
The Internet knows no borders, but according to our data, cybercrime has specific ‘geographical features’. In different parts of the world cybercriminals launch different malicious programs, their attacks have different priorities and they use different tricks to make money. This is not just due to their physical location, but also due to the nature of the countries where their potential victims are located. The key factors in this case are the level of economic development, the number of Internet users and the level of Internet penetration in the country.
In this article we will analyze the specifics of cybercriminal activity in western countries: the USA, Canada and Western Europe (the UK, Austria, Belgium, Denmark, France, Germany, the Netherlands, Luxembourg, Ireland, Italy, Spain, Switzerland and Portugal).
Summary
- GDP (by purchasing power parity, source: cia.gov):
- USA — $14.66 billion (2010 est.), 2nd in the world;
- EU — $14.82 billion (2010 est.), 1st in the world.
- Number of Internet users (source: cia.gov):
- USA – 245 million, 2nd in the world;
- Germany – 65.125 million, 5th in the world;
- UK — 51.444 million, 7th in the world;
- France — 45.262 million, 8th in the world;
- Italy — 29.235 million, 13th in the world.
- Level of Internet penetration (source: http://www.internetworldstats.com/):
- North America — 78.3%, 1st in the world;
- Europe – 58.3%, 3rd in the world.
- Internet use:
- The Internet is everywhere: in schools, public institutions, at home and at work.
- The internet is always at hand: mobile Internet is very cheap, mobile devices (tablets and smartphones) are very common
- The Internet is widely used to pay for public services, to make online purchases and to manage bank accounts.
- The percentage of users exposed to Internet attacks (H1 2012):
- USA – 38.8%, 31st in the world;
- Germany — 28.8%, 101st in the world;
- UK — 36.8%, 42nd in the world;
- France – 36.3%, 44th in the world;
- Italy – 43.5%, 18th in the world;
- EU – 32.1%.
- Lots of Mac OS X users, more and more smartphones running Android OS
- Operating systems most frequently targeted by cybercriminals:
- Windows
- Android
- Mac OS X
Almost half of the western countries analyzed are among the Top 20 countries with the most Internet users – and those users are very active. Most consider the Internet not only a source of information but also the easiest way to keep in touch and the most accessible way to make purchases and payments. Additionally, in western countries people keep most of their savings in banks and actively use online or mobile banking systems to manage their bank accounts.
At the same time, computers in these countries are often well protected and are difficult for cybercriminals to penetrate. Western users have sufficient skills and knowledge to protect their computers against infection. In particular, installing an antivirus program is considered a basic security measure for users in the US and Western Europe.
Users in Western Europe and North America are quick to migrate to new versions of operating systems, making it harder for cybercriminals to find ways around IT security systems. For example, in the first half of 2012 more than half of computers (62.4%) in these countries were running under Windows 7. That is 6 percentage points higher than the global average.
With each new update of an operating system, integrated security solutions become more advanced. Current operating systems incorporate several mechanisms to combat malware: DEP, ASLR, restrictions on installing drivers without digital signatures, etc. In addition, most operating systems are licensed. This enables them to automatically receive updates which are often critical for security.
Specific features of malicious programs
The level of information security in Western countries forces cybercriminals to develop new technologies. The malicious programs distributed by malware authors in these countries share a high level of technical complexity. North American and Western European users in effect become guinea pigs for cybercriminals to test their latest creations: technologies designed to infect computers that hide malicious code in the system, as well as various mechanisms for making money.
The cybercriminals’ main target in this region is money and Trojan programs are the tool of choice when it comes to stealing it.
All Trojan programs distributed in Western countries can be divided into four groups.
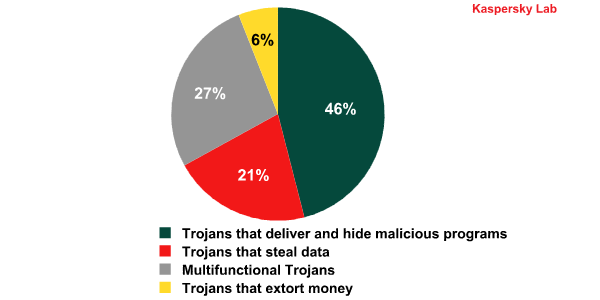
Distribution of Trojan programs by type. Western Europe and North America, H1 2012
The largest group is that of Trojans that deliver other malicious programs to users’ computers. Because malware authors continually produce modifications to try to evade antivirus defenses, there are a huge number of these. Meanwhile, the targeted delivery of malicious programs has given rise to a separate type of shady business practices.
Cybercriminals are especially interested in the second group of programs, which monitor user activity and steal important information. The most dangerous of these are Trojans targeting information to access online banking systems such as Trojan-Banker, Trojan-Spy.Win32.Zbot, Trojan-Spy.Win32.Spyeyes and Backdoor.Win32.Sinowal. If one of these programs successfully infects a computer, the fraudsters get access to the user’s bank account and can use that money at their own discretion.
Another group of Trojans are designed to extort money from the users on some pretext or other. They include rogue antivirus programs and ransomware.
Multifunctional Trojans perform two or more functions such as stealing the user’s data and downloading other malicious programs to the computer.
Money
| Main ways of making money | Malicious programs used by cybercriminals (according to Kaspersky Lab classification) |
|---|---|
| Financial data theft (Getting access to finance-related accounts; Internet banking, PayPal, Ebay) |
Trojan-Banker, Trojan-Spy, Backdoor |
| Installation and sale of rogue antivirus programs | Trojan-FakeAV |
| Theft of accounts to paid services, online games and services (Steam, WoW, Facebook, Skype, etc.) | Trojan-PSW, Trojan-GameThief, Trojan-Spy |
| Personal data theft | Backdoor, Trojan-Spy |
| The substitution of search results, ads, click fraud | Trojan-Clicker, Trojan.Win32.DnsChanger, Backdoor |
| Blackmail | Trojan-Ransom |
Let’s take a look at how cybercriminals are profiting at the expense of users’ compromised computers or mobile devices.
Financial data theft
Internet banking makes users in the US, Canada and Western Europe an attractive target for cybercriminals. The most notorious Trojans designed to collect financial data are widespread in these regions.
- Sinowal (Mebroot) — a backdoor which steals financial information. In order to get into the system it infects the first boot record on the hard drive.
- Zbot (ZeuS) — a universal Trojan which targets the accounts of many banks. Malware writers are actively developing it based on the source codes of the second version, which have been posted on the Internet.
- SpyEye — a universal Trojan which targets the accounts of numerous banks. It is a competitor to Zbot (ZeuS), but there are no free source codes available on the Internet.
In the first half of 2012 the US, Canada and West European countries accounted for 70% of all Backdoor.Win32.Sinowal (Mebroot) attacks, 41% of Trojan-Spy.Win32.SpyEye attacks and almost a quarter of all the Trojan-Spy.Win32.Zbot attacks that were repelled.
Besides user bank accounts, cybercriminals are interested in getting access to PayPal and E-bay accounts: 34% and 9% respectively of all phishing attacks target these e-pay services. In both cases the accounts are linked to bank cards, allowing the fraudsters to steal money. In addition to account information phishers usually try to extort other personal data, e.g. social security numbers, dates of birth and credit card cvv2 security codes.
European and American banks and e-pay systems are taking this problem seriously, and offer a variety of ways to protect users: authentication using e-tokens, one-time passwords, confirmation of transactions through codes sent to the phone, etc. However, cybercriminals are developing programs to bypass these measures. For example, the Zitmo family of programs is designed to attack a user’s mobile phone and can bypass the two-factor authentication systems of European banks. These mobile malicious programs work in tandem with Zbot (ZeuS): at first Zbot steals the username and password to enter the online banking system from the infected computer and then, during a money transfer, its mobile counterpart Zitmo takes over to forward the transaction authorization code (TAN) to the cybercriminals.
Official data gives an idea of how lucrative financial cybercrime can be. Those arrested in 2010 managed to withdraw $9 million from more than 600 accounts in three months of using Trojan-Spy.Win32.Zbot. And this is only the amount of money which could be traced. With so many different groups of cybercriminals out there, the total revenue plundered is likely to be 10 times this figure.
Personal data theft
Personal data theft plays a major role in cybercriminal activity in North America and Western Europe. Hacker forums offer customer databases from different stores and services. With so much information on offer the prices are rather low – just a few cents (in the case of wholesale purchases) for information about one person. However, information about thousands of different users of various services usually ends up in the hands of hackers as a result of vulnerabilities or mistakes in configuring servers and databases.
The most widespread vulnerabilities which lead to data leaks are SQL injections, Insecure Direct Object references, and Broken Authentication and Session Management. However, in addition to vulnerabilities, cybercriminals use mistakes in the configuration of web applications such as undeleted default accounts, open access to server directories, storage of unencrypted passwords and sensitive information, improperly filled robots.txt, etc.
The most obvious way to use this data is to launch personalized attacks on users. Such attacks have a better chance of success: the distribution of malicious or phishing emails targeting the accounts at a certain bank are only effective if the message gets into the mailboxes of this particular bank’s clients.
The users’ personal data is also required to access different financial services, which explains the keen demand for this information among cybercriminals involved in Internet banking and carding scams.
Distribution of rogue antivirus programs
Almost all rogue antivirus programs have an English-language interface because their main targets are western users. The rogue AV business manipulates the users’ desire to be protected and a readiness to pay big money to keep their computers safe.
Rogue antivirus programs are distributed via partner programs.
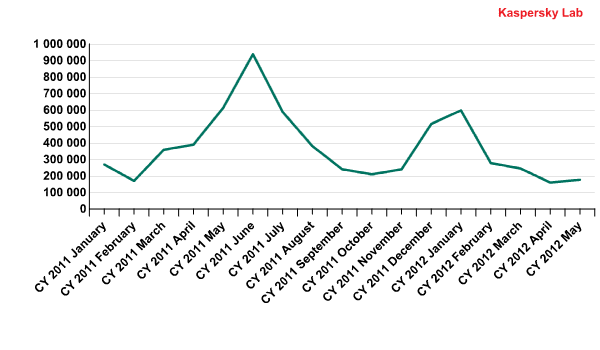
The dynamics of rogue antivirus detections in the US, Canada and Western Europe in 2011-2012
Cybercriminals started to distribute rogue antivirus programs in Europe and America early in 2011. In May they introduced rogue antiviruses for Mac OS X, also distributing them via partner programs.
In June 2011, the number of rogue antivirus programs reached its peak (Kaspersky Lab detected over 900,000 of them) before stabilizing at its former level. This coincided with Pavel Vrublevsky’s arrest. At the same time the police arrested members of two cybercriminal gangs that had been spreading rogue antivirus programs. Meanwhile, search engines became more active in removing malicious links from search results.
Although the period of between December 2011 and January 2012 was marked with yet another burst of rogue antivirus attacks, the number later returned to its initial level.
Currently, rogue antivirus programs do not bring cybercriminals huge profits, though they do provide a steady income which satisfies many “partners”. The profitability of this business can be illustrated by the fact that police believe a group of rogue antivirus distributors arrested in Latvia in June 2011 had extorted $72 million from 960,000 users in the space of three years.
Substituting search results
In most cases money-making schemes involving substitution of search results or ads are also aimed at western users. Following a user request, popular search engines are doctored to produce results where the top spots are filled with links from ad networks, rather than genuine search results. Link clicks are paid for by advertisers and the gain from each click goes to the cybercriminals who replaced the search results with adverts.
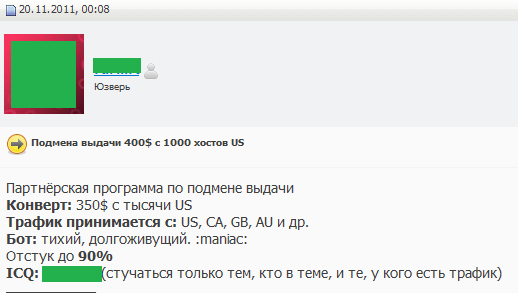
An example of a message on a Russian hacker forum offering substitution of search results for users in the US, Canada, the UK and Australia
Technically, it is performed with the help of Trojan programs that modify DNS servers/host files’ settings so that all user requests to search engines pass through the servers of the fraudsters, enabling the substitution to occur. Ultimately, the search results produce the links cybercriminals are interested in.
For example, Trojan-Downloader.OSX.Flashfake, discovered at the end of 2011, infected computers running under Mac OS X and substituted search results. The detected botnet included over 700,000 compromised machines which is almost 1% of all Mac OS X users. 84% of all infected computers were located in Western Europe and North America.
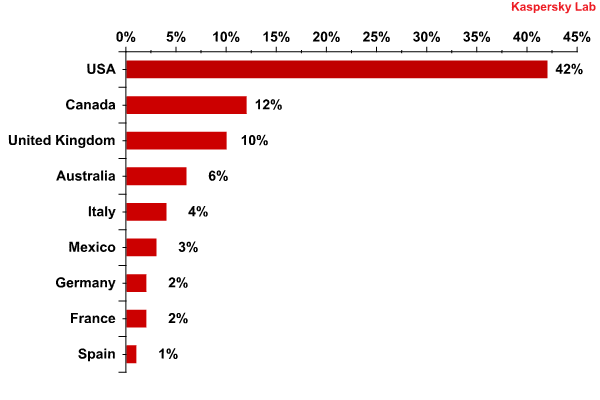
The Top 10 countries from which Trojan-Downloader.OSX.Flashfake sent requests to command centers
Another example of a Trojan with the same functionality is Backdoor.Win32.ZAccess (ZeroAccess). Its most favored targets are users in the US (27.7%) and Germany (11%).
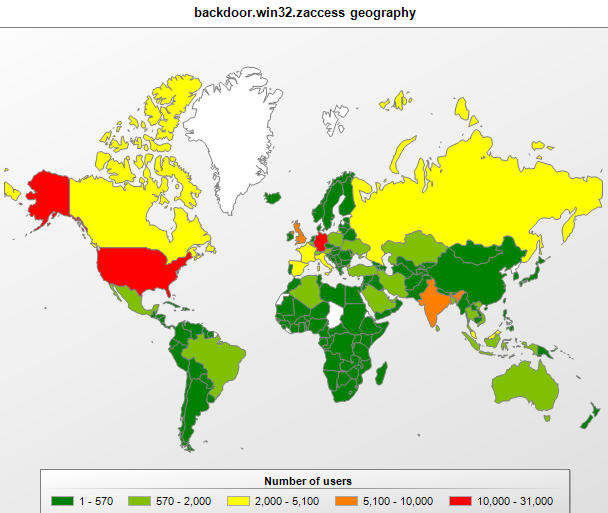
The distribution of Backdoor.Win32.ZAccess, July 2012
The US Department of Justice accused one cybercriminal group of developing a money-making scheme using search result substitution. According to the law enforcement authorities, the fraudsters appropriated $14 million over five years of illegal operations with Trojan.Win32.DnsChanger.
Extortion under cover
In western countries cybercriminals have started to actively use Trojan-Ransom programs which were almost unknown outside the former Soviet Union until fairly recently. Their operation principle is simple: having infected a computer they block all access to it modifying the system settings or opening their window on top of all other windows.
The two types of Trojan ransomeware encountered most frequently in the CIS are pornblockers, which demand money in return for closing a window which displays obscene content while blocking the computer’s normal operation, or programs which block the OS while claiming that the user has unlicensed software on the system.
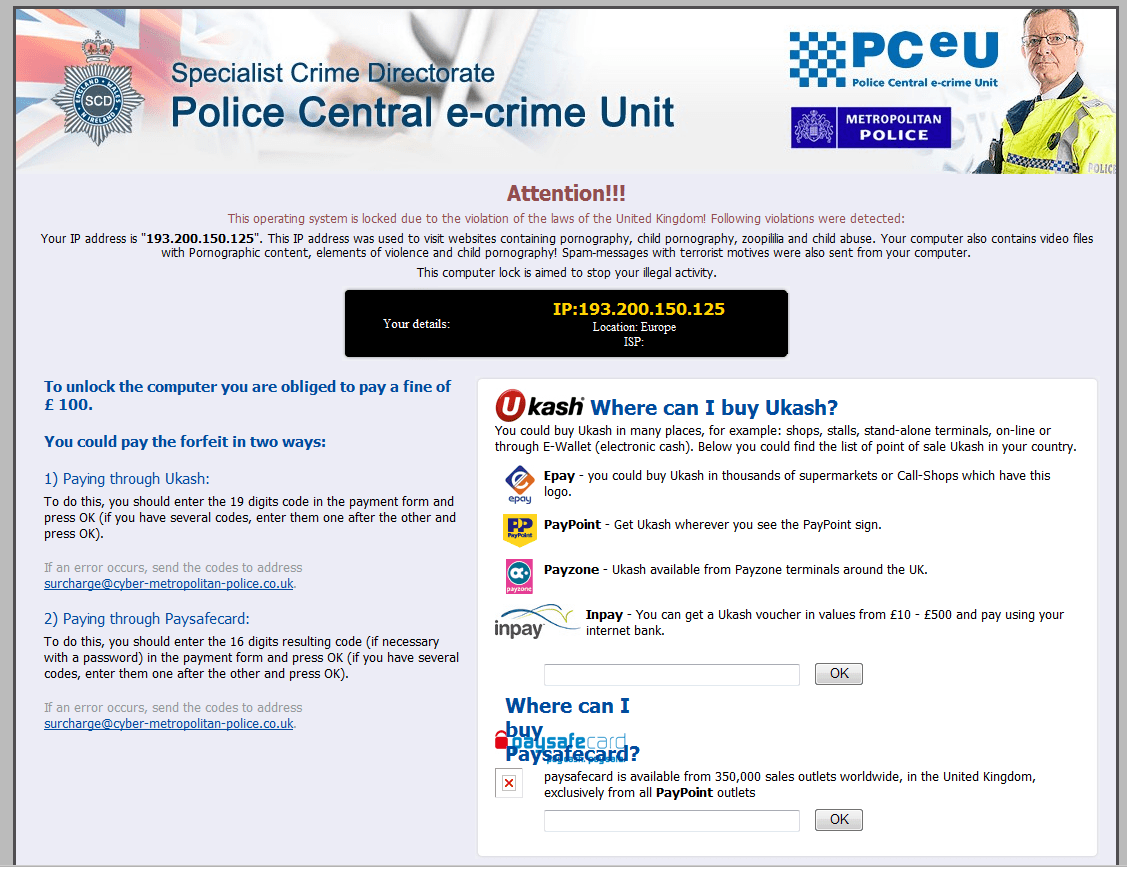
In Europe these tricks do not work. In the case of an extortion attempt, a law-abiding citizen will contact the police. Besides, most users have licensed software. Therefore, the fraudsters have created another ruse: they block the computer and allegedly on behalf of the police ask the user to pay a fine for visiting sites containing child pornography or scenes of violence against children.
The window opened by a Trojan-ransom program that attacks users in the UK
Currently we know several versions of the Trojans which use the names and symbols of the German, French, British, Swiss, Dutch, Finnish and Spanish police. Unfortunately, it is not easy to find out who receives the money because the fraudsters make transfers via the Ukash, Epay or PayPoint e-pay systems where it is not always possible to monitor transactions. Ukash was first used in a scheme involving the Trojan encoder GpCode which was created in the former USSR.
Specifics of malware distribution
In order to launch a malicious program cybercriminals must first deliver it to the user’s computer. The main channels for malware distribution all over the world are the Internet and removable media. Our research shows that programs that penetrate users’ computers via removable media, as well as classic viruses which infect files, do not work in the territories in question. The antivirus programs installed on the majority of computers simply do not allow worms and viruses to compromise enough computers to promote a self-infection process and keep it from fading away. The diagram below shows how malicious programs penetrate computers in western countries.
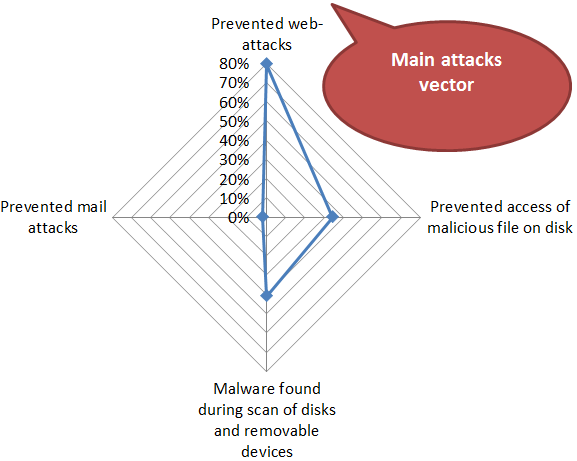
The attack vectors in Western Europe and North America, H1 2012
* The percentage of Kaspersky Lab users attacked via a specified channel out of all the attacked users of Kaspersky Lab products in the region.
The Internet is a much more effective way of attacking European and American users. According to our data, in the first half of 2012, 80% of all compromised computers were attacked while browsing the web.
The first two positions in the rating are occupied by Italy and Spain which are in the high-risk group for infection during Internet surfing (the countries where the percentage of attacks on computers exceeds 40%).
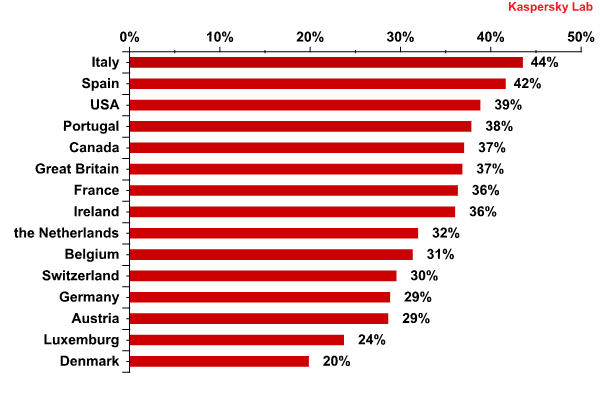
The risk of infection during Internet surfing* in North America and Western Europe in the first half of 2012
* The percentage of unique users exposed to Internet attacks out of all unique users of Kaspersky Lab products in the country.
All other countries except Denmark belong to the medium risk group (21-40%). However, in Switzerland, Germany, Austria and Luxembourg the percentage of attacked users does not exceed 30%. Denmark, the last in the list, is one of the safest countries with less than 20% of users attacked.
In order to infect computers while their users are surfing the Internet, criminals use a variety of tricks:
- Infecting legitimate sites
- Spoofing search engines
- Spreading malicious spam on social networking sites and on Twitter
Infecting legitimate websites
Infecting legitimate sites is a trick that is the most dangerous for visitors and simultaneously the most effective for cybercriminals. One way or another, the cybercriminals gain access to a popular site and introduce minor modifications to its code. When a user visits the site, their web browser goes through all the links in the code of the page and downloads their contents; at this point a string with embedded malicious code redirects the browser to a dedicated site containing an exploit, i.e. a malicious program that exploits vulnerabilities in legitimate software to intrude into the user’s computer. This attack takes place unobtrusively: as far as the user is concerned the site looks and works normally.
In such attacks, exploit packs are typically used. First these automatically search for vulnerabilities in the programs installed on the user’s computer, and then send an appropriate exploit to the computer. Thus, to achieve their goal, cybercriminals need to find just one popular application that is out of date.
Popular exploits come and go all the time: in late 2011, Java became the hackers’ favorite loophole, ahead of Adobe Acrobat Reader and FlashPlayer: four out of the five most frequently used exploits targeted Java. However, in the first half of 2012 exploits for Apple products made a comeback.
TOP 5 exploits targeting North American and Western European users
H2 2011
| Exploit name | Percentage of users attacked | Vulnerable application | |
|---|---|---|---|
| 1 | Exploit.Java.CVE-2010-4452.a | 20.6% | Oracle Java (JRE) |
| 2 | Exploit.JS.CVE-2010-4452.l | 3.4% | Oracle Java (JRE) |
| 3 | Exploit.JS.Pdfka.exr | 3.0% | Adobe PDF Reader |
| 4 | Exploit.JS.CVE-2010-4452.t | 2.9% | Oracle Java (JRE) |
| 5 | Exploit.Java.CVE-2010-0840.d | 2.6% | Oracle Java (JRE) |
H1 2012
| Exploit name | Percentage of users attacked | Vulnerable application | |
|---|---|---|---|
| 1 | Exploit.JS.Pdfka.fhh | 20.1% | Adobe PDF Reader |
| 2 | Exploit.SWF.CVE-2011-0611.bt | 10.8% | Adobe Flash Player |
| 3 | Exploit.Java.CVE-2011-3544.ct | 6.9% | Oracle Java (JRE) |
| 4 | Exploit.JS.Agent.blb | 5.6% | Oracle Java (JRE) |
| 5 | Exploit.JS.Pdfka.fhp | 4.7% | Adobe PDF Reader |
Fooling search engines
The second most popular trick is fooling search engines (Black Hat SEO). When this technique is applied, specially crafted sites containing malicious code are displayed at the top of search results.
Search engine developers ensure the relevancy of search results. Therefore, it may be too troublesome and probably unprofitable to keep malicious sites at the top of search results for routine requests. Cybercriminals have come up with a more effective method: they optimize their sites to work with hot topic search requests, i.e. to satisfy queries that are briefly popular, such as the aftermath of a celebrity death or the release of a major film, so search engine personnel do not have the time to ensure clean search results for them.
Spam
Sending spam in social networks and in twitter is a method of sending malicious links that is very popular with cybercriminals. Hot topics are a familiar feature of spam as well.
Recently, cybercriminals attacking users in Western countries have reinvented email-based spam as a means of delivering dangerous payloads. At present, email in the West is widely used to confirm registration in various services and for communication with banks, pension funds, shops, state organizations etc. So, emails containing malware are camouflaged as official notifications from such organizations. In the first half of 2012, the monthly average of messages containing malicious attachments constituted 2.8-4.3% of all email traffic, which is substantially higher than the mean values in the recent three years.
According to Kaspersky Lab’s statistics, email accounted for 2.5% of all infection sources in the first half of 2012. This statistic only included emails containing malicious attachments and scripts (emails containing dangerous links are classified as web attacks), and did not include emails that users received in web-based mail clients.
Cybercriminal infrastructure
Cybercrimes are only possible when a modern infrastructure exists – C&C servers, platforms for spreading malware, proxy servers, and botnets. All these components also have their geographic quirks.
Web hosting for malicious content
In Western Europe, the US and Canada there is a strong legal basis for combating malicious content. Despite this, 69% of all malicious content was hosted in these regions in the first half of 2012. In other words, substantially more than half of the malicious programs on the Internet are delivered from servers located in these regions.
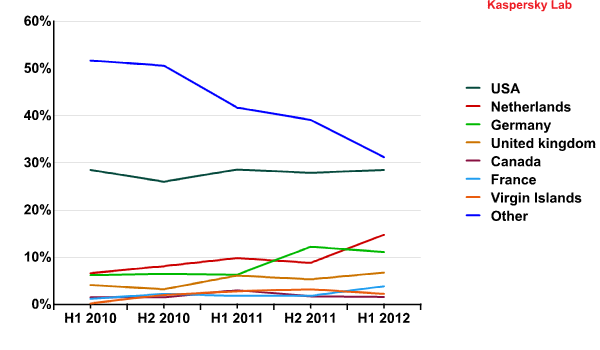
Distribution of web hosting for malicious content in 2010 – H1 2012
There are reasons for that. Firstly, the vast majority of data centers providing failsafe hosting are located in the West. Many players choose these hosting facilities for their projects. Cybercriminals hack such servers to obtain quality hosting. Another important advantage to these servers, from the cybercriminals’ viewpoint, is that they can carry out attacks from legal sites, which makes protection much more difficult. Secondly, it is anything but simple for a provider to tell a cybercriminal server from a regular one. That is why hackers do not have much difficulty using the services of legal providers. Although hosting services from Western providers are not cheap, cybercriminals can afford quality hosting services given their ample revenues.
Domain zones
Apart from physical servers, cybercriminals need domain names to distribute malware. The most popular among them are site names in the domain zones .net, .com, .info and .org. These zones account for 44.5% of repelled attacks that were launched from malicious sites on users in North America and Western Europe.
However, there are also many national domain zones from which cybercriminals actively distribute malware.
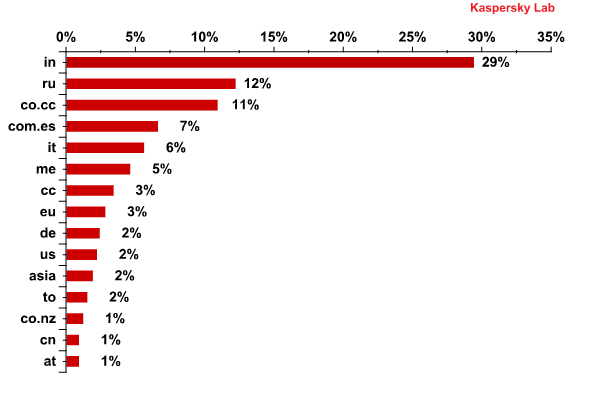
Top 15 national domain zones of malicious sites from which attacks on North American and West European users originated
The users from the US, Canada and Western Europe are typically redirected to sites located in the domain zones of India (.in), Russia (.ru) and the Cocos Islands (co.сс). Domains can be registered free of charge in the .co.cc domain; it is littered so heavily that in 2011 Google decided not to index sites located there. However, free domains still attract cybercriminals.
Positions four and five are taken respectively by the sites located in Spain’s (.com.es) and Italy’s (.it) domain zones. Montenegro’s domain zone .me elicits obvious associations among English speakers and contains a multitude of sites in English, such as love.me. Italy’s domain zone (.it) is used in a similar fashion: many companies use the domain name as the English “it” (do.it, get.it etc.). Therefore, sites in these domain zones that have been hacked or created by cybercriminals target both local and English-language users.
The domain zones of the European Union (.eu), Germany (.de) and the US (.us) are at the bottom of the top 10 national domain zones most often used by cybercriminals to launch attacks on users in Western Europe and North America.
Botnets
Botnets acting in association with partner programs are another important part of the cybercriminal infrastructure in this region.
A partner program is a scheme used by cybercriminals based on a clear-cut division of labor: there are developers of malicious programs and clients ready to pay for distributing malware; there are performers who distribute malware for money; and there are organizers of partner programs who create a site on which the above groups can communicate.
Many botnets are a huge installation base for other malicious programs. Bots are developed specifically to infect computers and download other malicious programs on to those computers, as requested by ‘clients’. Bots can mask the presence of downloaded programs in the system, and perform various extra tasks. An example of such a bot is the notorious TDSS that delivered Trojan bankers, DNS changers and rogue AV to victim computers. In 2011, 41.5% of all computers infected with TDSS were located in North America and Western Europe.
The client can choose specific countries in which to deliver their malicious program. Europe and the US are the most expensive (and, obviously, the most valuable for cybercriminals): infecting 1000 computers costs some $100-150. Infecting computers in Asia could be just a tenth of that price.
Conclusion
Most countries in North America and Western Europe are among the countries with the highest Internet penetration rates. Practically everyone there keeps their money in bank accounts, and actively uses cards associated with these accounts to pay for goods and online services.
Cybercriminals make money from users in these regions by stealing their banking data, as well as by deceiving users and extorting money. Statistics show that many computers in these regions are infected with bots which collect banking information, spread rogue antiviruses and spoof user traffic: users from these regions accounted for over 70% of the victims of the Sinowal bot attacks, over 40% of the victims of attacks by SpyEyes bots that collected banking details, and 67% of the rogue antivirus detections in the first half of 2012.
However, if we look into the cybercriminal infrastructure, we can see that there are not very many botnets in these regions that do menial jobs such as distributing spam, launching DDoS attacks, or concealing cybercriminal sites. (We will discuss in the next article where most of the computers performing these activities are located.)
In these two regions, new versions of operating systems are implemented faster than elsewhere, security programs are installed on most computers, and law enforcement agencies actively combat cybercriminals. However, even though it is comparatively difficult to penetrate computers in this part of the world, cybercriminals persevere, creating increasingly sophisticated technologies and putting them into action. The most sophisticated Trojans to date (naturally, apart from those created by secret services) operate in these regions. Unfortunately, Mac OS X users have also come under attack: during the Mac Trojan FlashFake epidemic, over 80% of infections were found in the US, Canada and Western Europe.
In these regions, cybercriminals use compromised sites and failsafe hosting services to deploy C&C servers and distribute malware. Nearly 70% of recorded malware download attempts come from servers in the US, Canada and Western Europe.
Kaspersky Lab’s research has demonstrated that the Internet is used by criminals as the main attack vector in Western countries. Revealingly, more that 40% of users’ computers in Italy and Spain were at risk of infection while surfing online in the first half of 2012, while that figure was 37% in the UK, 36% in France, and 29% in Germany. Across the Atlantic, the situation is largely the same: 39% of KSN users in the USA and 37% in Canada were attacked at least once via the Internet.
If the predicted economic crisis does materialize, it will, among other things, affect the cyber-security situation in the countries in question. The number of attacks on computers may increase, and computer security could deteriorate as people economize on upgrading computers and purchasing new versions of programs.
In the foreseeable future, mobile banking will become a new focus for cybercriminal activity. This shift will be promoted by the growing popularity of banking services among smartphone and tablet PC owners, and by the fact that many mobile devices do not have security products installed on them. Devices running under Android OS will become the most likely target for attacks.





















The geography of cybercrime: Western Europe and North America