
January in figures
- The amount of spam in email traffic remained unchanged compared to December and averaged 76.2%.
- The percentage of phishing emails also remained unchanged compared to the previous month and accounted for 0.02%.
- Malicious files were found in 4.3% of all emails, an increase of 0.3 percentage points compared to December’s figure.
Spam in the spotlight
Early Valentine’s cards
In January, more than a month before Valentine’s Day, our spam lab usually starts registering the first emails exploiting the Valentine’s theme. 2012 was no exception – last month mass mailings containing “Valentine’s” offers flooded the Internet.
This type of spam message traditionally contains adverts for fake designer goods and medication to boost the male libido. In order to grab the users’ attention, spammers are actively exploiting this particular holiday – recipients are invited to buy their nearest and dearest a replica of a Swiss watch or a pill to increase potency.
Seasonal partner programs containing adverts with the trappings of this day of romance increase their activity as 14 February approaches. In particular, partner programs offering flowers blossom at this time of year with participants getting a cut from every customer that they attract. These sorts of programs distribute the lion’s share of Valentine’s spam.
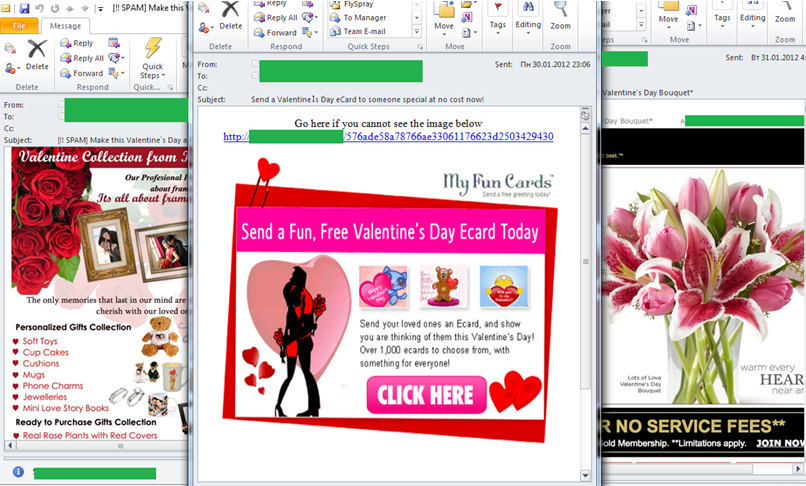
Spam emails exploiting the Valentine’s Day theme
In January spam traffic included Valentine’s e-cards to be sent on the big day. Knowing such greetings cards often contain malicious code we decided to have a closer look at one of these mailings. Contrary to our expectations, the link did not lead to a malicious program, but there was no e-card there either. More details about the results of our research are available in our blog.
In 2011, fraudsters distributed malware masked as e-cards less frequently than usual. However, users should not completely discount this risk, especially on a major date in the calendar. Spammer tricks do not disappear – they leave the stage and then come back again.
Political spam
The year 2012 promises to be packed with political events of international importance. In March Russia will elect its president. In April-May presidential elections will be held in France and finally in November US citizens will vote for their new president.
Previous years, especially 2011, demonstrated that political activity in various forms is familiar territory for spammers. In January 2012 it became evident that the amount of political spam in the coming year would not decrease.
Radical emails calling for revolution in Russia continued to appear on the RuNet in January. No “constructive” mass mailings from the supporters of this or that political faction were registered in January, although we expect to see them in February, the final month of presidential campaigning.
US spammers are also actively demonstrating their political stance even though the elections are almost a year away. Spam traffic often includes emails containing a “shocking video” of Barack Obama or “awful facts” about the current president. Additionally, American spammers have been distributing messages canvassing for other potential candidates in order to “end the Obama era”.
Interestingly, French spam lacks any political overtone. In January we failed to register a single French-language message exploiting the election theme.
The Olympic Games
Sporting themes have also become “newsworthy” for the fraudsters. The 2012 Olympic Games is the bait exploited by “Nigerian” spammers to distribute emails containing fake notifications of Olympic lottery wins. Advanced Internet users have no difficulty in recognizing them as fraudulent messages, but less experienced users can easily fall victim to such scams.
Statistical summary
Sources of spam
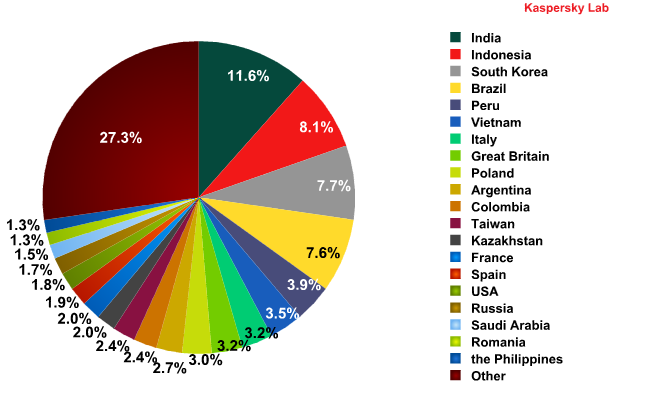
The Top 20 sources of spam in January 2012
In January the UK re-entered the list of ten most popular sources of spam, pushing Colombia off the list and taking 8th place. In December the UK had dropped out of the top 10, possibly because the holiday season saw many botnet computers switched off. The rest of the rating remained unchanged from December, although some entries swapped places.
India maintained its leadership having distributed 11.5% of the total quantity of spam (-1 percentage point). Indonesia’s share decreased compared to December’s figure by almost 3 percentage points which, however, could not prevent it from taking 2nd place in the rating. Indonesia was followed by South Korea (+1.6 percentage points).
Brazil and Peru came 4th and 5th. The amount of spam originating from these two countries decreased by 2.1 and 2.5 percentage points respectively.
As in December, 6th position in January was occupied by Vietnam, whose contribution to world spam dropped by 0.25 percentage points.
Thus, the first six places in the rating of the most popular spam sources were occupied by Asian and Latin American countries.
Italy (-0.25 percentage points) and the UK (+1.95 percentage points) in 7th and 8th positions were the highest entries from Western Europe. The share of the other Top 20 members fluctuated within a range of 1 percentage point.
Malware in mail traffic
Malicious files were found in 4.3% of all emails in January, an increase of 0.3 percentage points compared with the previous month.
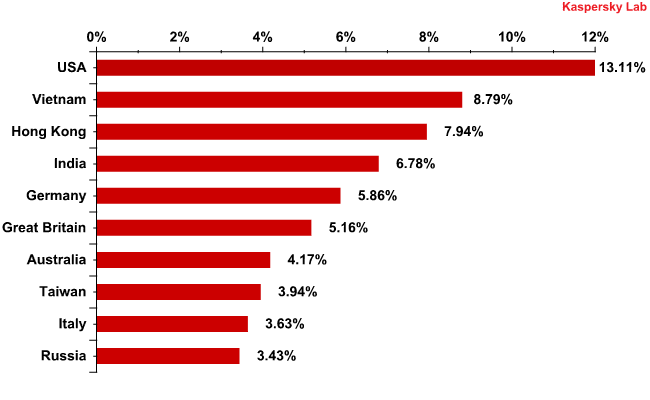
Countries where mail antivirus detected malware most frequently in January 2012
The USA took the lead in the rating of the countries where mail antivirus detected malware most frequently. However, this was not because Kaspersky’s mail antivirus component detected more malware in US mail traffic (-2 percentage points) but rather the result of a considerable drop in the number of antivirus detections from last months’ leader – the Russian share decreased by 11 percentage points.
This fall was not caused by the holiday season. On the contrary, at the beginning of January the percentage of antivirus detections on the Russian segment of the internet was 3-4 times higher than in the second half of the month.
Among other significant shifts in the rating, Germany’s figure is worthy of special mention – the share of antivirus detections in this country doubled compared to the previous month.
The share of the other Top 10 members fluctuated within a range of 1.5 percentage points.
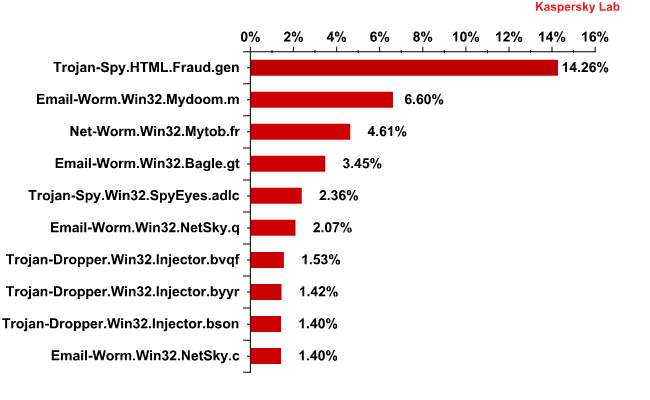
The Top 10 malicious programs distributed via mail traffic in January 2012
Trojan-Spy.HTML.Fraud.gen again topped the list of the 10 most popular malicious programs distributed via email in January: over 14% of all antivirus detections fell on this long-term leader of the rating, an increase of 3 percentage points compared with December’s figure.
Trojan-Spy.HTML.Fraud.gen uses spoofing technology and appears in the form of an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password.
Email-Worm.Win32.Mydoom.m, Email-Worm.Win32.Bagle.gt, Email-Worm.Win32.NetSky.q and Email-Worm.Win32.NetSky came 2nd, 4th, 6th and 10th respectively. Three of them – Mydoom.m and both mail worms of the NetSky family – are malicious programs whose only functions are to harvest email addresses and to send copies of themselves to these addresses. Bagle.gt is yet another mail worm, but as well as the usual functionality it downloads malicious programs from Internet resources.
In 7th to 9th positions in January’s Top 10 malicious programs most frequently detected by our mail antivirus we see programs of the Trojan-Dropper.Win32.Injector family. Trojan-Dropper programs are designed to secretly install malicious programs to victim computers as well as to bypass antivirus filtering.
Phishing
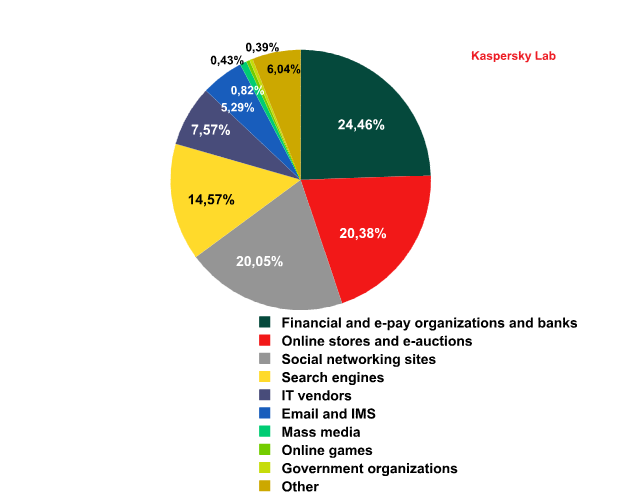
Top 100 organizations, by sphere of activity, targeted by phishers in January 2012 (based on anti-phishing component detections)
This year sees the start of Kaspersky Lab’s new listing of the top 100 organizations targeted by phishers, grouped by category. The rating is based on our anti-phishing component detections activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
According to KSN, phishing links are clicked from mail clients in about 65% of cases, which means email remains the main distribution channel for phishing links. In about 26% of cases phishing links are clicked directly from Internet browsers. These include links clicked on webmail interfaces and social networking sites as well as the links to phishing sites which come out on top in search engine queries due to the use of black SEO technology.
The Top 100 organizations targeted by phishers can be broken down into nine categories:
- Financial and e-pay organizations, banks. As the name suggests, this category includes banks whose clients have become victims of phishing attacks registered by Kaspersky Lab. It also includes e-pay systems such as Visa, MasterCard, PayPal as well as credit institutions, unit trusts, investment companies, etc.In January, this was the top category. Almost a quarter of the anti-phishing component detections came from phishing sites designed to steal users’ bank and e-pay accounts.
- Online stores and e-auctions. User accounts in many online stores are aligned with their credit cards and contain personal information (for example, a name, an email address, a postal address, a telephone number, etc.). When making a purchase in a fake online store a user enters his credit card information which then becomes the trophy of the fraudsters. No wonder, then, that 20.38% of all anti-phishing component detections fell on phishing attacks targeting different stores and auctions.
- Social networking sites. User accounts on social networks remain a tasty tidbit for fraudsters because they are in great demand on the black market. The share of anti-phishing detections on phishing sites targeting social network accounts is a little less than the figure for online stores (20.05%).
- Search engines. This category included search engines where services were affected by registered phishing attacks. Almost every search engine, in addition to Quick Search, offers its users other services including email. Some search engines have their own social networking sites and e-pay systems. The percentage of anti-phishing detections on the sites designed to steal users’ accounts on different services offered by the search engines accounted for 14.6%. Google and Yahoo! topped the list in this category.
- IT vendors. Many software and hardware vendors have web services which can be accessed (to pay for the services or grocery orders or to download updates) only after registration. In order to make the purchasing process easier for the user, financial information such as bank card details are often stored on the service account. Some vendors, Microsoft in particular, offer additional services such as IMS or email. Their accounts are also attractive for the fraudsters. Thus, Microsoft and its brainchild Xbox, Apple and its services and Electronic Arts have become the focus of their attention. In January, the share of anti-phishing detections on the sites used to attack IT vendors reached 7.6% of all anti-phishing detections.
- Email and IMS. Email and IMS accounts are also among phishers’ targets due to their popularity on the black market. In January, the percentage of anti-phishing detections of attacks on email and IMS users accounted for 5.3%. This category does not include email services provided by search engines. The fact is that if the fraudsters get access to an email account provided by a search engine they can also access other services offered by this company which makes it impossible to identify the final target of the attack.
The other three categories only accounted for less than 1% of all anti-phishing detections in January. - Mass media. This category includes phishing attacks which target the accounts of users registered on different news sites. These accounts may be somehow aligned with social network accounts, which are the fraudsters’ real targets. It is possible that these attacks are ordered by competitors in order to besmirch the reputation of the compromised portals. There were cases when the attackers got access to the accounts of users who had editing rights on the sites. Cybercriminals used these rights to post information or malicious links on news sites. The accounts had probably been stolen during phishing attacks. Either way, 0.8% of all anti-phishing detections fell into this category.
- Online games. The amount of anti-phishing detections of attacks targeting the accounts of online gamers accounted for 0.4%.
- Government organizations. The same percentage of attacks (0.4%) fell on the accounts of users registered on the sites of government organizations. As mentioned before, these attacks have a seasonal character. Most of them are launched when tax returns are due to be filed in the US and the UK because the tax organizations in these countries are the phishers’ preferred targets among all government agencies.
The “Other” category includes mobile operators, Internet providers and some other organizations. In most cases the accounts of the users on these sites also contain financial information.
Spam by category
The top two categories in English-language spam have not changed compared to December. Fraudulent emails remained on top despite a slight drop (-1.6 percentage points) in its share while the percentage in the Personal Finance category grew slightly (+3.3 percentage points).
The amount of spam messages in the Education category doubled. In January spammers were especially persistent in inviting users to get a degree in graphic design.
The share of the Computers and the Internet category increased fourfold in January. More than half of all spam messages registered by Kaspersky Lab offered cartridges for photocopying machines.
Conclusion
In practice, the “Valentine” mass mailings are not as numerous as those spread in the run-up to Christmas and the New Year. In the second week of 2011, the peak of their distribution, Valentine spam accounted for just 0.21% of the total quantity of spam and there is no reason to expect any considerable growth this year. However, emails exploiting the Valentine theme will no doubt be evident in the first half of February.
To recap, one of the traditional types of spam at this time of year is malicious messages imitating Valentine’s Day cards. Over the last few years this type of spam has not been encountered frequently in spam flows, but the risk should not be ignored. Users should be particularly vigilant with all emails received in this period. It is especially dangerous to open an .exe link because it may well contain malicious code instead of a declaration of love.
It is worth noting that the amount of spam with malicious attachments is not declining and has maintained its rather high level – 4.3%. Additionally, the Computer Fraud category tops the rating of the most popular spam categories. These two factors combine to make English-language spam very dangerous for users.























Spam report: January 2012