
Introduction
VoIP (Voice over Internet Protocol) technology is developing rapidly, and Skype is the most popular VoIP product on the market. Skype allows users to reduce telephone charges significantly compared to traditional telephone networks, with no loss of connection quality. A second advantage is ease of use. Users worldwide are up and running in seconds: Simply install Skype and plug in a microphone. That done, one can talk, exchange files, text messages and so on.
However, Skype take-up has gone beyond domestic users – it is also used on corporate networks. This is not surprising when one considers how it significantly reduces the cost of long-distance and international calls and simplifies inter-office and person-to-person communications. On top of that, the utility requires no administrator privileges to set up and use. Employees can download Skype from the Internet for free and simply install it on their corporate workstations. This gives rise to a new problem: The increased Information Security (IS) risk of Skype use in the corporate environment.
The issue of Skype and network security is pressing. It is a widespread program which attracts the attention of both insiders and hackers alike. For example, internal information thieves can steal vital data using Skype. Meanwhile, there is no shortage of examples of hackers probing Skype for vulnerabilities.
| Date | Vulnerability |
| Nov. 2004 | Having uncovered a hole, a hacker was able to gain complete control over a user’s computer by means of overloading Skype’s buffer. |
| Apr. 2005 | Skype did not always erase access rights promptly. As a result, ill-intentioned people could replace original attachments with modified ones using previously established authorization. |
| Oct. 2005 | A hole was discovered which could be used to induce an overloaded buffer error on the victim’s machine resulting in access to the system. |
| Oct. 2005 | A breach in Skype allowed a denial-of-service attack on a remote computer. |
| May 2006 | A new breach facilitated the theft of files from a user’s machine. However, for this to work it was necessary to send the victim specially formed packets provoking an abnormal program termination. |
| Dec. 2006 | A worm was found to be spread across several countries, infecting workstations which had Skype installed in chat mode. |
The present research is the first Russian study into risk-free Skype use on corporate networks. It had as its object:
- To assess anxiety among IT and IS specialists regarding the use of Skype on company intranets.
- To identify additional IS threats which add to such fears.
- To pinpoint the source of these risks.
Key conclusions
- Skype is the clear leader among VoIP products. Almost half of those surveyed (46.8%) use Skype. If one removes those without any form of VoIP, then Skype takes 64.9%.
- The risk of a leak of confidential information is the greatest threat (55.6%) for a corporate network which has Skype. That is, the survey’s participants fully understand what channels for additional leakage the program presents to insiders.
- Skype itself can not seriously be blamed for these additional risks. The core problem is with the human factor (44.6%) rather than with faults in the program.
- Despite this, almost two-thirds of those surveyed (66.4%) incline to the view that the threats which attend the introduction of Skype into the corporate environment are a serious obstacle to the program’s wider acceptance. Only one-third of specialists (33.7%) felt that IS problems would not prevent the program’s wider acceptance among companies.
Research methodology and survey participant profile
This research was conducted by InfoWatch’s analysis center between 15th and 30th of January, 2007. Survey participants submitted their answers via an online form with 1242 people taking part. Statistical processing and results analysis were carried out by InfoWatch’s analysis center. Percentages are rounded off to the nearest one-tenth of one percent. In the case of some answers, the total percentages exceed 100% due to the use of multiple choice questions.
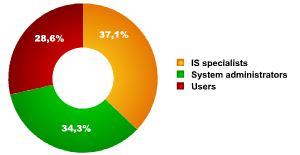
Survey participants’ IT status
The target participants for this research break down as:
- IS specialists: 37.1%
- System administrators: 34.3%
- Users: 28.6%
This means that around 71.1% of those surveyed are IT professionals.
VoIP use options
In fig. 2 we see the survey participants’ preferences regarding the VoIP programs available. That Skype is in first place (46.8%) comes as no surprise to anyone. It is the first – and some would say the most convenient – program for voice transmission over the Internet. All its competitors together only garnered a quarter of the votes (25.3%). We should mention that slightly over a third of specialists surveyed (27.9%) had no VoIP service on their intranets at all. It is probable that this is a result of the threats associated with using Skype.
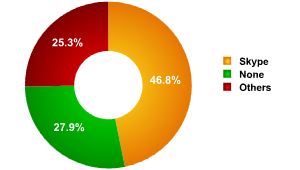
VoIP options in the corporate environment
Denis Zenkin, InfoWatch’s Marketing Director says, “Skype’s security problem is very real. Firstly, the program uses its own protocol which is not supported by traditional inter-network screens. Secondly, voice traffic is difficult for electronic systems to filter, and to do it manually is not cost-efficient. The simplest solution is to forbid the use of Skype altogether. But this is no solution since the program is convenient and beneficial.”
Skype threats
The research concentrates for the most part on identifying the risks inherent in using Skype and on their causes. It found that a clear majority of those surveyed sees a whole range of threats connected with the use of Skype (see fig. 3). A mere 5.3% of specialists felt that the use of Skype on a corporate network represented no threat whatsoever.
The greatest risk – according to 55.6% of those surveyed – is the leakage of confidential information. In other words, more than half the specialists felt that as a result of using Skype, confidential corporate information could leak out. The research concludes that the threat of a leak of confidential information is twice as likely (55.6% as opposed to 29%) than a hacker attack on intranet resources.
The center ground was occupied by the following risks:
- Unsanctioned access to information: 37.2%
- Data loss risk: 33.2%
- Threat of malignant program getting to workstations: 31.7%
- Other risks: 7.4%
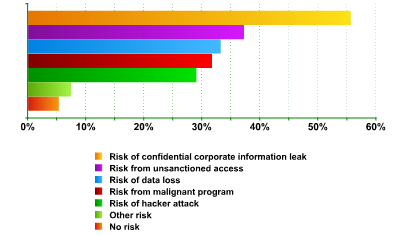
Threats from Skype
VoIP solutions – and this concerns not only Skype – clearly present companies with a whole range of IS threats. Programs for voice or video communications are sufficiently simple and accessible for insiders to use. Controlling Skype is no easy task since voice traffic is hard to filter automatically. At the same time, the use of attached files presents no difficulty to even inexperienced users. On top of this, as with the majority of software products, VoIP client programs have vulnerabilities which, theoretically, may be exploited.
What is more, in the opinion of InfoWatch’s analysis center, the risk of hacker attack is somewhat less than commonly thought. The most likely explanation is that fear has its roots in past dangers from hacker break-in. Realistically, at the present time, the threat from hackers is not so great. The threat from malware is also exaggerated. Only one instance of a Trojan penetrating a breach in Skype has been established. We remind readers that a virus cannot spread by itself but has to be physically downloaded by the user.
The source of threats
Having established that use of Skype leads to additional IS risks, the InfoWatch analysis center went on to ask its survey participants to indicate the sources of new IS threats (fig. 4). Clearly, apart from factors connected with the Skype program itself, vulnerabilities can arise due to other causes, such as faults in a given piece of software or malignant intent or lack of discipline among users, etc. The findings indicate that the majority of survey participants (44.6%) regards the workforce itself as the greatest source of threat. In other words, it is the human factor which is most likely to result in an IS incident connected with Skype.
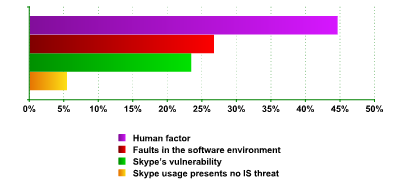
The nature of risks arising from use of Skype
The second-highest rating (26.7%) was accorded to faults in Skype’s software environment. Here we mean either vulnerabilities in the operating system, or the means of defence used and any other software application which might lead to an IS threat when run in combination with Skype. At the same time, only 23.4% of those surveyed thought that such issues were the responsibility of Skype’s developers. And only one in twelve specialists (5.4%) thought that Skype represented no IS threat whatsoever.
Thus, VoIP programs may hardly be said to be the root cause of risk. In almost half the cases, either a company’s employees themselves who did not know how to use their tools properly, or those who expressly wanted to steal information were at fault. To summarize, one may say that to stop using Skype is like trying to ban the Internet or e-mail. VoIP is beneficial and convenient, but to prevent the occurrence of the nightmare scenario – the loss of confidential information – companies need to protect their data in the same way as they protect against theft via e-mail, the Internet, printers or USB data-storage devices.
Denis Zenkin says, “Skype represents a unique opportunity to save money on long-distance calls. This means companies have an interest in the use of VoIP. To say that using Skype exposes corporate networks to unacceptable risk is not correct. But there is also no point in denying the risk altogether. However, other network applications (such as e-mail, browsers, and even the operation systems themselves) frequently present more of a threat than does Skype. To deny oneself promising and economically beneficial forms of technology is plain wrong. One needs only to use them correctly and create the right environment.”
Security and Skype
From participants’ feedback (fig. 5) we see that the factor of security is very high up the list of concerns when deciding whether to bring Skype onto a corporate network. Two-thirds of specialists surveyed (66.4%) either felt strongly or tended toward the view that IS threats make the implementation of Skype within a company more problematical. This is a significant number. In addition, as was already noted, the root cause of the problem does not lie with Skype’s technology, but rather with the its incorrect or malignant use. Naturally, any new technology which increases the risk of confidential information leaks will be given a hostile reception. This brings us to a dangerous pass. Without the implementation of advanced, modern technology companies cannot compete. But at the same time, the use of new solutions is complicated by the additional IS threats they may cause.
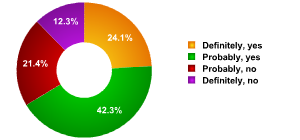
Do IS threats prevent Skype’s implementation in companies?
To return to the survey’s results, we see that 33.7% of specialists think that the additional risks do not present an obstacle to the implementation of Skype within companies, whereas 66.4% hold the opposite view. The result is that IS risks arising as a result of using Skype are a real obstacle to companies implementing VoIP programs. At the same time, it is hard to call such a view logical since it is the users themselves which are the cause of additional threats. As summary, if one takes the right steps to protect information, then it is unlikely to be leaked via Skype.
Conclusion
The research showed that there is some danger from the use of Skype in a corporate environment. The highest risk (55.6%) is of loss of confidential data. This should come as no surprise since VoIP programs are a convenient means for the misuse of internal data. Here, the threat from hackers (29.0%) and the penetration of malware onto the intranet (31.7%) was significantly overestimated by those surveyed. This was due in some part to traditional fears of computer integrity breaches and of resources “freezing up”. In reality though, the problem of hackers is not so pressing at the current moment and the number of worms and Trojans using voice-conference programs is limited.
At the same time, it is clear that, in principle, no IT instrument can be considered free of risk should it be used incorrectly. And according to the survey, it is the human factor itself which is the primary problem (44.6%) when using Skype. Besides people, the software environment also has a negative effect on security (26.7%). Only 23.4% of survey participants consider the primary cause of breach to be the VoIP client itself.
In conclusion, we can say that almost half of the survey participants think Skype makes the theft of confidential information much easier for those who wish to misuse internal data. And it is true that Skype involves a whole range of new leakage channels. Firstly, there is voice traffic. Just as with a mobile phone, one can make a call on Skype and read out a part of a document’s text. Secondly, there is file transfer. This facet is analogous to sending files via FTP, by e-mail, or ICQ. Thirdly, there is the issue of copying valuable data to the clipboard then pasting it into the chat facility which Skype supports. This facility is analogous to ICQ or Internet chat. However, of all these channels, the only relatively new one is voice traffic. All the other channels can be easily controlled by the same means used to prevent leaks via e-mail, pagers or the Internet. VoIP traffic itself, however, can hardly be said to be a dangerous leakage channel since, while an insider may relay information to an accomplice in this way over Skype, there is a limit to the amount of data which can be transferred in this way. And if a Skype user is in an open-plan office environment there should be no need to worry about leakage via voice traffic at all. Meanwhile, other leakage channels must be monitored or confidential information will soon fall into the hands of competitors or be made publicly available.
Skype and Corporate Network Security
















nworker
Any more recent studies on this now that a few years have past. Looking for pros and cons of the free version of Skype on a corp network today.