
Spam in the spotlight
January saw spammers switch their attention from Christmas and New Year to St. Valentine’s Day. English- and Russian-language mass mailings offering video surveillance systems were yet another popular trend in January.
So-called Nigerian fraudsters continued to exploit the deaths of Nelson Mandela and Ariel Sharon to trick users into giving away their money.
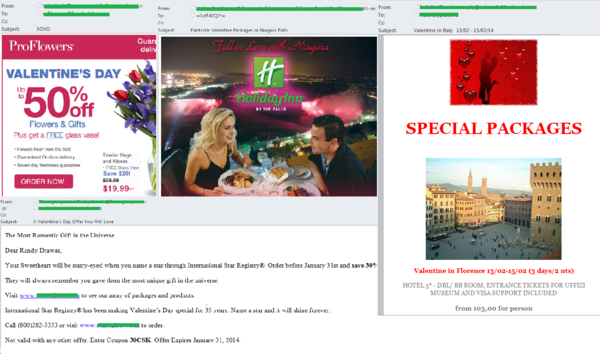
Holiday spam
With the main winter holidays over the spammers switched their attention to upcoming events, and in particular, to Valentine’s Day. As well as the traditional ‘flower’ mailings and suggestions for a romantic meal or trip, English-language spam contained adverts offering some rather unusual gifts, including a real star in the sky.
In February, we expect to see growth not only in holiday-themed spam but also in mass mailings on other themes. In addition, we forecast an increase in the number of mailings exploiting the theme of St. Patrick’s Day.
The ‘Nigerian’ wives of Nelson Mandela
The tragic events of recent months are actively exploited by ‘Nigerian’ scammers in their fraudulent emails. In early January, the former Israeli Prime Minister Ariel Sharon died and a week later we registered a mass mailing exploiting the news. However, the death of Nelson Mandela was exploited to a far greater extent. The first mailings mentioning the death of the former South African presidentappeared in December.
In January, as expected, new emails emerged. It is a well-known fact that Nelson Mandela was married three times and this was something the spammers picked up on. This time they actively used the names of his wives to convince the recipients that their stories were true.
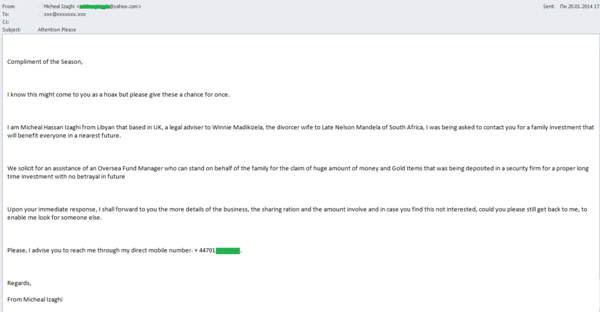
One ‘Nigerian’ letter supposedly written by the lawyer of the late president’s second wife Winnie Madikizela did not contain any details of cooperation. It merely stated that Winnie and her lawyer needed help in obtaining a huge amount of money and gold bars and then investing it. They claimed they were searching for a respectable person who had to be a foreign citizen. For feedback and more details the email specified a mobile phone number. Remarkably, the scammers asked the recipient to contact them even if the offer was not of interest to him, saying that in that case they would seek help from someone else. The scammers obviously banked on the recipient’s greed being greater than their common sense.
Yet another mass mailing was supposedly from Mandela’s third wife Graca Marshal. This time the scammers tried to win the recipient’s sympathy with a sad tale about the struggle within Nelson Mandela’s family for his millions and about other greedy relatives capable of anything. To confirm the story the emails contained a link to a news article in a renowned newspaper. The fraudsters asked for help in transferring the money of the “unfortunate president’s wife” and keeping it safe in the recipient’s account.
Video surveillance systems
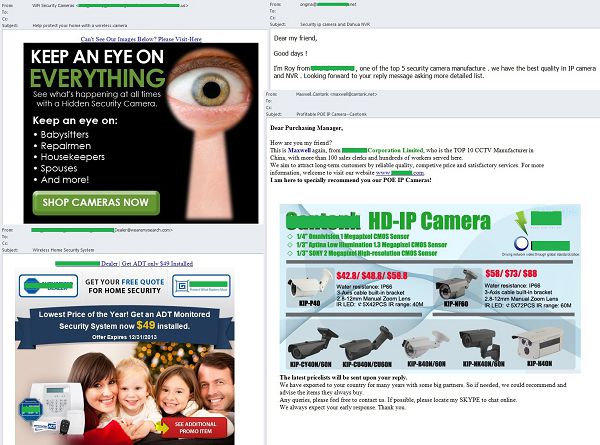
January saw an increase in the amount of mass mailings with offers to buy and install video surveillance systems on private and commercial premises. Such offers are fairly typical. Basically, they are unsolicited emails written on behalf of various companies specializing in video surveillance systems. As a rule, these emails do not specify the company name in the sender address. Instead, the address contains the name or the surname of the sender which is not always the same name of the manager in the message.
The English-language spam on this theme focused on personal safety and the possibility of keeping an eye on husbands and wives, as well as health visitors and workmen in private homes. The messages often included a link to the contractor’s site or an online store selling surveillance cameras instead of a contact phone number.
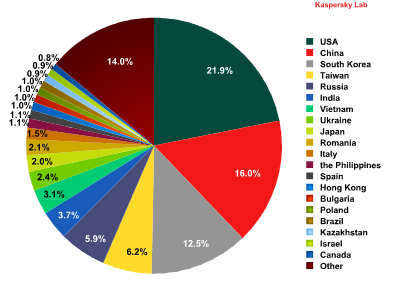
Geographical distribution of spam sources
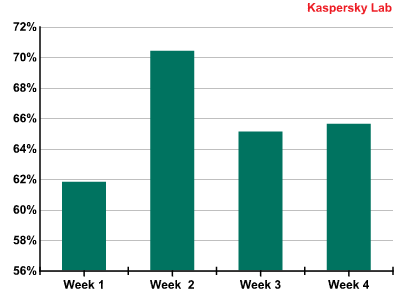
Proportion of spam in email traffic
The first week of 2014 saw a slight decline in the share of spam caused by a drop in spammer activity during the holiday season. However, the second week of January made up for this: the number of spam mailings increased significantly. In the second half of the month the situation normalized and the January average accounted for 65.7% of all email traffic.
Spam sources
In January, the list of sources distributing spam worldwide underwent several changes.
The USA moved up from second to first place in the rating after distributing 21.9% of all spam, an increase of 3 percentage points. By contrast, China’s contribution (16%) decreased by 7 percentage points, which resulted in the country dropping to second place. South Korea came third again (12.5%) though its share also fell by 1.5 percentage points.
As in December, fourth place was taken by Taiwan (6.2%), followed by Russia with 6%. The Top 10 was rounded off by Romania, which accounted for 2% of all spam sent worldwide.
A slight increase in spammer activity was recorded in Italy, where the proportion of unsolicited mail was 1.5%, as well as in Spain (1%), Hong Kong (1%) and the Philippines (1.1%). The figures for the other countries remained the same with no change in their ranking.
In January, South Korea remained the leading source of spam sent to European users (47.2%) even though its share dropped by 5.9 percentage points from the previous month. Next came Taiwan (5.8%), which was third in December, followed by the USA (-2.1 percentage points) averaging 5.3%.
Hong Kong ended the month in fourth place with 3% of spam in Europe originating from there. Russia (3%) remained fifth, gaining 0.3 percentage points. It is followed by Spain (2.4%) and Italy (2%): both countries also showed a slight increase in the proportion of spam sent to European users. Romania (1.7%) completed the Top 10.
China (1.4%) fell seven places and out of January’s Top 10 as its share dropped by almost 2 percentage points.
Of note is the slight growth in spammer activity in the UK (1.4%), Germany (1.3%) and France (0.9%).
Asia (49%) remained the leading regional spam source in January despite a considerable drop (-7.6 percentage points) in spammer activity. North America came second having distributed 15% of global spam, an increase of 2.8 percentage points. Meanwhile, Eastern Europe’s share went up 1.3 percentage points, averaging 18%, putting the region in third place in the rating. Western Europe (5.8%) and Latin America (4%) came fourth and fifth respectively.
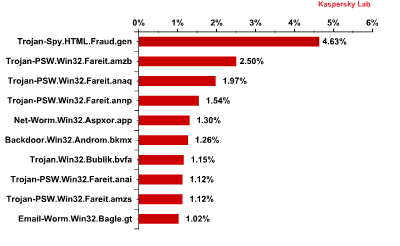
Malicious attachments in email traffic
In January, the Top 10 malicious programs that spread via email was as follows:
Trojan-Spy.html.Fraud.gen remained the most widespread malicious program. Fraud.gen belongs to a family of Trojan programs that use spoofing technology: these Trojans imitate HTML pages and are distributed via email, appearing in the form of notifications from major commercial banks, e-stores, software developers, etc.
Trojan-PSW.Win32.Fareit.amzb, Trojan-PSW.Win32.Fareit.anaq, Trojan-PSW.Win32.Fareit.annp, Trojan-PSW.Win32.Fareit.anai and Trojan-PSW.Win32.Fareit.amzs came second, third, fourth, eighth and ninth respectively. These programs belong to a family of malware that steals user logins and passwords and sends them to the command server of the criminals. They can also launch DDoS attacks, download and run random software. All five samples download and run the Trojans of the Zbot family designed to attack servers and PCs as well as to intercept user data. Although the Trojan is capable of different malicious activities, it is most often used to steal banking information. It can also install CryptoLocker, a malicious program which demands money to decrypt user data. Trojan-PSW.Win32.Fareit.anai also loads the Trojan that installs a malicious extension for the browser capable of looking through the user’s search requests on major search engines and replacing the results in the interests of the criminals. The malicious programs of the Fareit family steal the wallets of Bitcoin and around 30 other virtual currencies.
Fifth place was occupied by the net worm Asprox designed to spread spam. It automatically infects sites, loads and runs other programs, and collects valuable information stored on the computer such as passwords and other data to access email and FTP accounts.
The Top 10 was rounded off by Email-Worm.Win32.Bagle.gt., an email worm which sends copies of itself to all email addresses found on an infected computer. The worm also downloads files from the Internet without the user’s knowledge. Email-Worm.Win32.Bagle.gt uses its own SMTP library to send infected messages.
The USA (+3.5 percentage points) topped the rating of countries with the highest number of mail antivirus pushing the UK down to second (-3.41 percentage points). Germany remained third with a decrease of 0.39 percentage points compared to the previous month.
Russia’s share of the total number of mail antivirus detections worldwide was up to 2%. The shares of Mexico and South Africa grew significantly meaning these countries entered the Top 20 in seventeenth and eighteenth places respectively.
Special features of malicious spam
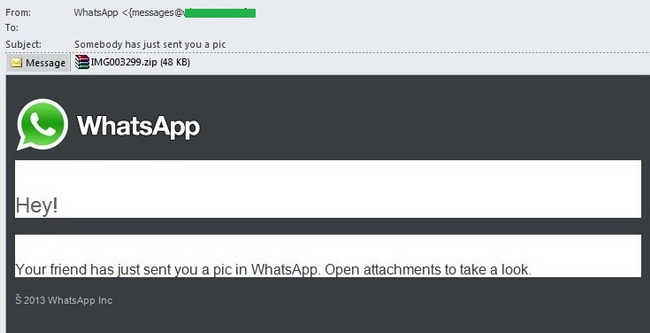
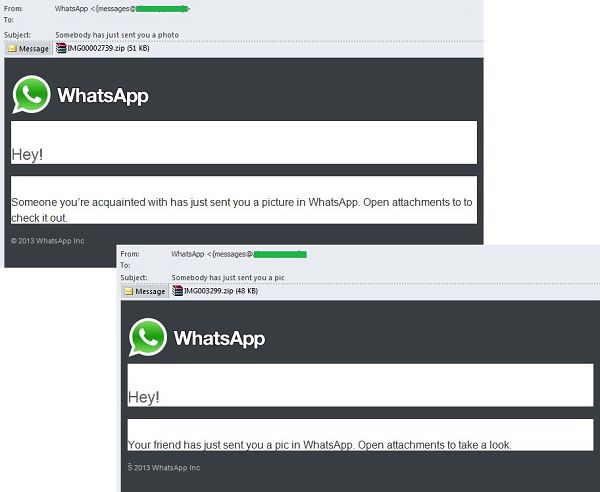
Last month the fraudsters focused on users of the cross-platform messenger WhatsApp whose worldwide popularity is growing rapidly. The messenger allows users to send text messages and exchange images, and video and audio files. The fact that WhatsApp is currently only available on smartphones and creating a WhatsApp account does not require an email account, did not prevent the criminals from sending out spam notifications via email.
In January, we came across fake notifications from WhatsApp which said that one of the user’s friends or just “your friend” had sent him a photo or an image. The attached archive actually contained a malicious program detected by Kaspersky Lab as Backdoor.Win32.Androm.bjkd., a notorious backdoor whose main functionality is to download other malware on the victim computer.
Phishing
The ranking of organizations attacked by phishers did not change significantly in January.
The ranking is based on Kaspersky Lab’s anti-phishing component detections that are triggered every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
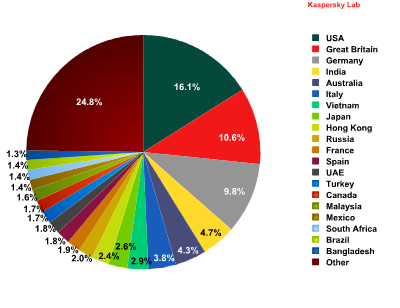
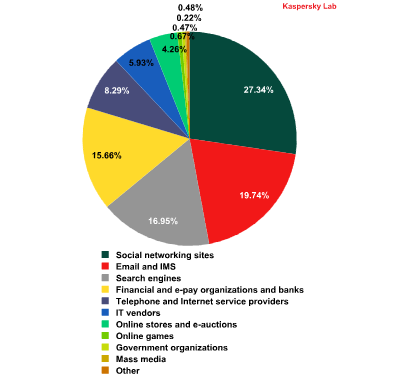
First place was once again occupied by social networking sites (27.3%), which increased their contribution by 0.9 percentage points. The shares of email services (19.7%) and search engines (16.9%) increased slightly and these categories remained in second and third positions in the ranking respectively.
Financial and e-pay organizations (15.7%) remained in fourth place despite the category’s share falling by 0.2 percentage points compared to the previous month.
The percentage of the telephony and internet service providers (8.29%) and IT vendors (5.93%) categories dropped slightly, though this did not affect their ranking – they remained in fifth and sixth positions respectively.
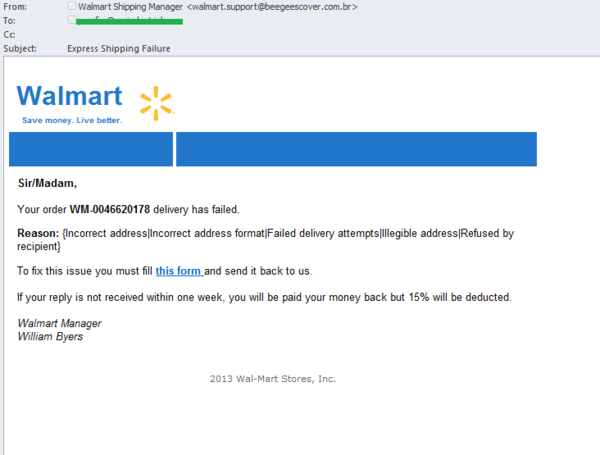
January saw phishers send out fake notifications from a number of popular online stores. The recipients of the fraudulent email signed by the “manager” of the American retail chain Walmart were informed that their order had not been delivered. To resolve the problem, they were asked to fill in a form and send it back within a week. The message was designed in the official corporate style, included the company’s logo and an auto signature at the foot of the message – all this was intended to convince the user that the email was legitimate. However, the recipient should have been suspicious by the fact that the email didn’t address them personally by name and the fact that more than one reason was given for the delivery not being made.
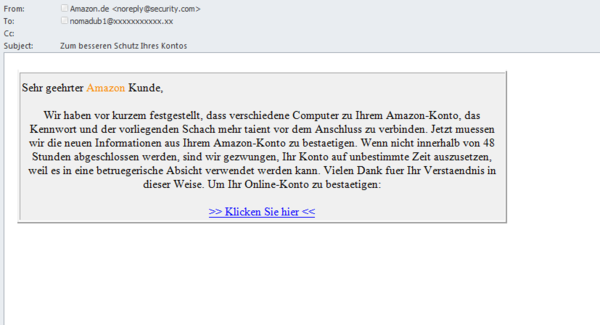
In January, we also came across a German-language phishing mass mailing that was using the Amazon store name. The recipient was informed that the service had registered an attempt to access their account from someone else’s computer. The recipient was asked to confirm the account information within 48 hours; otherwise, it would be blocked. The email contained a link to the phishing page. It’s worth noting that the email did not have the slightest resemblance to a legitimate message. It appears the scammers were hoping the recipients were inexperienced or inattentive, while using a legitimate looking email address in the From field.
Conclusion
The share of spam in global email traffic decreased by 7.6 percentage points and averaged 65.7% in January. As forecasted, the drop in the share of spam was due to a lull early in January when there is less business activity and a large number of botnets are turned off.
Spam mailings contained adverts for gifts as well as services offering to organize various events or trips. Yet another holiday, Valentine’s Day, was exploited in both English- and Russian-language spam. We registered traditional mass mailings from ‘flower’ partner programs advertising romantic dinners and numerous other gift offers.
As expected, spammers continued to send out ‘Nigerian’ letters exploiting the theme of Nelson Mandela’s death. This time the scammers passed themselves off as the wives or assistants of the late president. January also saw Ariel Sharon’s death used to trick users.
Yet another important event exploited by the fraudsters was the Olympic Games in Sochi. Mass mailings were detected in January with adverts for fake designer goods and accessories with the logo of the Games.
The January rating of organizations targeted most often by phishers saw little change from the previous month. Social networking sites remained in first place with an increase of 0.9 percentage points. They are followed by the email and instant messenger, and search engine categories whose shares also grew slightly.
Popular social networking sites and instant messenger services maintained remained the targets of choice for fake notifications containing malicious programs. January saw malicious notifications made to look as though they were sent from the WhatsApp cross-platform messenger for smartphones.























Spam Report: January 2014