
- Blackmailer: the return
- In the tracks of Gpcode.ai
- The “universal” code
- Bad company
- ZeuS – Zbot
- The three Zs
- Conclusion
The third quarter of 2007 was less eventful than we expected. Of course, malicious programs didn’t cease to exist, and virus writers certainly didn’t reform overnight. Nevertheless, the events on the threat horizon were on a lesser scale than in previous months and years.
Anyone who remembers the global epidemics caused by Mydoom and Lovesan may find the unceasing stream of almost identical Trojans flooding the Internet rather boring. At first glance, malicious users appear to be lacking in ambition in terms of scale, and also in innovation. However, there’s a simple explanation: cybercrime has evolved into a professional business, and that’s why cyber criminals are now attempting to fly under the radar. Virus epidemics lead to investigation by law enforcement agencies. Those on the other side of the barricades now take discretion as their watchword, taking a softly softly approach, and behaving as quietly and unobtrusively as possible. In this climate significant technical innovations are rare. The criminal groupings now prefer to use tried and tested techniques and structures.
However, the desire to earn as much money as possible (or to put it more bluntly, straightforward greed) is exacerbated by the low-level technical skills of virus writers to create the weakest link in the chain. It’s when this happens that the ‘invisible war’ falls under the bright spotlight of the media and the general public hear of what is happening.
What will the third quarter of 2007 be remembered for? A multitude of incidents linked to the theft of user data. The latest ransomware Trojan. Mass hysteria about the Russian Business Network, so-called bullet-proof hosting that came to be seen as the ‘Resident Evil’ of the cyberworld by rank and file users, and as the ‘spawning ground for all hacker attacks’.
Against this background, information about the increasing size of botnets connected to the Zhelatin (Storm Worm) went almost unnoticed. Even information which clearly indicated that the ‘Storm’ botnet was made up of more than 2 million victim machines was effectively overlooked. The softly softly approach, remember?
The actual ‘front line’ was located on an entirely different level – and it wasn’t covered by the mass media.
As it happens, during the third quarter of 2007 we focussed a great deal of attention on certain events which were covered in the news. Researching one incident led us to other incidents which were just starting to unfold; to an outside observer, these events appeared to have no connection with each other.
This quarterly report is not a standard one. It’s based on data from a single major investigation and covers not only the significant events of the last three months but also demonstrates what virus analysts actually do.
Blackmailer: the return
For more than a year there had been no news of Trojan encryption programs. Last year our article ‘Blackmailer’ gave a detailed account of how antivirus companies combated Gpcode, a program which used an RSA algorithm to encrypt user data. The article stated that we expected to see an increased number of such programs in the future. However, there was a gap of almost a year before the encryption program staged a return, in mid July 2007.
Starting from around 13th July, some users started to discover that their documents, photos, archives and working files stopped opening, and simply contained ‘digital garbage’. Additionally, a file called ‘read_me.txt’ had appeared on their systems. Unfortunately the contents of this file were all too familiar:
(http://en.wikipedia.org/wiki/RSA).
You will need at least few years to decrypt these files without our
software. All your private information for last 3 months were
collected and sent to us.
To decrypt your files you need to buy our software. The price is $300.
To buy our software please contact us at: xxxxxxx@xxxxx.com and provide us
your personal code -XXXXXXXXX. After successful purchase we will send
your decrypting tool, and your private information will be deleted
from our system.
If you will not contact us until 07/15/2007 your private information
will be shared and you will lost all your data.
Glamorous team
Had the unknown scammer returned? The email address given was already known to Kaspersky Lab virus analysts – it had been used in some variants of Trojan LdPinch and Banker programs, Trojans which had clear Russian connections.
An analysis of the encrypted files conducted by our team showed that contrary to what was stated in the email, the virus writers had used a modification of the RC4 algorithm rather than RSA-4096. This made our task much easier. Within 24 hours following the initial discovery of the Trojan blackmailer we were able to break the encryption key and include decryption routines for user files in our antivirus databases.
An analysis of this new version of Gpcode showed that this malicious program was multiple functions. In addition to the encryption routine, Gpcode was potentially able to steal user data from the victim machine, send it to the remote malicious user’s server, and download certain files from the same server.
We were well aware that ransomware Trojans pose a serious threat, and decided to investigate this latest malicious program, named Gpcode.ai, more deeply. This turned out to be a very worthwhile decision.
In the tracks of Gpcode.ai
We decided to focus on three main areas:
- the server the Trojan sent data to and downloaded files from (http://martin-golf.net)
- the email address included in the message left on infected machines
- a text string contained in the body of the Trojan – “_SYSTEM_64AD0625_”
The server
We established that Gpcode.ai connected to the server using an s.php script placed there. In addition to this, it downloaded a file called cfg.bin from the server. This file was an encrypted set of instructions about what information should be harvested from the victim machine (account data for a range of banking and payment systems).
While we were analysing the malware, so were a number of other antivirus companies. The alarm was sounded by representatives of PrevX, who detected files from 494 victim machines on the malicious users’ server. The company then announced that a number of major companies were among the blackmailer’s victims. Mel Morris, PrevX’s CEO, even disclosed names: American Airlines, Booz Allen Hamilton and the U.S. State Department. None of the victims who were ‘outed’ chose to comment on Morris’ decision to reveal this information.
Other antivirus companies took a dim view of PrevX’s announcement. David Perry, from Trend Micro, said from an ethical point of view, the company was disturbed by PrevX’s desire to disclose details. Major antivirus companies were attempting to avoid giving any information (such as server or email addresses) about the malicious users, and were obfuscating these details in published descriptions of the virus (although this wasn’t always successful – see our blog (https://securelist.com/virus-descriptions-101/30352/) for further detail). PrevX, however, was telling the world not only where private data could be accessed, but who the data belonged to.
There was then an onslaught on martin-golf.net, with security experts, hackers, representatives of law enforcement agencies from many countries and the simply curious dropping by to take a look. Any research that could have been undertaken was disrupted – the malicious users knew that they were being observed, leaving the watchers watching the watchers, and not the criminals.
This meant that this line of investigation was going to be fruitless. We switched our focus to the email address.
We wanted to find out exactly what the correspondence between a cyber criminal and a user willing to pay money to have his/ her data restored looked like. So we sent an email to one of the addresses from the Trojan program, an email along the lines of ‘I’m John Brown, and my important data has been encrypted. I need this data urgently to compile a report and if I don’t get it done, my boss will kill me’. The very next day the unknown malicious user responded:
Please transfer $500 to e-gold account 4616329 and send us a e-mail to
address oxyglamour@gmail.com. You can buy e-gold with paypal with help of
exchange site listed on official e-gold site (http://www.e- gold.com/unsecure/links.htm#marketmaker).
After that, we will send your personal decoding program immediately
As this email shows, the authors of Gpcode.ai weren’t asking for the $300 dollars quoted in the message left by the Trojan but $500. The money was to be transferred using e-gold, the favourite payment system of cyber criminals. An account number was provided for the transfer.
And with this email this line of investigation came to a dead end.
The string “_SYSTEM_64AD0625_”
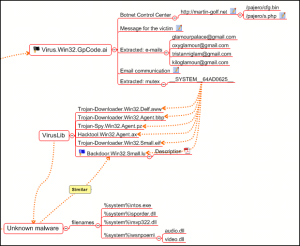
The only thing left to do was to attempt to establish which other malicious programs could have been created by the group calling themselves the “Glamourous team”. So we started searching our virus collection for the following string: “_SYSTEM_64AD0625_”
The results were entirely unexpected. This mutex was found in the widest possible variety of Trojans – in Trojan downloader programs, Trojan spy programs, and in backdoors as well.
The common feature in all these samples was the name of the file which the malicious programs installed to the victim machine: ntos.exe, exactly the same file name used by Gpcode.ai. In addition to this, the malicious programs found in the collection contained files called sporder.dll and rsvp322.dll, and created a sub catalogue called wsnpoem containing files called audio.dll and video.dll in the Windows system directory.
A detailed analysis of selected files showed that they didn’t just contain the same mutex, but over 80% of the code was identical!
The “universal” code
We seemed to have stumbled across some universal code. The code was designed both to steal data and to install new Trojans on the victim machine, as well as acting as a bot and connecting a victim machine to a zombie network.
Malicious programs which use this ‘universal’ code have a single component and a small (when compared to the overall size of the file) unique function which differs from variant to variant. Interestingly, we detected some of these programs back at the end of 2006. The ‘universal’ code was also used to create Gpcode.ai.
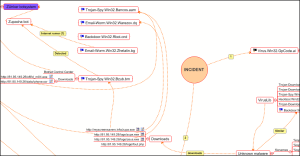
New records and relations extended the charts we used in tracking our research.
Bad company
The next stage in our research was to analyse the links in the samples which contained the ‘universal’ code. We took the most recently detected file and extracted four links from it – links used by the malicious program in delivering its payload:
http://81.95.149.28/logo/zupa.exe
http://myscreensavers.info/zupa.exe
http:/81.95.149.28/logo/fout.php
What does this Trojan do? Above all, it installs itself as ntos.exe to the victim machine, then downloads files called zeus.exe (http://81.95.149.28/logo/zeus.exe) and zupa.exe (http://81.95.149.28/logo/zupa.exe), connecting via a script called fout.pho (http:/81.95.149.28/logo/fout.php) in order to identify itself within the botnet. The Trojan downloads cfg.bin, an encrypted configuration file. This file contains a text message and links to other sites. The malicious program then starts to track user activity and when the user visits any message boards, guest books or blogs, the Trojan appends its own text (extracted from cfg.bin and containing links to a malicious file (http://myscreensavers.info/zupa.exe)) to the user’s message:
We used Google to find similar examples…and found a lot of them without any difficulty:
Constructing an attack in this way makes it possible for the Trojan authors to use previously infected machines in order to spread new variants of the malicious program and/ or to increase the number of infected computers. This case is a clear demonstration of how malicious users are moving away from traditional infection vectors (e.g. sending malicious programs via email) and are instead harnessing the power of the Internet to spread their creations.
But which malicious programs did the Trojan that we were analyzing spread? The data below gives an interesting picture:
These families are all distinct from each other; at first glance they don’t seem to have anything in common and it was previously believed that they were written by different virus writing groups. However, they were spread from one and the same site by one and the same Trojan downloader program. What’s more, they’re all connected in some way with Gpcode.ai!
It wasn’t entirely clear what was going on. We started to think that there might be an international syndicate involved in the creation and spreading of the vast majority of today’s malicious programs.
Our worst fears were confirmed when we analysed the botnet which was created using Bzub. It became clear that a Trojan, named Zupacha by its author, was a direct relative of Bzub. Bzub and Zupacha are almost identical programs, but Bzub has a Trojan spy function whereas Zupacha does not.
Bzub/ Zupacha are bot clients managed by the botnet system Zunker.
And there’s yet another malicious program related to the Zunker botnet: Email-Worm.Win32.Zhelatin.bg. This is one of the notorious Storm worms which since the start of 2007 have been flooding mail traffic. These worms use sophisticated social engineering approaches in order to spread.
To summarize: Zhelatin, Warezov, Bancos.aam, Bzub and now Gpcode.ai all turned out to be connected to each other. These programs all come from different families but these malware families are among some of the most active and dangerous malicious programs at the current moment. Files with names such as ntos.exe, video.dll, audio.dll, sporder.dll, lcewza.exe, filech.exe, filede.exe, iphone.scr, ldr.exe, ldr2.exe, loader.exe, pajero.exe, update92520748.exe, zeus.exe, zs1.exe are well known to virus analysts throughout the world.
Having teased out one thread, we started unravelling the following tangle:
While we were conducting our investigations, the unknown malicious users made themselves clearly known. To be more precise, they weren’t attempting to attract attention, but the events that unfolded turned out to be very significant.
Broker
During 25th July 2007 (only ten days after Gpcode.ai appeared) Kaspersky Lab analysts detected a new malicious program which was spreading actively. The victims were users of some of the most popular Russian news sites – utro.ru, gzt.ru, rbc.ru.
It became clear that a link (http://www.txt.utro.ru/cgi- bin/banner/rian?86028&options=FN) within the Utro.ru banner system was being opened, which contained a link to a malicious site (http://81.95.145.210/333/m00333/index.php). This site was hosted by the notorious ‘bullet-proof’ hosting company RBN (Russian Business Network).
When this page was opened, the user’s browser would be attacked using a collection of exploits (in this case, the commonly used Mpack bundle). If the attack was successful, a Trojan downloader would be downloaded to the victim machine. This program would, in its turn, install another malicious program – Trojan-Spy.Win32.Bancos.aam.
Once installed on the system, the Trojan would start to run the following commands:
GET /e1/file.php HTTP/1.1
GET /ldr1.exe HTTP/1.1
GET /cfg.bin HTTP/1.0
POST /s.php?1=april_002fdf3f&i= HTTP/1.0
As a result a file called ntos.exe (a name already well known to virus analysts) would appear on the victim machine. This was the file used to install Gpcode.ai to the system. Expecting the worst in the form of a new encryption program, we started to conduct a detailed analysis of this file.
However, the program turned out not to be a Gpcode variant. This new version of Bancos.aam turned out to be the first Trojan spy program designed to steal data from users of the Russian QUIK system.
QUIK is an application package which provides online access to stock market systems. Securities deals conducted via the Internet are known as Internet trades. QUIK is made up of a server side application and the client side workplace (terminal) which communicate with each other via the Internet.
We had never seen virus writers attempting to get access to online trading systems before. There are multiple examples of cyber criminals gaining access to bank accounts and this has been happening for a long time. But stealing trading account data was something new.
The Trojan scanned the victim machine for files called secring.txk, pubring.txk, and qcrypto.cfg, which contained saved access parameters to QUIK. The data in these files was then sent back to the server.
Given that we knew exactly which files the spy program was searching for, we once again searched our virus collection. And we found another five variants of the Trojan, the first of which dated back to the beginning of July. As a result, all these programs were reclassified into a new family and renamed as Trojan-PSW.Win32.Broker.
It should be noted that these Trojans exhibited a remarkable resemblance to Gpcode.ai in terms of their code. The differences were simple: one steals data, while the other encrypts data. Once again we had stumbled across the ‘universal’ code.
Interim results
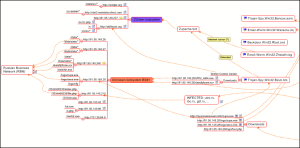
The facts which we had by the first of August were as follows:
- Gpcode.ai used the ‘universal’ code and contacted the martin-golf.net site
- Bancos.aam used the ‘universal’ code and downloaded files hosted by the ‘bullet-proof’ Russian Business Network (RBN)
- Some of the Zunker botnets which we had already detected were hosted on RBN resources
- Zunker botnets act as command and control centres for downloaders which download programs similar to Bancos.aam/Gpcode.ai
- Among the malicious programs which can be managed using Zunker are the Zupacha downloader program, the Bzub spy program and probably the Zhelatin (Storm) worm
- One such botnet was used to spread the Warezov worm
However, we were lacking one piece of the jigsaw –who was the author of this ‘universal’ code that was so widely used in such a range of malicious programs? And could all these incidents result from the activity of one and the same group of virus writers?
We had to spend a considerable amount of time reading a range of hacker sites and message boards, most of them Russian language ones. The situation gradually started to become clearer.
In search of the ‘universal’ code
Zunker and Zupacha
So what had we been dealing with all this time? Hacker sites were actively selling a Zunker+Zupacha package – a botnet command and control centre and a bot client. We already knew this. The interesting discovery was how much the unknown authors of the bot system wanted for their bundle: up to $3000. There were occasional ‘two-for-one’ offers at around $200, a far lower price. Such offers were probably made by other owners of the source code of the Trojan bundle.
However, we didn’t have any trouble getting our hands on all the Zunker and Zupacha files for free, simply by using Google and knowing the addresses of some currently active botnets.
Zupacha’s functions turned out to be formidable. In addition to downloading files to the victim machine, the program’s main task is to continue to spread. We’ve already described one of the ways in which it spreads (by inserting its texts into messages on forums) above. Overall, Zupacha is able to spam its links in the following ways:
- ICQ/Jabber spam: Texts with links to malicious sites are added to all messages which the victim exchanges with his/ her contacts via these IM clients
- Web spam: Texts are added to any web form filled out by the user. As a rule, these are forms contained on message boards and the web interfaces of email systems.
- Email spam: Texts are added to the victim’s emails.
It should be noted that in the cases shown above, Zupacha doesn’t initiate the mass mailing of messages. It simply monitors user activity and adds its texts to any outgoing message – in such a way that the user doesn’t see them! This is a feature expressly designed to hinder the detection of infection.
However, Zupacha does not steal any data – it’s simply a self-propagating Trojan downloader. Consequently, it can’t serve as the notorious ‘universal’ code.
The answer to our question came after further analysis of hackers’ offers of malicious programs: the ‘universal’ code which was used in hundreds of variants of Bancos.aam, Gpcode.ai and Broker turned out to be the ZeuS bot (this is the name used by the author).
ZeuS – Zbot
The data collected by us from the variants of ZeuS which we already had, plus our own investigations on the Internet, made it possible for us to get an almost complete picture of what this program actually is.
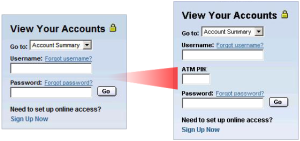
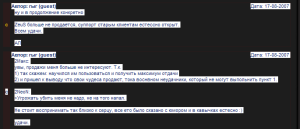
Let’s start with the fact that the bot was originally designed to be sold to anyone who wanted it, and to be configured in accordance with the buyer’s wishes. The author of the program did not offer ‘technical support’ to those who bought the program, outsourcing this function to others. After the publicity created by Gpcode.ai and Broker it seems the author decided that his/ her creation had attracted far too much attention and that law enforcement agencies were exhibiting an unhealthy degree of interest. S/he subsequently announced that sales of the program would cease.
The screenshot above showed a conversation in which the author of the program explains that the program is no longer for sale, but that ‘old clients’ will continue to receive support.
This story is extremely similar to the events which took place at the end of last year, when incidents connected with the theft of data from Nordea bank customers caused Nuclear Grabber, a Trojan with very similar functionality, to come to light. At one stage this Trojan was being sold for $3,000, and its author, Corpse, even gave an interview to a journalist. Corpse then announced on his site that he was ‘going out of business’, that ‘all source code had been destroyed together with the hard disk’ and that he wouldn’t be creating or supporting malicious programs any longer.
In the case of ZeuS the scenario was very similar. Despite the fact that the author had shut up shop at the end of July, a constructor was circulating among hackers. This constructor made it possible to create new variants of the bot with specific functions. Several competing groups started selling and spreading these new variants.
Initially ZeuS had a relatively limited bot function – it simply downloaded other files to the system. However, over time this was extended. We don’t know whether this was done by the author, or if the new developments were implemented by the new ‘owners’ of the source code. The most significant innovation was the appearance of a universal ‘interface’ in ZeuS, which made it possible for the program to connect to the Zunker botnet (just as Zupacha did), get instructions via the cfg.bin file and run them on the fly.
We created a program to decrypt some of the cfg.bin files. It turned out that they contained the online addresses of a multitude of banks and payment systems. The owners of the botnet were able to quickly add the addresses of new targets in order to track user activity and intercept data.
In addition to standard routines (such as installing itself to the victim machine, injecting its code into launched processes, counteracting some antivirus solutions and the presence of socks and http proxy servers) the bot also had extensive data theft functions:
- The Trojan harvests the contents of Protected Storage which includes saved user passwords
- Form grabber. The Trojan intercepts all data entered in a form transmitted via the browser. The list of monitored addresses (to which data relating to will be stolen) is made up, as a rule, of banks and payment systems. This is how payment accounts are stolen.
- Circumventing virtual keyboards. The Trojan hooks mouse presses and makes screenshots as the data is intercepted.
- Falsifying sites and pages. This is a very interesting method previously used in Nuclear Grabber. When the user attempts to contact one of the sites which are monitored by the Trojan in order to harvest data, the request is either redirected to a phishing site, or a new data entry field will be added to the original page. The contents of the page are modified on the user’s computer prior to the page being displayed by the browser.
- Stealing certificates
The distinguishing feature which enabled us to find ZeuS variants very quickly within our collection is the mutex which it creates in order to flag its presence in memory: _SYSTEM_
For example:
__SYSTEM__64AD0625__
__SYSTEM__23D80F10__
__SYSTEM__7F4523E5__
__SYSTEM__45A2F601__
Thanks to this we were able to group all ZeuS variants into a separate family under the generic name of Zbot.
And this is the ‘universal’ code; it uses a large number of original methods to steal any type of data. The most dangerous thing is that every new variant can be supplemented by a wide range of other functions, as was the case with Gpcode.ai.
The three Zs
Now everything was clear. In effect, there’s a standard package being used by the Russian cyber criminal community: the Zupacha+ZeuS bundle, and the Zunker botnet managed by this bundle.
The sheer size of the zombie networks created using these programs is impressive. One of the largest networks, created using Zunker, united 106000 victim machines at the time of its detection, with 1,500 new computers being added every 24 hours. Zupacha was able to spread very effectively as the botnet command and control centre is easy to configure and use.
Any malicious user, even a real script kiddie, would have been able to buy these two Trojans (ZeuS and Zupacha) specially configured for a specific client. S/he then needed to rent a server somewhere and install Zunker (the botnet control panel). Of course, in a great many cases the hosting company of choice was the Russian Business Network, which has figured in the media over the last six months and which has gained a reputation in the West similar to that of the Umbrella Corporation in Resident Evil.

We weren’t so much interested in RBN as in its clients and the botnets which these clients were using. As we knew where to look and what to look for, we were able to easily identify several such systems (see diagram above).
We can state with certainty that some of the Zunker botnets were used to spread dangerous malicious programs such as Zhelatin (the Storm worm) and Warezov. It could be that the authors of these programs deliberately used Zunker+Zupacha to create these botnets, or it could be that they simply leased the power of already existing botnets, paying the owners for spreading their malware.
It’s worth noting that when Zupacha fell into the hands of hackers in the West they were impressed by the concept, analysed the code and discussed it on forums. (http://www.1918.com). They learnt how to modify the address of the control centre in the Trojan’s binary file in order to use it for their own ends, even though they didn’t have the source code. They even attempted to construct a control centre themselves which included a database to which the Trojan’s configuration was saved. Later, one of these hackers found the control centre code, and the database structure, and everything started moving more quickly. Everyone involved in this (analysing the Russian Trojan and using the ‘weapons of the Russian mafia’) participated in developing, spreading, and popularizing Zupacha.
Conclusion
All the information above illustrates how cyber criminals (particularly Russian ones) act as a team. Individual virus writers and groups create Trojan programs for sale; those who buy them configure the programs to meet their needs, sometimes to such an extent that the original program is barely recognizable. Infected machines are united into botnets which may be made up of hundreds of thousands of machines. The machines are managed via a command and control centre – code written by other malicious users which is also freely on sale. These botnets can be used to spread a wide variety of malicious programs, which frequently are in direct competition with each other. In order for this entire structure to have as long a life cycle as possible, in spite of all the efforts of antivirus companies and law enforcement bodies, there are dedicated ‘bullet-proof’ hosting companies which offer their services at prices ranging from tens to thousands of dollars a month.
This industry naturally makes a certain profit as there’s not only demand for the creation and spreading of Trojans, but there’s also supply. Our research focussed on one particular part of the iceberg: the one made up of Russian language hacker groups. Of course, there are other groups in existence – South American, Chinese, Turkish and so on and so on. Each of these groupings has its own way of working and its own characteristics but overall they are relatively similar. There are no frontiers on the Internet.
One final example of the information given above is an article which appeared on 17th August in InformationWeek. In the article, Don Jackson, a security researcher with SecureWorks, told the publication that he had identified 12 data caches most of which contained between four and six thousand stolen records. Overall, data from approximately 100,000 individuals had been stolen – four times as large as what Jackson had seen previously. The data had been stolen by Trojans running on fraudulent ads on two major recruitment sites, one of which was Monster.com.
You’ve probably managed not only to guess which Trojan Jackson was referring to and where it sent the harvested data. Yes, you’re right! It was ZeuS, the ‘universal’ code, which sent the data to the Russian Business Network.



















Malicious code evolution: July – September 2007