
Targeted attacks and malware campaigns
More wipers
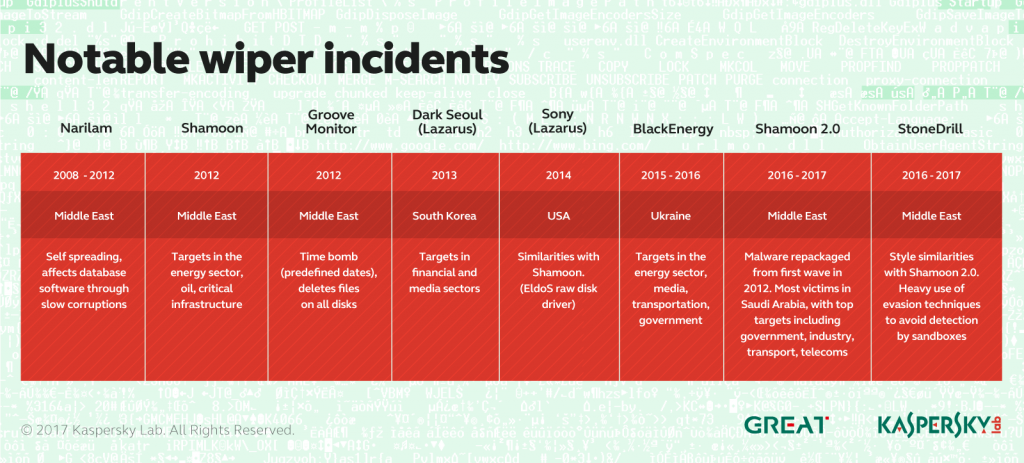
The aim of most targeted attack campaigns is to steal sensitive data. However, this isn’t always the goal. Sometimes attackers erase data instead of – or as well as – trying to gain access to confidential information. We’ve seen several wiper attacks in recent years. They include Shamoon (also known as ‘Disttrack’), believed to have been used to erase data on more than 30,000 computers at Saudi Aramco in 2012, and Dark Seoul, used in the attack on Sony Pictures in 2013.
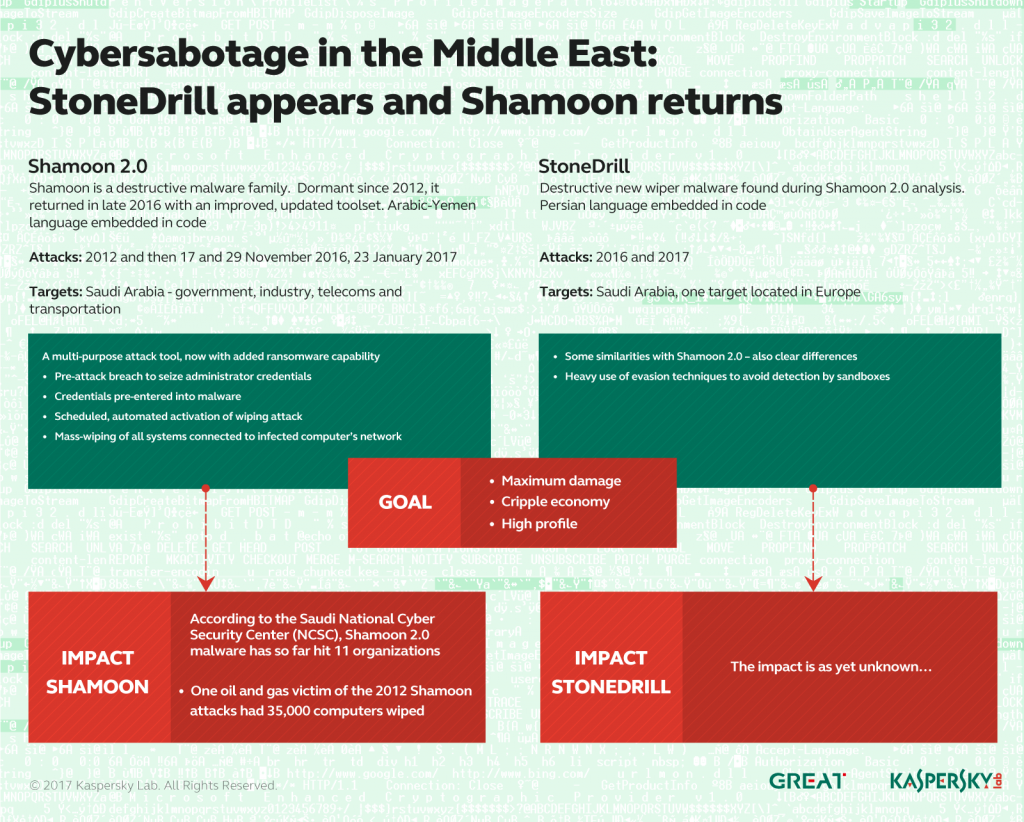
Shamoon re-appeared in November 2016, targeting organisations in various critical and economic sectors in Saudi Arabia. So far we have observed three waves of attacks using the Shamoon 2.0 malware – activated on 17 November 2016, 29 November 2016 and 23 January 2017.
While the attacks share many similarities with the earlier wave of attacks, they now feature new tools and techniques. The attackers start by obtaining administrator credentials for the target network. Then they build a custom wiper (Shamoon 2.0) which uses the stolen credentials for lateral movement across the organisation. Finally, the wiper activates on a predefined date, leaving the infected computers unusable. The final stage of the attack is completely automated and doesn’t rely on communication with the attacker’s C2 (Command-and-Control) center.
Shamoon 2.0 also includes a ransomware component. This has yet to be used in the wild, so it’s unknown whether the attackers would use this part of the platform for financial gain or for idealistic purposes.
While investigating the Shamoon attacks, we discovered a previously unknown wiper. This malware, which we’ve named StoneDrill, also seems to target organisations in Saudi Arabia. There are similarities in style to Shamoon, with additional features designed to help it evade detection. One of the victims of StoneDrill, observed via the Kaspersky Security Network (KSN) is located in Europe (and operates in the petro-chemicals sector), suggesting that the attackers might be expanding their wiping operations beyond the Middle East.
The most significant difference between the two relates to the wiping process. Shamoon uses a disk driver for direct access to the disk, whereas StoneDrill injects the wiper directly into the victim’s preferred browser.
StoneDrill also shares similarities with an APT group known as NewsBeef (also known as ‘Charming Kitten’), so-called because of its use of the Browser Exploitation Framework (BEeF). These similarities include familiar WinMain and OS signatures, update commands and C2 server names. It isn’t known whether the groups behind Shamoon and StoneDrill are the same, or are just aligned in terms of interests and the regions they target – the latter seems most likely to us.
In addition to the wiping module, StoneDrill also includes a backdoor that has been used to run espionage operations against a number of targets.
You can find the full report on Shamoon 2.0 and StoneDrill here. By subscribing to our APT intelligence reports, you can get access to our investigations and discoveries as they happen, including comprehensive technical data.
EyePyramid
As we’ve seen before, targeted attacks don’t have to be technically advanced in order to be successful. In January 2016, the arrest of two suspects by Italian police brought to light a series of cyber-attacks that targeted prominent politicians, bankers, freemasons and members of law enforcement agencies.
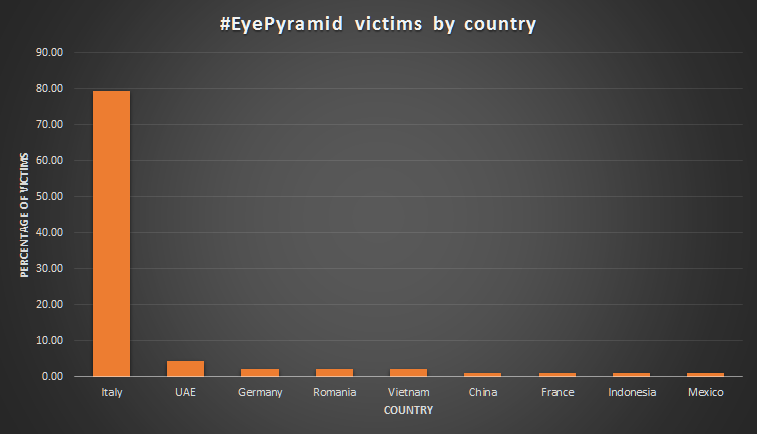
The malware used in the attacks, called ‘EyePyramid’, was unsophisticated, but nevertheless successful enough to enable the attackers to gain access to all resources on their victims’ computers. The police investigation revealed 100 active victims in the server used to host the malware, but there were indications that the attackers had targeted around 1,600 victims in the last few years. Their victims – located mostly in Italy – included law firms, consultancy services, universities and Vatican cardinals.
The Italian police report didn’t include technical details about how the malware was spread – other than revealing that spear-phishing was used. However, it did identify a number of C2 servers and e-mail addresses used by the attackers to exfiltrate stolen data. Using this information, we created a YARA rule, based on custom e-mail addresses, C2 servers, licences for the custom mailing library used by the attackers and specific IP addresses used in the attack. Then we ran it through our systems to see if it matched any known samples. Out initial YARA rule highlighted two samples which enabled us to create a more specific YARA rule that identified a further 42 samples in our collection. A further search revealed more details about EyePyramid. The attacks relied on social engineering to trick victims into opening and running infected files attached to the spear-phishing e-mails. The attachments used were ZIP and 7ZIP archives which contained the malware. The attackers used multiple spaces to try and mask the extension of the file – underlining the low level of sophistication of the attacks.
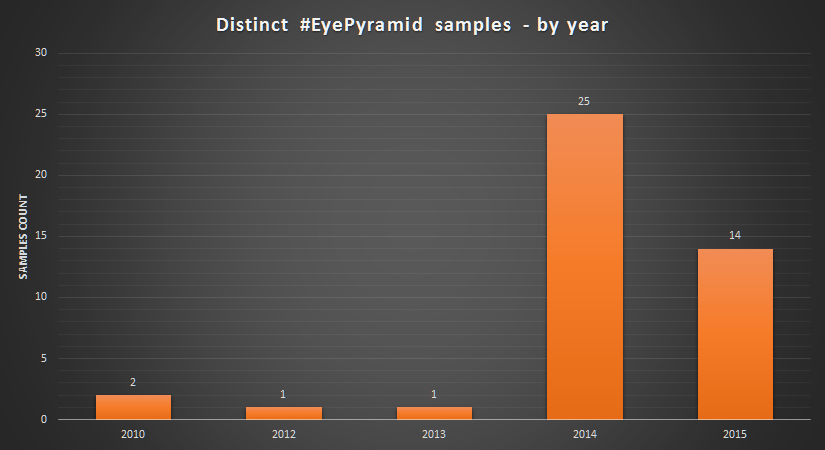
Based on the compilation time-stamps of the samples, which appear to be legitimate, most samples used in the attacks were compiled in 2014-15.
It’s clear that cybercriminals can achieve success even when the malware they use is neither sophisticated nor hard to detect. From the poor OPSEC (operational security) employed in the campaign (for example, using IP addresses associated with their own company and discussing victims in regular phone calls and using WhatsApp), it’s clear that the attackers were amateurs. Nevertheless, they were able to operate for many years and managed to steal gigabytes of data from their victims.
You can read our full report on EyePyramid here.
Breaking the weakest link of the strongest chain
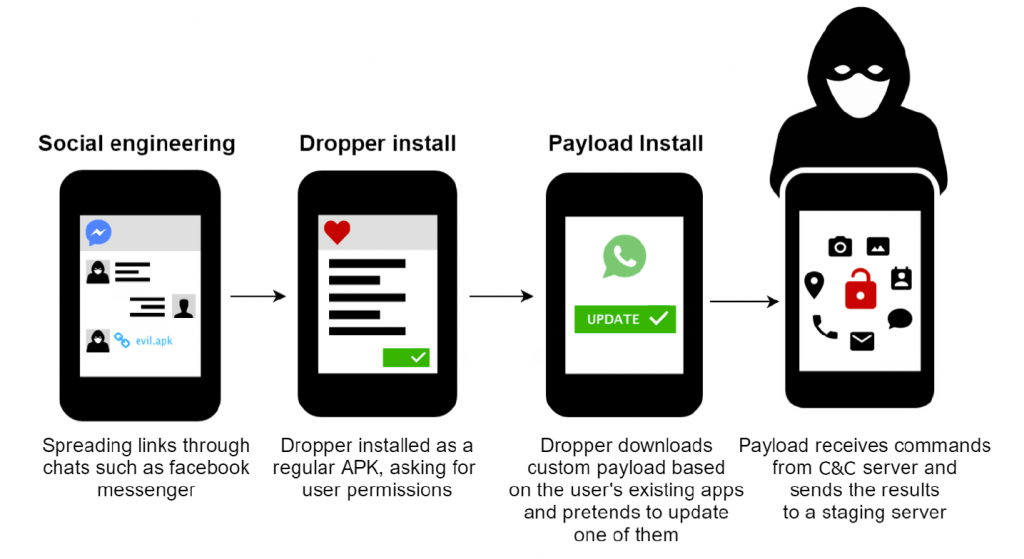
In the middle of 2016 more than 100 Israeli servicemen were targeted by a cunning threat actor. The attack compromised their devices and exfiltrated data to the attackers’ C2 server.
The IDF (Israeli Defense Forces) C4I and the IDF Information Security Department unit, with Kaspersky Lab researchers, obtained a list of the victims – all IDF servicemen serving around the Gaza strip.
This campaign, which experts believe is still in its early stages, targets Android OS devices. Once the device has been compromised, a process of sophisticated intelligence gathering begins, exploiting the phone’s video and audio capabilities, SMS functions and location.
The attacks are unsophisticated, relying heavily on social engineering techniques. The attackers lure their victims into installing a malicious application, while continuously attempting to acquire confidential information using social networks: the group seems particularly active on Facebook Messenger. Most of the avatars used by the attackers (virtual participants in the social engineering stage of the attack) lure the victims using sexual themes: for example, asking the victim to send explicit photographs and, in return, sending fake photos of teenage girls. The avatars pretend to be from different countries such as Canada, Germany, Switzerland and others.
The victim is tricked into downloading an app from a malicious URL. The app collects data from the victim’s phone, including general information (network operator, GPS location, IMEI, etc.), contacts, browsing history, SMS messages, pictures. The app is also able to record video and audio.
The IDF, which led the research along with Kaspersky lab researchers, believes that this is just the opening shot of a wider campaign that is designed to capture data on how ground forces are distributed, the tactics and equipment the IDF uses and real-time intelligence.
You can read our full report on this campaign here.
The non-persistence of memory
During an incident response, security specialists hunt for any artefacts that attackers have left behind in the victim’s network. This includes inspecting log files, looking for files on the hard drive, looking at the registry and checking memory.
However, each of these has a different ‘shelf-life’: in other words, the clues will be available to an analyst for a shorter or longer time, depending on where they’re located. Data stored on a hard drive will probably be available to a forensic analyst for a long time: although, as we saw with Duqu 2.0, sophisticated malware might deliberately remove all traces from the hard drive after installation, leaving itself in memory only. This is why memory forensics is critical to the analysis of malware and its functions.
Another important aspect of an attack is the tunnels that are installed in the network by an attacker. Cybercriminals (such as Carbanak and GCMAN) might use PLINK for this purpose; Duqu 2.0 used a special driver.
In our predictions for 2017 we forecast an increase in ephemeral infections – memory-resident malware intended for general reconnaissance, with no interest in persistence. In highly sensitive environments, where stealth is essential, attackers might well be satisfied to operate until the malware is cleared from memory during a re-boot, since this will reduce the likelihood of the malware being detected and their operation being compromised.
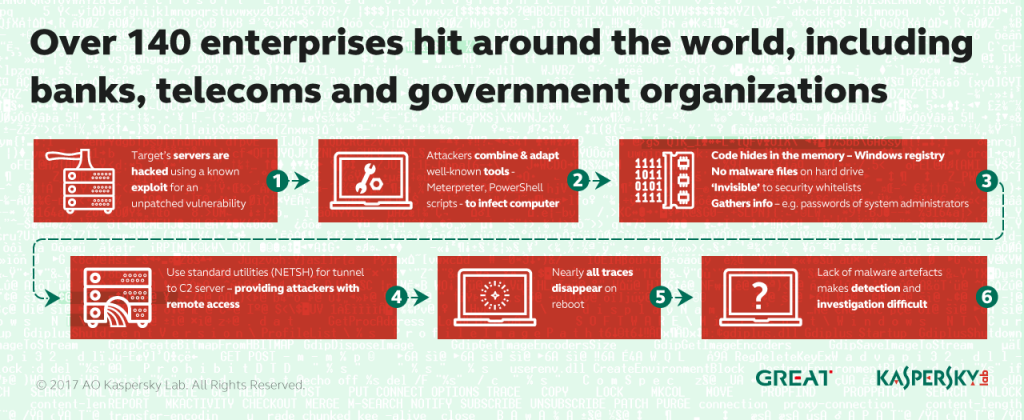
During a recent incident response our experts found that both memory-based malware and tunnelling had been implemented in a bank attack using standard Windows utilities such as SC and NETSH. The threat was originally discovered by the bank’s security team after they detected Meterpreter code inside the physical memory of a domain controller. We participated in the forensic analysis following this detection and discovered the use of PowerShell scripts within the Windows registry. We also discovered that the NETSH utility was used for tunnelling traffic from the victim’s host to the attacker´s C2.
You can read the details of our investigation here.
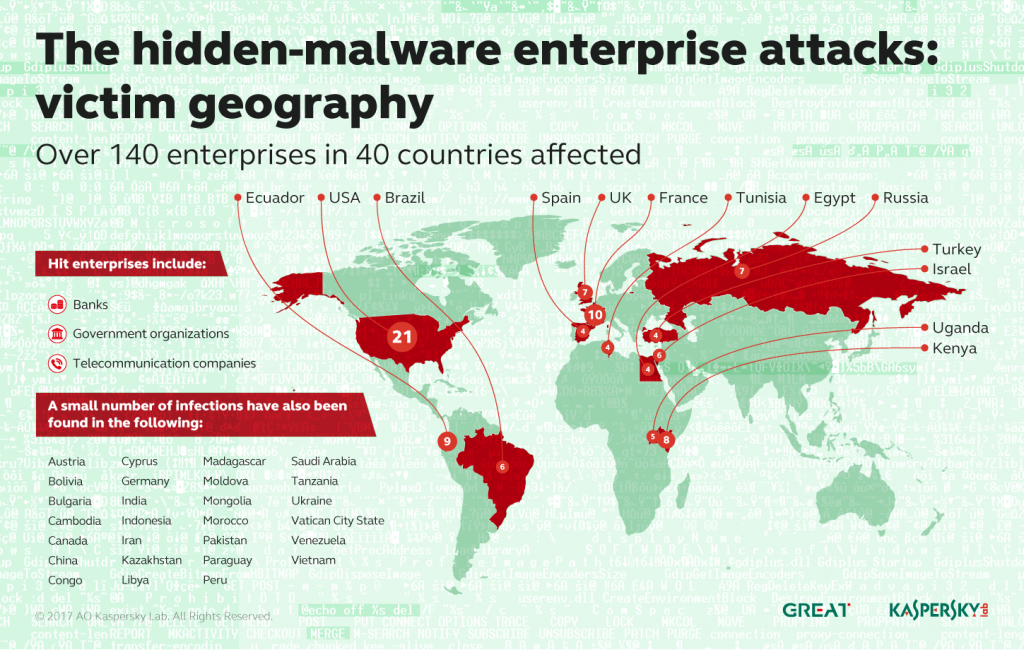
Using the Kaspersky Security Network we found more than 100 enterprise networks infected with malicious PowerShell scripts in the registry.
We don’t know if they were all infected by the same attacker. During our analysis of the affected bank we learned that the attackers had used several third level domains and domains in the .GA, .ML and .CF ccTLDs. The benefit, for the attackers, of using such domains is that they are free and don’t include WHOIS information after the domain expiration. The fact that the attackers used the Metasploit framework, standard Windows utilities and unknown domains with no WHOIS information makes attribution almost impossible. The closest groups with the same TTPs are Carbanak and GCMAN.
Techniques like this are becoming more common, especially in attacks against financial institutions. Exfiltration of data can be achieved using standard utilities and some tricks, without the need for malware. Such ephemeral attacks highlight the need for sophisticated, proactive technology in anti-malware solutions, such as Kaspersky Lab’s System Watcher.
KopiLuwak: a new JavaScript payload from Turla
The Russian-speaking APT group Turla (known variously as ‘Snake’, ‘Uroburos’, ‘Venomous Bear’ and ‘KRYPTON’) has been active since at least 2007 (and maybe even longer). Its activities have been traced to many high-profile incidents, including the 2008 attack against the US Central Command (the Buckshot Yankee incident) and, more recently, the attack against the Swiss military contractor, RUAG. We’ve discuss its activities on a number of occasions (here, here, here and here). The group intensified its activities in 2014, targeting Ukraine, EU-related institutions, governments of EU countries, global foreign affairs ministries, media companies and possibly corruption-related targets in Russia. In 2015 and 2016 the group diversified its activities, switching from the Epic Turla watering-hole framework to the Gloog Turla framework, which is still active. The group also expanded its spear-phishing activities with the Skipper/WhiteAtlas attacks, which made use of new malware. Recently, the group has intensified its satellite-based C2 registrations ten-fold compared to the 2015 average.
In January, John Lambert from Microsoft (@JohnLaTwC) tweeted about a malicious document that dropped a ‘very interesting .JS backdoor‘. Since the end of November 2016, Kaspersky Lab has observed Turla using this new JavaScript payload and specific macro variant. This is a technique we’ve observed before with Turla’s ‘ICEDCOFFEE’ payloads (detailed in a private report from June 2016 which is available to customers of Kaspersky APT Intelligence Services). While the delivery method is somewhat similar to ICEDCOFFEE, the JavaScript differs greatly and appears to have been created mainly to avoid detection.
The targeting of this new malware is consistent with previous campaigns conducted by Turla, focusing on foreign ministries and other governmental organizations throughout Europe. However, the frequency is much lower than ICEDCOFFEE, with victim organizations numbering in the single digits (as of January 2017). We strongly believe that this new JavaScript will be used more heavily in the future as a first-stage delivery mechanism and victim profiler.
The malware is fairly simplistic but flexible in its functionality, running a standard batch of profiling commands on the victim and also allowing the attackers to run arbitrary commands via Wscript.
Full details on KopiLuwak can be found here.
The document contains a malicious macro that’s very similar to macros used previously by Turla to deliver Wipbot, Skipper, and ICEDCOFFEE. The Turla group continues to rely heavily on embedded macros in Office documents. This might seem to be a basic tactic for such a sophisticated attacker, but it has helped them to compromise high-value targets. We would advise organisations to disable macros and not allow employees to enable such content unless it’s absolutely necessary.
The lure document above shows an official letter from the Qatar Embassy in Cyprus to the Ministry of Foreign Affairs in Cyprus. Based on the name of the document, ‘National Day Reception (Dina Mersine Bosio Ambassador’s Secretary).doc’, we presumed it may have been sent from the Qatar Ambassador’s secretary to the Ministry of Foreign Affairs, possibly indicating that the Turla group already had control of at least one system within Qatar’s diplomatic network.
The best defence against targeted attacks is a multi-layered approach that combines traditional anti-virus technologies with patch management, host intrusion detection and a default-deny allowlisting strategy. According to a study by the Australian Signals Directorate, 85 per cent of targeted attacks analysed could have been stopped by employing four simple mitigation strategies: application allowlisting, updating applications, updating operating systems and restricting administrative privileges.
Malware stories
Stand and deliver: your money or your files!
In eighteenth century Britain (and elsewhere) travellers could be waylaid by a highwayman – a thief who held up coaches on the public highway and demanded that those on board hand over their money and other valuables. The highwayman would typically issue the challenge – ‘Stand and deliver: your money or your life! Ransomware is a version of such highway robbery for the digital age – with the difference that it’s our data that is held hostage and the ‘highwayman’s’ ransom demand is displayed on the screen.
There were more than 1,445,000 ransomware attacks in 2016, on businesses as well as individuals. The huge growth we’ve seen in recent years is fuelled by the success that cybercriminals have had with this type of malware – ransomware is easily monetised and involves a low investment cost per victim.
Out of the 62 new crypto-ransomware families that we discovered last year, at least 47 were developed by Russian-speaking cybercriminals. In February, we published a report on the Russian ransomware economy. It’s clear that the development of ransomware is underpinned by a flexible and user-friendly underground eco-system that allows criminals to launch attack campaigns with almost any level of computer skills and financial resources. Our researchers identified three levels of criminal involvement in the ransomware business.
The first is the creation and update of ransomware families. This requires advanced code-writing skills; and those involved are the most privileged members of the ransomware underground, since they are the key to the whole eco-system. The second is the development and support of affiliate programmes for distributing ransomware. This is done by criminal communities that deliver the ransomware using ancillary tools such as exploit kits and spam. The third is partner participation in such affiliate programmes. Those involved are on the lowest rung of the ladder and their role is to help the owners of affiliate programmes to spread the malware, in return for a cut of the proceeds: the only qualifications required are a willingness to carry out illegal activities and the money to join the affiliate scheme.
We were able to identify several large groups of Russian-speaking criminals specialising in crypto-ransomware development and distribution. These groups might bring together tens of different partners, each with their own affiliate programme. The list of their targets includes not only individual consumers, but small- and medium-sized businesses and even enterprises. While initially targeting organisations in the Russian Federation, these groups are now shifting their attention to companies in other parts of the world. The daily revenue of an affiliate programme might reach tens, or even hundreds, of thousands of dollars: of this, around 60 per cent stays in the pockets of the criminals as net profit.
In March we reported a new ransomware family used in targeted attacks against organizations, named PetrWrap. One they have gained a foothold in the target company, the attackers use the PsExec tool to install ransomware on all computers. One especially interesting aspect of this ransomware is that the attackers use the well-known Petya ransomware to encrypt data. Although Petya makes use of a ‘Ransomware-as-a-Service’ model, the attackers didn’t make use of this facility. Instead, they include a sample of the Petya ransomware inside the data section of the malware and use Petya to infect their victims’ computers. A special module patches the original Petya ransomware ‘on the fly’. This allows the attackers to hide the fact that they are using Petya.
Targeted ransomware attacks on organizations are becoming more common. The groups using ransomware in targeted attacks typically try to find vulnerable servers or servers with unprotected RDP access. After penetrating an organization’s network they use special frameworks such as Mimikatz to obtain the necessary credentials to install ransomware throughout the network. To protect against such attacks, organizations need to keep their server software up-to-date, use secure passwords for remote access systems, install security solutions on their servers and use security solutions with behavioral detection components on all their endpoints.
The Internet of broken Things
You might remember that in October 2016, cybercriminals used a botnet of Internet-connected home devices (such as IP-enabled cameras, DVRs, CCTV cameras and printers) to launch DDoS attack. To do this, the attackers infected vulnerable devices with the Mirai malware. This operation was significant not only because it misused Internet of Things (IoT) devices, but also because the DDoS traffic generated exceeded all previous volumes. The DDoS took down a portion of the Internet and was severe enough to initiate investigations by the FBI and the DHS. At the time, they had not ruled out activity by a nation state, because of the overall power of the Mirai botnets. But even the scale of these attacks didn’t require the work of a nation state. Time will tell if nation states choose to hide their destructive activity in plain sight in the IoT – the capabilities are clearly available. It’s possible that we might see a nation state tempted to take down wide swaths of the Internet using this juvenile toolset.
In February, we looked at reports of a cross-platform Win32-based Mirai spreader and botnet in the wild. Some of the public discussions around this suggested that an entirely new IoT bot is spreading to and from Windows devices. But this is not the case: rather, a previously active Windows botnet is now spreading a Mirai bot variant. We hadn’t seen this spreader variant pushing Mirai downloaders until January. But this Windows bot itself is not new. The Windows bot’s method for distributing Mirai is very limited as well – it only delivers the Mirai bots to a Linux host from a Windows host if it successfully brute-forces a remote telnet connection.
So we haven’t seen a sensational hop from Linux Mirai to Windows Mirai. But we do have a new threat and the use of Windows to spread Mirai to previously unavailable resources. In particular, vulnerable SQL servers running Windows can be a problem, because they can be Internet-facing, and have access to private network connected IP-based cameras, DVR, media center software and other internal devices.
It’s unfortunate to see any sort of Mirai crossover between the Linux and Windows platforms. Just as the release of source code for the Zeus banking Trojan brought years of problems for the online community, the release of Mirai IoT bot source code will also bring major problems to the Internet infrastructure for years to come. This is just the start.
In response to the huge problem this poses to the Internet infrastructure, over the past few months our team and CERT have participated in multiple successful C2 take-down efforts that otherwise have posed problems for partners simply providing notifications. While some security researchers may describe these take-downs as ‘whack a mole’, these efforts resulted in relief from Gbps DDoS storms for major networks. We’re happy to partner with more network operators to use our connections with CERTs, law enforcement agencies and other partners around the world, to build on this success.
You can read our report here.
This attack, like others that involve compromised IoT devices, exploited the fact that many people don’t change the manufacturer’s default credentials when they buy a smart device. This makes it easy for attackers to access the device – they simply have to try the known default password. In addition, there are no firmware updates for many devices. IoT devices are also an attractive target for cybercriminals because they often have 24/7 connectivity.
These days we’re surrounded by smart devices. This includes everyday household such as telephones, televisions, thermostats, refrigerators, baby monitors, fitness bracelets and children’s toys. But it also includes cars, medical devices CCTV cameras and parking meters. Some homes are even designed now with the ‘smartness’ built-in. Ubiquitous Wi-Fi brings all these devices online, as part of the Internet of things (IoT). These things are designed to make our lives easier. Since everyday objects are able to collect and transfer data automatically, without human interaction, they can operate more effectively and efficiently. However, a world of connected everyday objects means a bigger attack surface for cybercriminals. Unless IoT devices are secured, the personal data they exchange can be compromised, they can be subject to an attack, or they can be used in an attack.
One of the problems associated with IoT devices is that they are often everyday objects that have provided useful functions for much longer than the Internet has been around. So we don’t see the computer within the object. Nowhere is this truer than with children’s toys. In the last two years security and privacy concerns around children’s toys have been raised on a number of occasions (you can read more here, here and here).
In February, similar concerns were raised about the My Friend Cayla doll. The Federal Network Agency, the German telecommunications watchdog, suggested that parents that had bought the doll should destroy it because of these worries.
The best advice for anyone using connected/IoT devices at home, is to ensure the default passwords on all devices are changed (using unique, complex passwords) to prevent them being remotely accessed – this includes home routers, which are the gateway to your home network. The temptation may be for people to want to disconnect all devices in light of such news, but in today’s increasingly connected world, that’s not realistic; although it’s always good to review the functionality of a smart device and disable any functions that you don’t actually need. However, good password ‘housekeeping’ goes a long way to keeping cybercriminals away from your devices. This kind of large scale attack also highlights the need for manufacturers to consider security by design, rather as an afterthought.
Data breaches and data dumps
We’ve become accustomed to seeing a steady stream of security breaches month after month; and this quarter has been no exception, including attacks on Barts Health Trust, Sports Direct, Intercontinental Hotels Group and ABTA.
Some breaches result in the theft of sensitive data, highlighting the fact that many companies fail to take adequate steps to defend themselves. Any organisation that holds personal data has a duty of care to secure it effectively. This includes hashing and salting customer passwords and encrypting other sensitive data.
Consumers can limit the damage of a security breach at an online provider by ensuring that they choose passwords that are unique and complex: an ideal password is at least 15 characters long and consists of a mixture of letters, numbers and symbols from the entire keyboard. One alternative is to use a password manager application to handle all this automatically. It’s also a good idea to use two-factor authentication, where an online provider offers this feature – requiring customers to enter a code generated by a hardware token, or one sent to a mobile device, in order to access a site, or at least in order to make changes to account settings.
The public dumping of sensitive information has been gathering pace in recent years. This is a trend that we predicted in 2015. ‘Hacktivists’, criminals and state-sponsored attackers alike have embraced the strategic dumping of private pictures, information, customer lists and code to shame their targets. While some of these attacks are strategically targeted, some are also the product of opportunism, taking advantage of poor cyber-security.
In February, WikiLeaks released more than 8,000 documents, referred to as ‘Vault 7’, that describe tactics and tools used to break into computing devices from leading manufacturers, to circumvent installed security solutions and even lay a trail of false flags. The first batch of documents released (dated between 2013 and 2016) included documentation on how to compromise major browsers, smartphones and computers running Windows, Mac OS and Linux. Subsequent dumps of data focused on the development of malware to compromise firmware running on Mac OS and iOS, especially EFI and UEFI firmware; and on methods to evade detection. You can read more here and here.
We can only expect this practice to continue to grow in the future. Consumers and businesses alike should use encryption to secure sensitive data and should ensure that they apply updates as soon as they become available, to reduce the chances that their data will be stolen and dumped online.



















IT threat evolution Q1 2017