
Introduction
This article examines the evolution of the IM worm since the beginning of 2005. It is written from a European standpoint: this means that it does not include information about certain IM-Worms which did not spread widely in Europe. It also does not cover the topic of malware for certain IM clients such as icq, which are less commonly used in Europe.
Although the first IM-Worm appeared in 2001, this type of malware didn’t become really common until the beginning of 2005. If we take a look at this period, it becomes clear that it’s very important to differentiate between IM Worms which were written with a range of aims.
Worms like Sumom caused quite an outbreak and therefore caught the attention of the media.
Worms like this were written by cyber vandals, who were interested in causing arbitrary damage and attracting attention. This type of IM-Worm gave the overall impression that IM-Worms were the domain of cyber vandals wishing to assert themselves. However, this was incorrect: two of the most notorious families, Bropia and Kelvir, were created specifically for financial gain.
The appearance of Bropia, Kelvir and Prex
Bropia, Kelvir and Prex all spread via MSN Messenger as links to files located on a (http) server.
The next step in the evolution of IM-Worms came with the appearance of the Bropia family in February 2005. Although from a programming point of view, Bropia was nothing special, the author showed he was serious by choosing a then unknown packer. An early Bropia variant was packed with PEspin 1.1; at that point in time no major virus scanner offered support for this packer. When we noticed that the author of Bropia was continuing to use PEspin 1.1 unpacking support was quickly added to the antivirus databases.
In response to Kaspersky Lab proactive detection rates increasing for this family, the author(s) started using another, at the time, unknown packer – UPack. At the time of writing, UPack was one of the packers most commonly used by malware authors
Two weeks after the first Bropia appeared, Kelvir was first detected. These two families are very similar to one another, with one significant difference.
Bropia and Kelvir both contain an IRCBot. The main purpose of these worms is to install this IRCBot.
While Bropia arrives as just one file, which contains the IM-Worm with the IRCBot embedded, Kelvir typically arrives as a self extracting (RAR) archive which contains two separate files: the IM-Worm and the IRCBot.
Early variants of Bropia and Kelvir were regularly placed on Dutch servers. This, combined with the facts that the Netherlands has one of the highest percentage of MSN users in the world, and that awareness of the security risk posed by IM worms was non-existent, resulted in a significant number of local outbreaks.
With the IRCBots being used for massive AdWare installations it’s likely that the authors were making quite a profit, as they would have been receiving payment for every piece of adware installed to a victim machine.
The third family discussed here, Prex, is based on code from Bropia/Kelvir. It was initially classified as a Trojan-IM instead of an IM-Worm.
This was because Prex spreads a link to an IRCBot and not to itself. According to the Kaspersky Lab virus classification, such programs are Trojans, not worms. However, in view of the fact that files on web servers can always be changed, it was decided that this piece of malware should be reclassified as an IM-Worm. Overall, there is still some debate as to whether such malware, which spreads via IM, really is: a worm or a Trojan.
Bropia, Kelvir and Prex are very much alike and for this reason dozens of variants of all these families have been detected with our IM-Worm.Win32.Prex.d signature.
Social revolution
Initial IM-Worm variants used primitive, tried and tested social engineering methods to encourage users to click on the link sent by the worm. File names (with a .scr or .pif extension) The file or link would often suggest content of a humorous or sexual nature, with Paris Hilton being a popular choice among these virus writers.
Our data shows clearly that worms which used .a pif extension caused a much bigger outbreak than those with a .scr extension. This is almost certainly due to the fact that people misread it as gif (or .tiff), indicating a graphics file.
This meant that virus writers opted to use a .pif extension as it seemed to be more effective, and, there was a clear increase in the number of worms using a .pif extension. Nevertheless, worms using .scr extensions didn’t completely disappear.
Major outbreaks resulted in IM-Worms becoming less effective; users were becoming more aware of the risks, and were less likely to infect themselves. This meant that attackers needed to think of new social engineering tricks.
The virus writers started adding a message next to the link in an attempt to make it seem more legitimate. This proved to be quite effective, as an increased number of reports from infected users showed. However, the virus writers’ next move had even more impact. In April 2005 we started spotting Kelvir variants which spread as a link to a server supporting php.
How is PHP used in this case? PHP is used mainly for producing dynamic web content and server-side applications. A client, in this case the user, can submit data for the server to process.
Example:
Pictures.php is the PHP script running on the server. Everything after “?” is the data submitted to be processed by the PHP script.
What then happens depends on how the PHP script is written.
The most usual scenario in the case of IM-Worms is that the email address will be stored in a database for spamming purposes. Then an executable will be presented to the user for download – the IM-Worm.
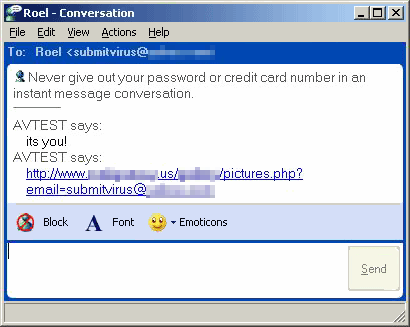
Kelvir.k spreads as a link to [server]/pictures.php?email=[recipient’s email address]. This was an extremely sophisticated piece of social engineering.
Firstly, this link doesn’t seem like an executable. The recipient is therefore more likely to click the link. Clicking the link makes it possible for the recipient’s email address to be harvested even if the user doesn’t execute the program offered for download.
Secondly, the inclusion of an email address personalizes the message. Such personalization is key in successful social engineering.
Thirdly, the link appears to lead to a picture gallery hosted on the server.
Following this, a Kelvir variant with ‘chatbot’ functionality was detected. This worm used set phrases to make small talk with the potential victim before sending the link.
However the approach of sending a ‘.php link’ remained (and remains) a favourite with the authors of IM worms, presumably because it is seen as being the most effective. As there are quite a lot of variables in such ‘.php links’ which can be changed, it’s easy for virus writers to exploit this from a social engineering point of view.
This is as far as IM-Worm evolution has advanced in social engineering terms as far as MSN is concerned.
AOL Instant Messenger
In the first half of 2005 it became clear that virus writers were mainly targeting MSN as this would be the way to infect the maximum number of users. Because of this focus, malware for other IM-clients did not go through such a clear process of evolution in terms of social engineering and more or less skipped the initial steps which might have been expected.
There’s one significant factor which influenced the evolution of malware for different IM clients: HTML parsing. Clients such as AIM support (basic) HTML parsing, which gives virus writers using social engineering a lot of options. It’s very easy to exploit HTML parsing by making ‘fake’ links/URLs which will tempt the recipient to click on them.
It seems likely that the fact that MSN does not support HTML parsing is one of three major reasons why there has been a clear shift from virus writers targeting MSN to targeting AIM.
The second reason is that not a lot of people use both MSN and AIM. This means that by targeting AIM, virus writers had a whole new ocean to fish in – and given the number of AIM users, particularly in the USA, the potential catch is very large.
The third and final reason, as I see it, is that while it’s easier for virus writers to trick AIM users, it has also become much harder to fool MSN users. This is not because the MSN user community overall is now aware of potential threats, but partly because MSN itself took some drastic measures.
For instance, MSN blocked all messages containing “.pif” at the network level. Messages containing “gallery.php” and “download.php” messages were also blocked. In addition to these security measures, later versions of MSN Messenger will not accept files with extensions which indicate a potential threat, such as .pif, .scr and so on.
Although there are a number of IM-Worm families which target the AIM network, they currently appear to be of limited significance. One example is IM-Worm.Win32.Opanki: although this worm became quite prevalent, it has limited IRCBot functionality, and is only capable of downloading files.
Invisible IM-Worms
Although we did start seeing IM-Worms which used rootkit technology to mask their activity back in May 2005, this section examines a slightly different issue.
One of the interesting differences between malware that spreads via MSN and malware which spreads via AIM is that usually the MSN-Worm is a separate component/file. In the case of malware which spreads via AIM, this functionality is usually incorporated into the body of the malicious program; the propagation routine is often secondary to the main payload.
There is some malware which spreads via MSN which behaves in a similar way: for instance, some Mytob variants also contain a component which spreads via IM. This component will be detected as Mytob. However, there’s a greater number of malicious programs which spread via AIM: one of the most notable families is Backdoor.Win32.Aimbot, a typical IRCBot with the ability to spread via AIM.
There are also a lot of SdBot and Rbots whose ability to spread via AIM is just one small subset of their features. Some Trojan-Downloaders, such as the Banload family, have similar functionality.
All of this makes it hard to get a clear picture of the number of malicious programs with the ability to spread via AIM. One thing is clear: there is far more malware out there which is capable of spreading via AIM than it would seem at first glance.
What’s at the bottom of this quantitative difference between MSN and AIM spreading malware? Pretty much all MSN-Worm code is still in Visual Basic, while most malware which spreads via AIM is written in C. Code in C can effectively be cut and pasted by inexperienced virus writers into the source code for an IRCBot and it will still work, because all popular open source IRCBots are written in this language. This is not the case with VB code. This pool of ready made code results in the increased number of malicious programs which spread via AIM.
Technical evolution
The earlier parts of this article cover some points relating to the technical evolution of IM-Worms. However, there are some additional points of interest.
In May 2005 we noticed that some functionality was being added to the IM-Worm package. Bropia.ad included the ability to spread via P2P, while the IM-IM-Worm.Win32.Kelvir.bm package also contained a rootkit.
IM-Worm/Backdoor packages like Kelvir and Bropia are not that common anymore. It seems that malware authors have chosen to split the two for a number of reasons.
For instance, the following scenario is quite common nowadays:
An user receives a link via IM. S/he clicks on it and is either taken to a website which contains an exploit, and malware will then automatically be installed to the victim machine, or s/he is asked to download and/ or run an executable file i.e. the IRCBot.
When the Backdoor is executed it will either download the IM-Worm automatically or receive a command via the IRC channel to download this file..
These worms are still very similar to Kelvir, but there is one major difference: they spread only on command.
The worm will only start spreading when the IRC operator (the Bot master) gives a specific command in the channel, or to one specific victim machine. It should be noted that in such cases, the worm spreads as a link to the Backdoor, not to itself.
There are several advantages to this approach:
- If a download command is issued via an IRC channel, it’s just a matter of time before the files reach security researchers. Researchers frquently contact the hosting providers of the website hosting malicious files, and ask them to take the site offline. As soon as the bot master realizes his website has been taken down, he can upload the malicious file to a different server and modify the download link which is fed to the IRCBots. This way the botnet can continue to grow
<li class=largeIt can be harder for antivirus companies to obtain a sample of the IM-Worm. As a result, it may take longer to create and release detection.
The most important reason is that this way the size of the botnet can be controlled. Earlier Kelvir variants would simply continue to spread in an uncontrolled fashion. However, if only one or two IRCBots are instructed to start spreading, there will be no large scale epidemic which would attract the attention of antivirus companies, law enforcement bodies and the media.
There are some Kelvir and Opanki variants which are able to send dynamic messages and/or download links. This means that the botmaster has full control over the content the IM-Worm sends out. This a now fairly standard for Backdoors which are able to spread via AIM.
Finally, in January 2006 we came across IRCBot.lo.
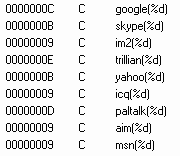
Not only is this piece of malware able to spread links to a large number of IM networks, but both the message and download link are variable. This may well be the ultimate in IM-Worm functionality.
Conclusion
This article doesn’t examine other malware such as Trojan-PSW.Win32.PdPinch which spreads via ICQ, and which is a big issue for Russia and certain other non-European countries. Nevertheless, we have aimed to provide an overview of the IM malware landscape.
Since IM-Worms first appeared, there have been significant changes, in distribution methods, in the sophistication of the code used and in the IM networks targeted. Additionally, dynamic messages help increase the lifecycle of malware and of botnets, and the use of controlled spreading helps malware authors evade unwanted attention.
In most cases, an IM-Worm should not be viewed as a standalone piece of malware, but rather as a slave which is used to help the IRCBot spread.
The appearance of IRCBot.lo demonstrates that IM is an infection vector which has not yet been exhausted. Additionally, this code could be easily copied, potentially resulting in a significant increase in IRCBots which can spread links across all major IM networks. It therefore seems likely that we may start to see reports of other IM networks being increasingly targeted in the future.
The ability to spread via IM is functionality which malware authors will undoubtedly continue to use as part of a multi-featured IRCBot. However, it is likely that in the long run, dedicated malware which only exists to spread via IM (i.e. early variants of IM-Worms) will continue to die out.





















Death of the IM-Worm?