
The InfoWatch analytical center has published its results for 2006 presenting the first global survey of internal information security (IS) breaches. The goal was to analyze all leaks of confidential or personal data, cases of employee sabotage or negligence, and any other breach of internal IS which had received at least one mention in the mass media during 2006. The survey is truly global since the analysis includes all internal violations regardless of the geographical location of particular company or government structures affected by insider sabotage. Thus, all patterns and tendencies revealed in the survey can be equally applied to companies of all industries and countries.
This survey is the first global project targeted at the study of breaches of internal IS. In 2004, the InfoWatch analytical center began keeping a database of breach occurrences. Today, the database contains nearly 500 entries, 145 of which were added during 2006. This database provided the initial information for the survey.
The results of the survey naturally supplement the conclusions of the wide scale survey Internal IT Threats in Europe 2006 in which InfoWatch questioned more than 400 European organizations. However, unlike the latter project, Global Leakage Survey 2006 identifies tendencies in the development of internal threats of IS and how they happen.
Key conclusions
- For the most part, it is businesses that suffer from leaks of confidential information. According to the survey, 66% of internal breaches occurred in private companies. Moreover, businesses carry the main burden of loss caused by such leaks since a company’s competitiveness depends on its reputation, and reputation is the first thing to suffer in the event of an information leak.
- In 2006, a vast number of people suffered from information leaks. Just 150 breaches exposed 80 million people to identity theft. Many of them are now at risk of becoming victims of swindlers, losing all their savings, or having their credit history ruined forever.
- Every leak of personal information causes million-dollar losses. In addition to financial loss, a company’s reputation is ruined and hundreds of thousands of people face having their identities stolen. On average, 785,000 people suffered from every leak of private information in 2006.
- Organizations which allow their employees to use mobile devices are in a high-risk group. The use of mobile devices led to information leaks in half of all breaches (50%); meanwhile, the Internet was used as a medium for leaks in only 12% of cases.
- The main threat for a business is a lack of discipline among employees. Negligence led to the overwhelming majority of all leaks (77%) in 2006. This suggests that insiders can be found in any company.
The sources of information leaks
A survey of 145 breaches of internal IS shows that information leaks have a global character. One cannot point to any area of business or any particular geographical region where companies have rarely or never suffered from the activities of insiders. Small business and giant corporations, commercial organizations and governmental establishments all experienced cases of information leakage in 2006. Insiders managed to jeopardize the security of such strong and well-protected structures as military and special services. Again, such cases involved mobile devices and the Internet. Often, as a result, top secret information became freely available on the Internet, or ended up in the hands of journalists or foreign states.
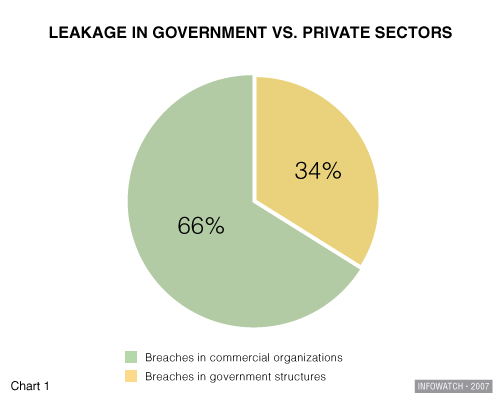
Chart 1 shows the distribution of breaches of internal IT security between government and commercial sectors. It is clear that private companies suffer from twice as many data leaks, cases of sabotage and other breaches than government structures. There are several reasons. First, the number of private companies greatly exceeds the number of government organizations. Second, it is easier for government organizations to conceal a leak when one occurs. It often happens that the controlling body is responsible for a breach of internal IS. Thus, we have the problem of lack of control over the controller. Meanwhile, some cases of information theft from government structures become public. This happens when it is simply impossible to hide the incident, or when it becomes necessary to make public example of the offender. For instance, for many years the US government kept quiet about breaches of internal IS. But today, news about information leaks and gaps in security systems is commonplace. One of the latest cases reached the news when the US Tax Inspectorate announced in November 2006 that almost 500 laptops had been stolen over the preceding 4 years.
Commercial organizations, on the other hand, do not just experience a lot of data leaks, but also suffer from the huge losses they cause. The company’s reputation and brand image are significantly damaged by such leaks. This problem is as vital for government organizations. In a competitive market, customers can easily switch to a more reliable supplier, but one has no alternative but to engage with one’s own state and its governmental ministries. Imagine that a tax inspectorate had a substantial leak of private information on companies and individuals. People would be extremely unhappy about such an incident. But nobody can stop using government services in such a case.
The nature of leaks
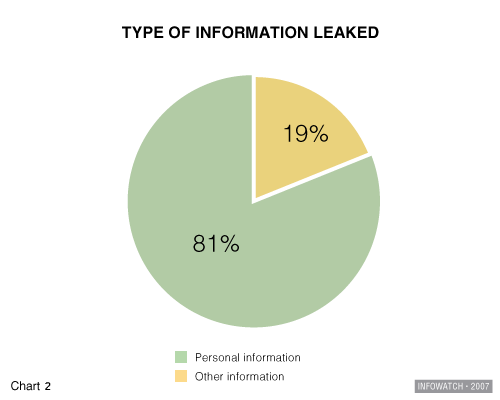
Insiders have no qualms about what confidential information they steal. However, the survey discovered that personal details are stolen several times more often than any other kind of information (see chart 2). While intellectual property, commercial and industrial secrets are unequivocally very valuable, it is private information that is most valued by insiders.
However, the occurrence of both types of leak – whether clients’ personal details or a company’s confidential information – are very dangerous for a business. The survey clearly shows the number of victims of a personal information leak is usually huge. Chart 3 compares the total number of victims of personal information leaks in 2006 and the average number of victims of each leak. It turns out, that every breach of IS which involves the leak of customers’ personal information exposes approximately 785,000 people to ID theft.
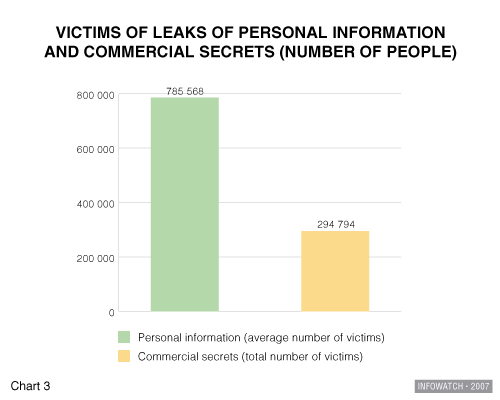
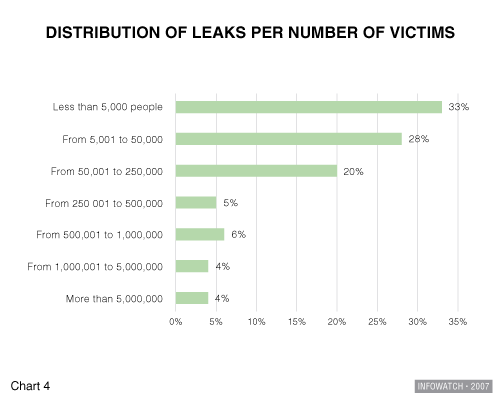
Chart 4 shows the percentage of information leaks based on the number of people affected. The survey reveals that the majority of incidents affected relatively small groups. For example, 33% of information leaks harmed groups of less than 5,000 people, and 28% harmed between 5,000 and 50,000. However, we already know that the average number of victims is 785,000 – which significantly exceeds the figures mentioned above. This is because the average number was greatly influenced by huge information leaks that occurred in 2006. An example which immediately comes to mind in this regard is the information leak from the US Department of Veterans’ Affairs which occurred in May of that year.
How information leaks occur
The most important question is: How exactly does information get leaked? In order to combat information leaks it is important to identify the channels by which data is leaked from a company. Whereas IS specialists may need time to identify such channels, insiders – in most cases – already know exactly what they need to do to steal data. That is why an effective security system must close all possible loopholes. They are as follows:
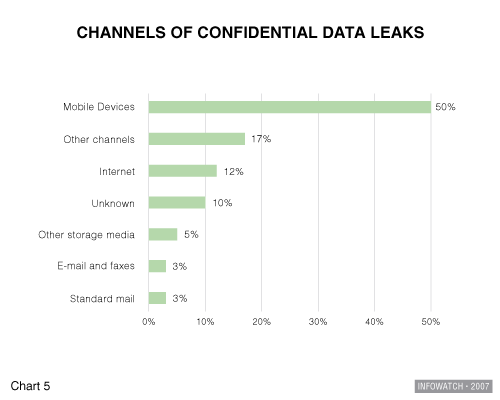
As we can see, most information leaks (50%) are perpetrated via mobile devices (laptops, PDAs, USB flash, CD, DVD, etc.). Whereas the small size of mobile devices makes them convenient, they can easily be lost or stolen. In the case of accidental loss of media, the confidential information ends up in the hands of a stranger to be used at the finder’s discretion. Whereas, internal fraudsters can easily take out information from the workplace hidden on small media.
The second most widespread channel of information leaks is the Internet (12%). The Internet is less popular than other means since it cannot be used for transferring large volumes of information quickly – something which mobile devices can do. Besides, network filtration makes it easy to identify the insider and prove that an instance of data theft took place. An additional 5% of incidents occurred through incorrectly utilized or lost storage media. E-mail/faxes and standard mail were responsible for 3% of incidents each. 17% of breaches of internal IS happened through other channels; for example, information was leaked as a result of outsourcing to an unreliable partner. In 10% of cases the channel of information leak was unknown.
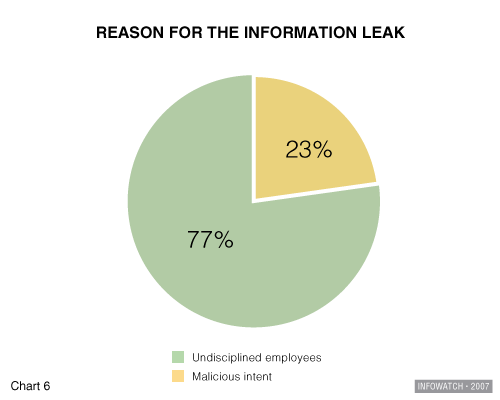
Insiders motivated by profit make up just one category of dishonest workers. The survey shows that by far the greatest number of information leaks (77%) results from the actions of undisciplined employees. The main reason for breaches of internal IS is failure to observe company policy, or basic negligence in protecting information. For instance, laptops with unencrypted data are quite often lost, despite the fact that company security policy requires all information on mobile computers be encrypted. Moreover, there are cases where people unwittingly perform insider actions, providing confidential information to fraudsters who manipulate them by using methods of social engineering. Once again these results emphasize the fact that any group of workers can contain insiders.
The biggest information leaks of the year
The five most notorious information leaks of 2006 (see table 1) make 2006 the year with the largest volume of information leaks in history. The total number of people who suffered from these five leaks was a little under 50 million.
| № | Incident | Date of the incident | Number of victims | Additional information |
| 1. | Gratis Internet Company collected the personal data of 7 million Americans via the Internet and later resold it to third parties | March 2006 | 7 million people | More details at Infowatch.com |
| 2. | Leak of personal data of US Army veterans and servicemen. | May 2006 | 28.7 million people | More details at Infowatch.com |
| 3. | A laptop with personal details of TG customers was lost by an outsourced contractor of Texas Guaranteed. | May 2006 | 1.3 million people | More details at Infowatch.com |
| 4. | A laptop of an employee of the Nationwide Building Society was stolen. It contained the personal information of 11 million society members. | August 2006 | 11 million people | More details at en.wikipedia.org |
| 5. | A mobile computer containing personal details of the company’s employees was stolen from the office of Affiliated Computer Services (ACS). | October 2006 | 1.4 million people | More details at Infowatch.com |
For example, on May 3, 2006 criminals stole a hard drive from the house of an employee of the US Department of Veteran Affairs. As a result, personal details of 26.5 million veterans and 2.2 million active-duty servicemen fell into the hands of fraudsters.
The biggest leak in Great Britain happened in August 2006. Burglars got into the house of an employee of the Nationwide Building Society and stole a laptop with the company’s clients’ personal information in unencrypted form. 11 million people face the risk of ID theft as a result. Nationwide notified the police at once, but the investigation was fruitless. Three months later the company started sending notifications to the victims.
Other leaks, while not so big, still affected millions of people. One noticeable fact is that in four out of the five biggest incidents the information disappeared from mobile computers. In those four cases, the reason was employee negligence in protecting personal information. For example, in the case of the American veterans, the employee should not have kept secret information at home. An even worse violation of IS was that in all cases the files on the mobile media were not encrypted.
Conclusion
2006 breaks all previous records in terms of the number of breaches of internal IS and the scale of total losses. Several of the biggest leaks in history happened in that year. Among them was the theft of the personal information of 28.7 million servicemen and veterans of the Army from the US Department of Veterans Affairs and also the leak of private information of about 11 million members of the British Nationwide Building Society. All this gives us grounds to dub 2006 The Year of Data Leaks.
The figures of tens of millions of victims and millions of dollars of economic loss are, in themselves, frightening. The example of such careless organizations stands to become a factor provoking other organizations to action. Regardless of all the bad news, however, there are some positive changes in the industry. Managers of companies have started realizing the importance of defending against information leaks. The popularity and massive introduction of new standards and legislative acts help in this regard. It is worth noting that in California, USA, the SC 1386 law has already been in effect for several years and has meant that the problem of leaks has received the attention that it deserves from society, authorities and the press. At the same time, a federal law with the same requirements is being worked on, though we are yet to see specific results. At the same time, there is the prospect of a new European Union directive, according to which organizations will be obliged to disclose all cases of leaks. It is possible that such a standard will appear in one or two years.
Such are the results of 2006. We hope that 2007 will prove to be a turning point in terms of internal threats. At present, the majority of companies have already started paying attention to such breaches in the protection system that allow confidential information to easily leave the organizations’ boundaries. What remains is to find the best solution and introduce the necessary protection systems.
















Global Data Leakage Survey 2006