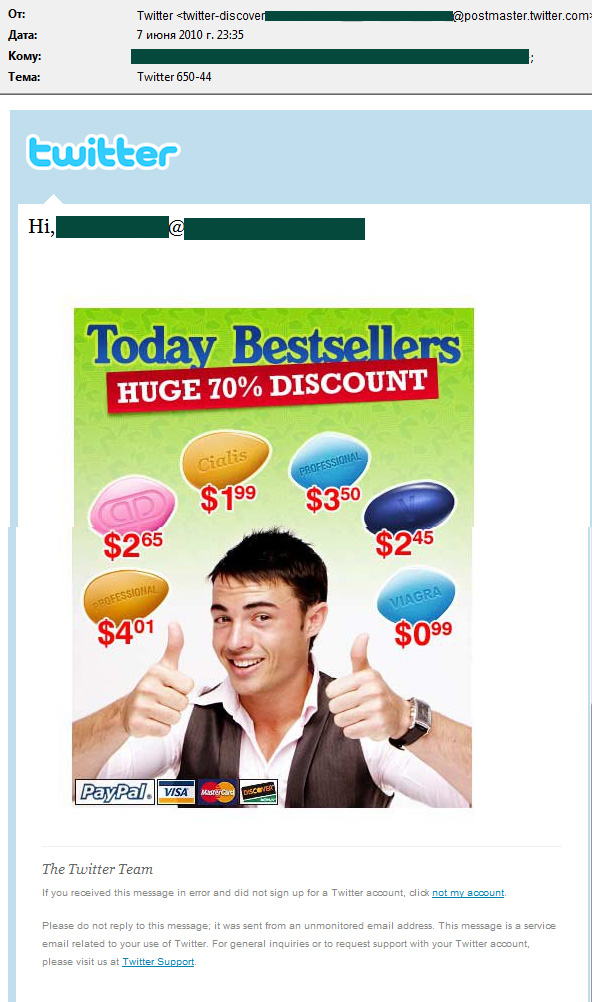
Spam advertising in an email designed to resemble a Twitter notification
Remarkably, in the example shown above not only the primary link in the graphic, but all of the others too, including ‘not my account’ and ‘Twitter support’, led to the spam website of an online pharmaceuticals store.
Other medication-themed mailings managed to sneak past spam filters when spammers injected large fragments of text taken from various literary works or articles into the email. The advertisement itself was visible in the graphic that was downloaded from a free hosting service. Happily, these hosting services blocked part of these graphics and as a result, a user was shown a warning about the dangers of spam instead of the spammer’s graphic.

An example of a spam advertisement for Viagra and an email
with a graphic blocked by the hosting service
Furthermore, in some cases, spammers attempted to disguise the URL to which redirected users would be taken. Over this last quarter, spammers used the Google Translate service for this purpose. The link looked like this:
http://www.google.com.et/translate?js=y&prev=_t&u=http %3A%2F%2F*****.info&sl=auto&tl=en
As you can see, in order to increase the chances of bypassing a filter, some spam links used ASCII coding, shown highlighted in red. If an unwary user followed the link, they would initially be taken to a webpage displaying a translation service header, before being redirected to a spam website.
Spam categories

The distribution of spam categories
The most common spam category in the second quarter of 2010 was Education. This category includes offers for different training courses and seminars. Health and medication spam dropped down from second place, making way for Travel and tourism which has became much more prevalent over the past three months. In April, the percentage of emails in this category reached 21.1%, although later on the amount of these types of emails began to run out of steam.

The percentage of emails in the Travel and tourism spam category
Throughout the quarter, Kaspersky Lab noticed a rise in the number of fraudulent emails in spam. In June, the percentage of Computer fraud spam reached 14.5%, with most of it being comprised of fake notifications from social networks that redirected traffic to websites advertising Viagra. These types of mailings were discussed in the sections above.

The percentage of Computer fraud spam
The Health goods and medication category only it made it to third place during this past quarter. On the one hand, this was due to the fact that a portion of emails advertising Viagra fell into the Computer fraud category. On the other hand, another important factor is that when compared to the previous quarter, the percentage of other categories such as Education, Travel and tourism and Other goods and services also increased. Overall, the dynamics among the different categories of spam demonstrate that once the crisis ends, the amount of traditional ‘legitimate’ spam will rise, while the amount of ‘affiliate’ spam will start to decrease.
The World Cup
Spammers just couldn’t resist the opportunity to exploit the World Cup. However, readers should note that spam that took advantage of the popularity of the championship was considerably less than is normally expected for events of this scale. As ever, the hot topics of the day were used to entice the unwary into becoming involved in fraudulent schemes aimed at spreading malware. Most of the emails that mentioned the World Cup were so-called Nigerian letters or fake notifications about lottery winnings, some of which contained malicious programs.

Examples of emails taking advantage of World Cup fever
In the first example, we can see that the attachment just contains more of what is in the body of the email itself: a fake notice about lottery winnings. Anyone opening the attachment from the second email will not be so lucky: the HTML attachment contains a Trojan.JS.Redirector.dw script that will redirect the user to a cybercriminal’s site.
Conclusion
In the second quarter of 2010, spam sent from countries in Asia and Latin America accounted for over half of all spam traffic. Earlier, we noted a shift in the sources of spam to these regions. Now we can say with some certainty that this trend will remain for the foreseeable future. This situation is due in part to the lack of any effective legislation in Asia and Latin America, coupled with low levels of computer and Internet literacy that has led to a popular disregard for information security issues. These unprotected computers are the ones that are most at risk of becoming infected and subsequently being incorporated into a botnet.
The principal target among those organizations most frequently subjected to phishing attacks was PayPal. However, social networking sites are quickly becoming the spammer’s target of choice, with Facebook being on the receiving end of the bulk of the attacks against social networks.
Kaspersky Lab has often written about the criminalization of spam and of the collaboration that exists between spammers, scammers and virus writers. In the second quarter of 2010, this trend was clearly demonstrated in a spam mailing that took place in June. The spam emails used a classic phishing tactic: they were an exact copy of a notification from a social network or email service provider. Furthermore, by clicking on the link in the email, the user was redirected to a website advertising Viagra or fake luxury goods and sometimes to a site containing malware. These types of schemes have already become commonplace and will continue to grow in popularity in the future.
Kaspersky Lab would like to once again advise Internet users not to click on links in spam emails. We strongly recommend that software updates be downloaded and installed as soon as they become available and that users’ antivirus programs are regularly updated.





















Spam in the Second Quarter of 2010