
Contents
- April in figures
- Spam in the spotlight
- The geographical distribution of spam sources
- Malicious attachments in email
- Phishing
- Conclusion
April in figures
- The percentage of spam in email traffic was up 2.1 percentage points compared with March and averaged 72.2%
- The percentage of phishing emails decreased by a factor of three compared with March, dropping to 0.002%
- In April, malicious files were found in 2.4% of all emails, a decrease of 1.6 percentage points
Spam in the spotlight
In April, the quantity of spam emails grew very slightly – by 2.1 percentage points. The amount of ‘holiday’ spam fell, even though spammers continued to actively exploit the Easter theme for spreading fraudulent emails and messages containing adverts for goods and services. Additionally, they tried to draw users’ attention with the names of the world political leaders and tragic events which happened in the US.
Events in the US and malicious spam
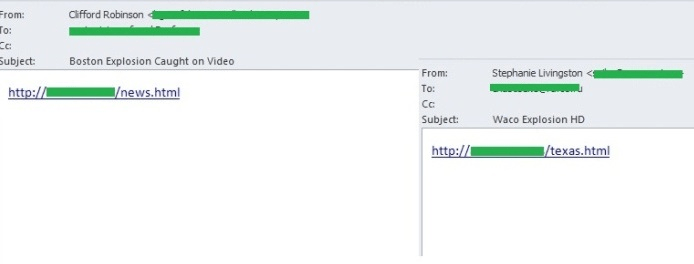
As usual, the month’s biggest news stories did not escape the spammers’ attention. In April, the fraudsters exploited the double bomb blasts at the Boston Marathon and an explosion at a chemical plant in Texas.
Within a day of the bombings we registered several mass mailings containing malicious files or links in spam traffic. One of these mass mailings was described in detail in our blog.
The emails imitated mass mailings from popular news sources (CNN and BBC) and contained a provocative headline plus a link to a supposed article about the tragic events. On clicking the link, the user was directed to a fraudulent site which used the Blackhole 2 exploit folder to attack the system. If this succeeded, Backdoor.Win32.Papras.ppk was downloaded on the user’s computer. This malicious spyware is designed to steal information from protected browser connections (HTTPS), cookies, screenshots and computer data (installed programs, OS configuration) and transfer it to cybercriminals.

Noticeably, a similar malicious mass mailing was registered in Q1 2013. Emails with a very similar design were used by the fraudsters to spread news about the new Pope in March.
Yet another mass mailing was used to distribute links to web pages containing the words Texas, Boston and news in the address. The link sent users to a web page with a selection of videos of bombings taken from YouTube. This page also contained an exploit which downloaded a malicious program detected by Kaspersky Lab as Trojan-PSW.Win32.Tepfer on the user’s computer. This Trojan was created to steal user account details (logins and passwords) from infected computers.
Fraud
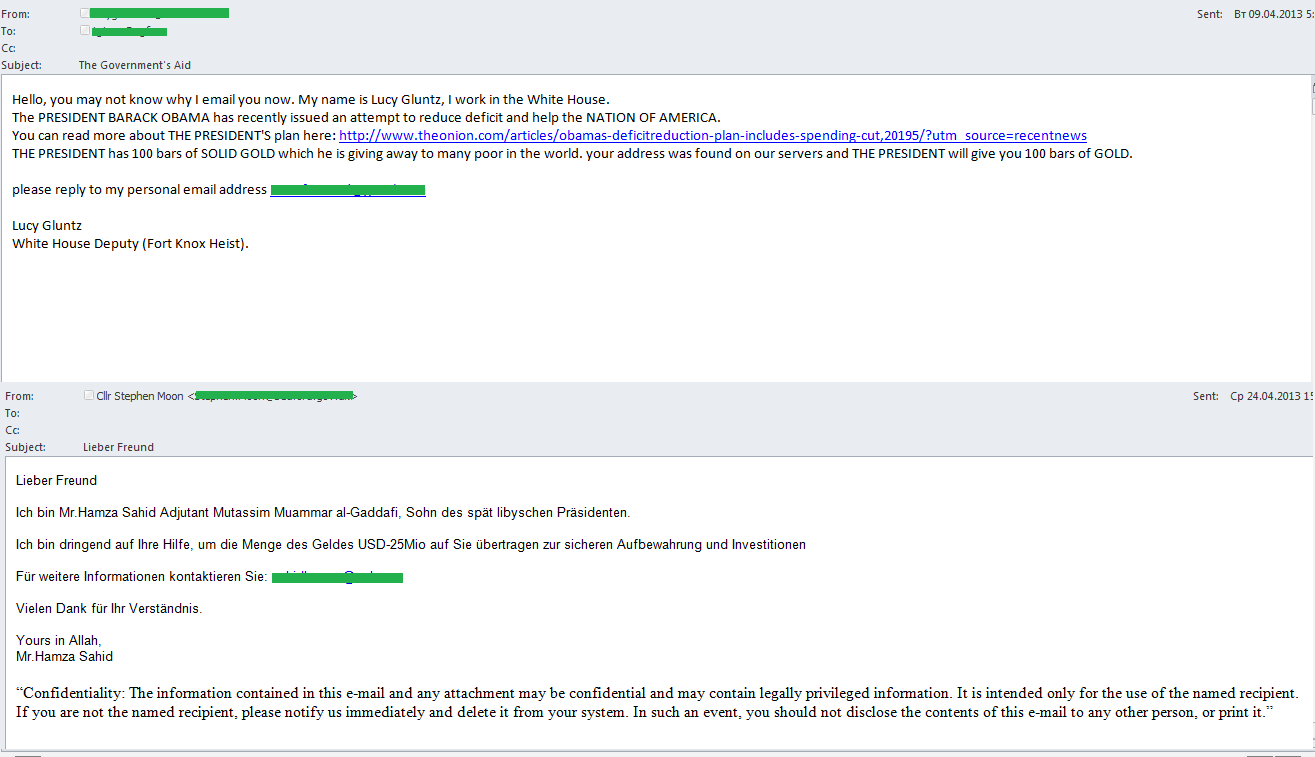
In April, ‘Nigerian’ fraudsters continued to use the names of famous political leaders in their emails – this time it was Barak Obama and the son of Muammar Gaddafi. For example, an email sent on behalf of a White House employee claimed that the American President was giving 100 gold bullions to needy people around the world and the recipient of the email was one of the chosen ones. A German-language ‘Nigerian letter’ written on behalf of the assistant of former Libyan president Muammar Gaddafi’s son contained the traditional request for help in saving and investing his mythical millions.
This type of fraud is well-known: once the victim is involved in the correspondence, the scammers ask for a relatively small sum of money to cover the middleman’s expenses or drawing up documents. The spammers believe that the huge gap between the money demanded and the promised rewards will make the potential victim throw caution to the wind and hand over the cash.
Nigerian fraudsters tried to grab users’ attention not only by promising ‘easy money’ but also by sending Easter greetings (the holiday was mentioned in the heading of the email and in the beginning of the message).
Traditional fake notifications of lottery wins also exploited the Easter theme and were spread with the word ‘Easter’ in the Subject field. One such email contained a link to the legitimate site of a real company which, however, had nothing to do with the ‘lottery’ organized by the fraudsters.
Holiday spam
Although Catholics had already celebrated Easter, spammers continued to actively exploit the theme in April, offering counterfeit goods and credit deals. For example, one mass mailing offered recipients a special ‘Easter’ code which allowed them to buy replicas of designer watches at a 50% discount.
In April, we again registered mass mailings dedicated to Mother’s Day. As previously, they advertised flowers and fake designer goods.
Yet another mass mailing offered cigars for the coming Father’s Day celebrated in the US in June.
The geographical distribution of spam sources
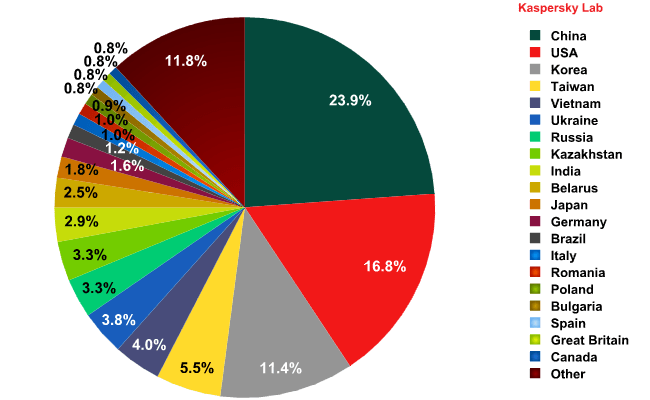
April saw no changes in the Top 3 leading sources of spam worldwide. China (23.9%) remained in 1st place despite a 2 percentage point fall in its share. The amount of spam sent from the US decreased slightly (16.8%) leaving this country 2nd in the rating. Overall, these two countries produced 41% of global spam.
Sources of spam around the world by country
In April, South Korea (9.8%) came third with an increase of 1.5 percentage points. Taiwan (5.5%) remained in the Top 5. India, which was 5th in March, lost 0.5 percentage points and fell to 9th place in the rating with 2.9% of all distributed spam. Russia (3.3%) increased its contribution by 1 percentage point and climbed from March’s 10th place to 7th. Germany was down 1 percentage point and dropped from 8th to 12th. Italy lost 2.1 percentage points and fell from 6th to 14th position.
Sources of spam in Europe by country
South Korea was the main source of spam sent to European users in April (43.4%): its share grew by 6.6 percentage points. Alternatively, China’s contribution fell significantly and averaged 3.7%, meaning it dropped from 2nd to 5th position.
The US remained in the Top 3 although its share fell by 3.4 percentage points. Vietnam (5.2%) climbed from 5th place to 3rd. Meanwhile, Italy saw its share reduced by a factor of three, falling from 4th to 11th position with 1.9% of spam sent to European users.
Sources of spam by region
Asia (55.7%) remained the leading source of spam by region. As in March, the Top 3 also included North America (17.6%) and Eastern Europe (13.6%).
Malicious attachments in email
In April, malicious attachments were detected in 2.4% of emails, a decrease of 1.6 percentage points from March.
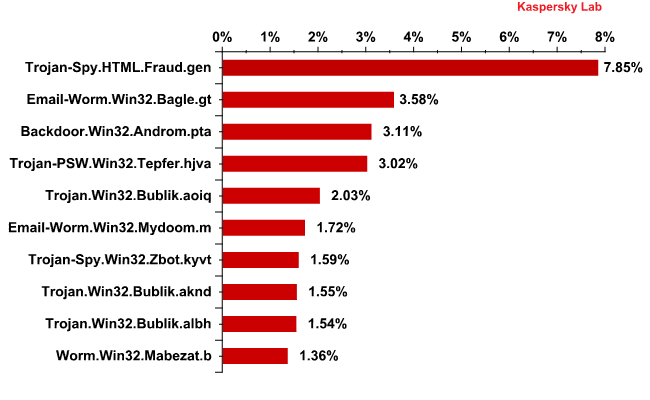
TOP 10 malicious programs spread via email in April 2013
In April, Trojan-Spy.html.Fraud.gen remained the most widespread malicious program. This malicious program appears in the form of HTML pages which imitate the registration forms of well-known banks or e-pay systems and are used by phishers to steal user credentials for online banking systems.
Email-Worm.Win32.Bagle.gt. came 2nd. This mail worm’s functionality is to self-proliferate to addresses in the victim’s address book, which is typical for this type of malware. It can also contact the command center and download other malicious programs onto a user’s computer.
In fourth place is Trojan-PSW.Win32.Tepfer.hjva, developed to steal passwords to users’ accounts.
Fifth, eighth and ninth positions in the rating are occupied by the malicious programs of the Trojan.win32.Bublik.aknd family. They harvest user passwords for FTP, email services credentials and certificates from infected computers. It can scour forms in Mozilla Firefox and Google Chrome in search of saved logins and passwords before forwarding the data it finds to the fraudsters.
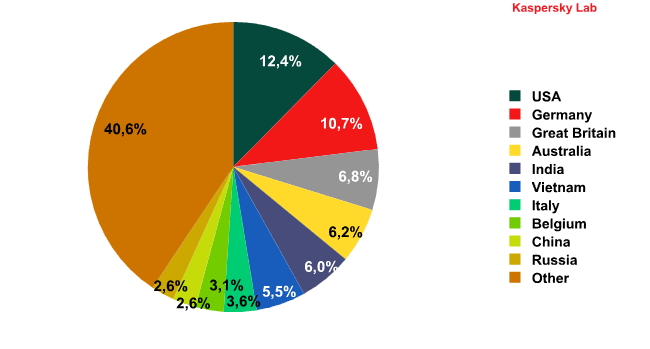
Distribution of email antivirus detections by country
The US (12.4%) and Germany (10.7%) maintained their leadership in the rating of countries that are most heavily targeted by malicious emails. In April, they were joined by the UK (6.8%), which came 3rd. The rest of the Top 10 members remained unchanged from March.
In April, spammers actively used the name of the international logistics company DHL to spread fake notifications with malicious attachments. We registered several mass mailings in English and Dutch.
The English-language mass mailing informed the user that the alleged DHL courier had failed to deliver the parcel which was now due to be picked up in the company office. To do this, the user had to print out the parcel detains containing in the attached archive. The fraudsters usually try to exert pressure on the user, threatening additional charges for storing the parcel if isn’t collected promptly. The size of the fine and the deadlines vary from email to email.
The attached archive DHL.REPORT.ID680.zip included the DHL.REPORT.F3B5DJ7.exe file (the numbers changed from email to email, but the name of the executable file was the same in every case). Not surprisingly, this file did not contain any information about a non-existent parcel. This was a Trojan program of the ZBot (ZeuS) family, specifically Trojan-Spy.Win32.Zbot.krhu.
ZeuS has been actively used by the spammers not only to steal users’ personal information and passwords to e-pay and banking systems but to create botnets. Due to its simple configuration and the ease of use, ZeuS has become one of the most dangerous and widespread examples of spyware.
The Dutch-language email informed the user that the attached file contained a bill for DHL services. In fact the archive Uw recentste DHL factuur.zip included the Uw recentste DHL factuur.pdf.exe file detected by Kaspersky Lab’s heuristic technologies as Trojan.Win32.Generic.
Fake notifications from e-stores are also popular with fraudsters who spread malicious files. In April, we registered a mass mailing containing fake notifications sent on behalf of the popular German e-store OTTO. Interestingly, the “From” field had a sender which appeared legitimate at first sight – otto-newsletter. This is a popular trick used to deceive the user.
The user is thanked for ordering with OTTO but nothing is said about opening the attached file. Probably, the fraudsters believe the user’s curiosity will make him open the archive Besstellung_bei_OTTO.zip, detected by Kaspersky Lab as a Trojan of the Trojan.Win32.Bublik family. It is used by scammers to harvest logins, passwords and other sensitive information saved on infected computers. In April, one representative of this family occupied 5th place in the rating of malicious programs most often distributed via email.
Phishing
The percentage of phishing emails decreased by a factor of three compared with March, falling to 0.002%
The distribution of the Top 100 organizations targeted by phishers, by category*
*This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In April, the Top 5 organizations most often targeted by the phishers saw no major changes. Social networking sites continued to be the most attractive target for phishing attacks: their share grew 1 percentage point and averaged 35.5%. The Top 3 also included Financial and e-pay organizations (17%) and Search engines (15.3%) which came 2nd and 3rd respectively.
IT vendors remained in 4th position (9.1%). They were followed by Telephone and Internet service providers (8.7%).
Conclusion
As expected, in April the amount of holiday-related spam decreased. We registered mass mailings exploiting the Orthodox Easter theme, and scammers used it not only to advertise goods and services but also to deceive users. Fraudulent mass mailings containing the names of the popular political leaders were also quite frequent in April’s spam flows.
Tragic events are seldom ignored by spammers. April 2013 was no exception. After the bombings in Boston, the Internet was flooded with malicious mass mailings exploiting the event. In general, the total amount of spam in April grew very slightly.
In April, the majority of world spam originated from China and the US. South Korea remained the unsurpassed leader in spam distribution to European users. Together with the US (2nd place) it generated half of all European spam. Vietnam came 3rd in the rating.
The quantity of phishing emails decreased by a factor of three, but there were no major changes in the Top 5 organizations most often attacked by phishers. As in March, social networking sites topped the rating and we expect they will maintain their position in May. Most likely, next month will see growth in the Online games category: during the summer holidays schoolchildren and students are usually more active as they use different social and entertainment services online.





























Spam in April 2013